The following sections describe the different methods to control what you can discover and monitor with the Amazon Web Services PowerPack:
Configuring AWS for Monitoring Regions with AWS Config Enabled
If your accounts have the AWS Config service enabled, then ScienceLogic recommends setting the Embed Value [%2] field in the SOAP Options section of the SOAP/XML credential you will create to "AUTO". The AWS Config service will then be used by SL1 to determine which regions and services are being used and only create the components needed. This will reduce the number of components created and will also reduce the load on the Data Collector.
NOTE: The Dynamic Applications "AWS: Account Resource Count Performance" and "AWS: Region Resource Count Performance" will only show data if the AWS Config service is enabled for those accounts/regions.
Configuring AWS for Monitoring Regions with AWS CloudWatch
If AWS config is not enabled, then ScienceLogic recommends setting the Embed Value [%2] in the SOAP Options section of the SOAP/XML credential you will create to "FILTER". This will use AWS Cloudwatch to determine which regions are reporting CloudWatch metrics and discover those regions. This will reduce the number of components created and will also reduce the load on the Data Collector.
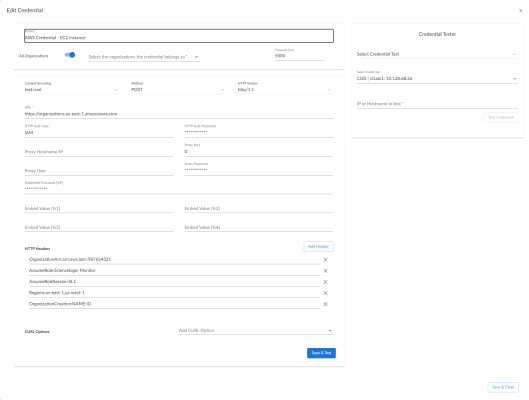
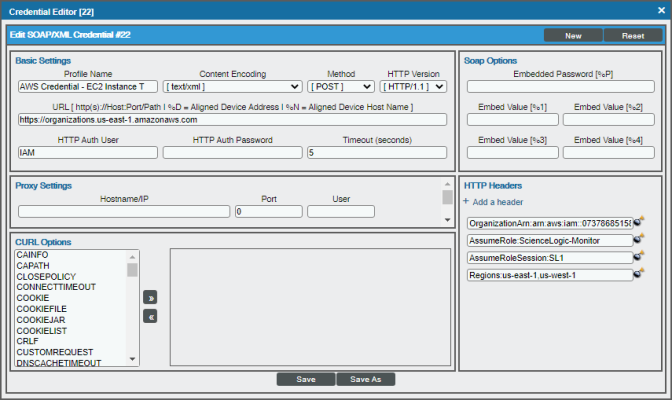
The Regions Header in the SOAP/XML Credential
The Regions header is an optional header that can be inserted into the AWS SOAP/XML credential you will create to restrict which regions are discovered. This header supports a comma-separated list of regions that will be discovered and monitored. For example, the credential below shows the header with two specific regions. In this case, only those two regions would be discovered and monitored.
NOTE: The Regions header must not be included if "FILTER" or "AUTO" are used in the Embed Value %2 field.
Using IAM Permissions to Restrict SL1 Access to Specific Regions and Services
You can use IAM policies in AWS to restrict which regions and services SL1 will monitor. To do this, you can create another IAM policy and apply that along with the SL1 monitoring policy to the applicable user or role(s).
To monitor specific regions and services, you must create a JSON policy in the AWS Management Console that uses the NotAction, Allow, and Deny policy elements to specify the regions and services you want to monitor as well as which regions and services you do not want to monitor.
You must have at least Read-Only JSON policy permissions for the regions you want to monitor. You cannot discover regions for which you do not have policy permissions. At a minimum, you must at least have permissions for the us-east-1 (Virginia) region; without permissions for this region, you cannot discover general AWS services such as CloudFront, Route53, and OpsWorks.
When discovering resources in specific regions, you should ensure that any Global services or resources you want to monitor have the necessary access permissions.
For more information about the NotAction, Allow, and Deny policy elements, see https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_notaction.html.
The following sections provide two examples of region-specific JSON policies.
Example 1: One Region
This JSON Policy will deny any service that is not in the us-east-1 region. As a result, SL1 will discover only components in the us-east-1 region.
In addition to the code below, you would need to specify the other resource permissions you want to allow in the policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyAllOutsideUSEast1",
"Effect": "Deny",
"NotAction": [
"iam:*",
"organizations:*",
"support:*",
"aws-portal:*",
"s3:ListAllMyBuckets"
],
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
}
]
}
Example 2: Multiple Regions
This JSON Policy will deny any service that is not in the us-east-1, us-west-2, and ap-northeast-1 regions. As a result, SL1 will discover only components in the us-east-1, us-west-2, and ap-northeast-1 regions.
In addition to the code below, you would need to specify the other resource permissions you want to allow in the policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyAllOutsideUSWest2USEast1APNortheast1",
"Effect": "Deny",
"NotAction": [
"iam:*",
"organizations:*",
"support:*",
"aws-portal:*",
"s3:ListAllMyBuckets"
],
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": ["us-east-1", "us-west-2", "ap-northeast-1"]
}
}
}
]
}
Configuring AWS for Monitoring Regions Using CloudWatch Namespaces
NOTE: These steps will be applied to all discovered AWS accounts on your SL1 system.
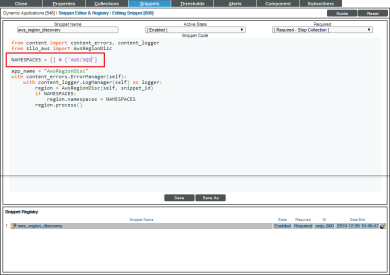
Users discovering with CloudWatch metrics can also discover regions where a specific namespace is available by editing the NAMESPACES field in the aws_region_discovery snippet in the "AWS: Region Discovery" Dynamic Application.
To edit the snippet:
- Find the "AWS: Region Discovery" Dynamic Application in the Dynamic Applications Manager page (System > Manage > Applications) and click its wrench icon (
 ).
). - Click the tab and then click the wrench icon (
 ) for the aws_regon_discovery snippet.
) for the aws_regon_discovery snippet. - Edit the NAMESPACES field to include the namespace for your region. For example:
NAMESPACES = [ 'AWS/SQS' ]
- Click .
Only regions that have services grouped in the specified namespace will be discovered. Global services will also be discovered.
For more information about namespaces, see https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/viewing_metrics_with_cloudwatch.html.