If you have created Active Directory or LDAP accounts for users and do not want to manually create accounts again in SL1, you can configure SL1 to automatically create accounts for Active Directory users or LDAP users.
Each Active Directory or LDAP user logs in to SL1 using his or her Active Directory or LDAP username and password, and SL1 automatically creates an account for that user. Each subsequent time that user logs in to SL1, SL1 will use Active Directory or LDAP to authenticate that user.
Use the following menu options to navigate the SL1 user interface:
- To view a pop-out list of menu options, click the menu icon (
 ).
). - To view a page containing all of the menu options, click the Advanced menu icon (
 ).
).
Required Tasks
To configure SL1 to automatically create accounts for existing LDAP or AD users, you must perform the following steps:
- Create one or more user policies that define account properties and privilege keys in SL1 for imported LDAP users or AD users.
- When creating the user policy, you must select LDAP/Active Directory in the Authentication Method field.
- You can create more than one user policy for imported user accounts.
- For example, suppose you want to import 100 user accounts. But suppose not all these users require access to the same parts of SL1. You could define multiple user policies, each defining a unique sets of ticket queue-memberships, organization membership, and Access Keys.
- For example, you could define a user policy for imported user accounts from the Sales department, another user policy for imported user accounts from the Support department, and yet another user policy for imported user accounts from the NOC department.
- Later, in the LDAP/AD Auth Resource Editor page (System > Settings > Authentication > Resources > create/edit LDAP/AD Resource), you specify the user policy to apply to imported user accounts.
- If you have created only one user policy for all imported accounts, you select the option for Static policy alignment and then select the single user policy.
- If you have created multiple user policies for imported user accounts, you select the option for Dynamic policy alignment and then assign a user policy to each type of imported user, based on an LDAP or AD attribute. For example, "department".
- Create an LDAP or AD credential that allows SL1 to read from (and optionally, write to) the LDAP or AD directory.
- Define the LDAP/AD Authentication Resource.
- Specify how SL1 should communicate with the LDAP or Active Directory server and exchange information with the LDAP or Active Directory server.
- Specify how SL1 should map LDAP or AD attribute values to fields in the Account Properties page.
- Specify whether SL1 should remain synced with the LDAP/AD server. If an LDAP or AD administrator makes changes to an account, SL1 can automatically retrieve those updates and apply them to the user's account in SL1 (in the Account Propertiess page) the next time the user logs in to SL1.
- In the Type field, specify one of the following:
- Static policy alignment. All user accounts imported from LDAP or AD will use a single user policy.
- Dynamic policy alignment. User accounts imported from LDAP or AD will use multiple user policies.
- If you selected Static policy alignment in the Type field, then you must select a policy in the Policy field. All users who use the Authentication Resource will use this policy.
- If you selected Dynamic policy alignment in the Type field, then you must supply values in the Attribute, Value, and Policy fields.
- In the Attribute field, specify the LDAP or AD ) attribute you want to use to differentiate imported user accounts. For example, you could select the attribute "department" and then assign different user policies to import user accounts from different departments.
- In the Value field, specify one of the possible values for the LDAP or AD attribute (specified in the Attribute field).
- In the corresponding Policy field, specify the policy you want to associate with that value. Select from a list of all user policies.
- Click the plus-sign icon (
 ) to add additional values and policies, as needed.
) to add additional values and policies, as needed. - For example, suppose you specified department in the Attribute field. Suppose that the department attribute could have two possible values: Sales or NOC.
- Suppose you created two user policies. One user policy, called Sales User Policy, includes the appropriate ticket queues and access keys for Sales personnel. Another user policy, called NOC User Policy, includes the appropriate ticket queues and access keys for NOC personnel.
- In one of the Value fields, you could specify Sales. In the corresponding Policy field, you could then specify Sales User Policy.
- You could then click on the plus-sign icon (
 ) and add another Value field and another Policy field.
) and add another Value field and another Policy field. - In the next Value field, you could specify NOC. In the corresponding Policy field, you could specify NOC User Policy.
- After defining these two Value fields and corresponding Policy fields, user accounts from the Sales department would be imported into SL1 using the Sales User Policy.
- User accounts from the NOC department would be imported into SL1 using the NOC User Policy.
- Define one or more Authentication Profiles that tell SL1 how to recognize LDAP/AD users and which Authentication Resource to use with those users.
- After completing these steps:
- Each LDAP/AD user must log in to SL1 using the LDAP or AD user name and the LDAP or AD password.
- SL1 will examine the hostname or IP address in the incoming URL request to align the user with an Authentication Profile.
- The Authentication Profile tells SL1 which Authentication Resources to use to authenticate the user.
- SL1 will use the settings and the credentials defined in the LDAP/AD Authentication Resource to query the LDAP or AD directory to authenticate each user.
- Optionally, SL1 will use the mappings and the user policy specified in the LDAP/AD Authentication Resource to create each user account. The user name will match the Search Field in the LDAP/AD Authentication Resource.
Creating a User Policy for Imported Users
User Policies allow you to define a custom set of account properties and privileges (from the Account Permissions page) and then save them as a policy.
A user policy allows you to define:
- Login State
- Authentication Method
- Ticket Queue Memberships
- Primary Organization and other Organization Memberships
- Theme
- Time Zone
- Access Keys
When you configure SL1 to automatically create user accounts for Active Directory users or LDAP users, you must define one or more user policies for those imported accounts. Because you will not be creating the accounts manually and then manually defining the account properties, SL1 uses the user policy to define the properties for the user account.
You can create more than one user policy for imported user accounts.
For example, suppose you want to import 100 user accounts from Active Directory. But suppose not all these users require access to the same parts of SL1. You could define multiple user policies, each defining a unique set of ticket queue memberships, organization membership, and Access Keys.
For example, you could define a user policy for imported user accounts from the Sales department, another user policy for imported user accounts from the Support department, and yet another user policy for imported user accounts from the NOC department.
Later, in the LDAP/AD Auth Resource Editor page (System > Settings > Authentication > Resources > create/edit LDAP/AD Resource), you specify the user policy to apply to imported user accounts. When doing this, you could tell SL1 to examine the value of the attribute "department" to determine the department associated with each user account. You could then tell SL1 to assign the sales policy to users from the sales department, the support policy to users from the support department, and so on.
To create a user policy that will configure imported user accounts:
- Go to the User Policies page (Registry > Accounts > User Policies).
- In the User Policies page, click the button. The User Policy Properties Editor page appears.
- In the User Policy Properties Editor page, supply a value in each field:
- Policy Name. Name of the user policy. Can be any combination of alphanumeric characters, up to 64 characters in length.
- Login State. Specifies whether user accounts created with the policy can log in to SL1. Choices are:
- Active. Means user accounts created with this policy are active and can log in to SL1.
- Suspended. Means that user accounts created with this policy are not active and cannot log in to SL1.
- Account Type. This drop-down list contains an entry for each standard account type. These account types affect the list of Access Keys for the user. The choices are:
- Administrator. By default, administrators are granted all permissions available in SL1. Administrators can access all tabs and pages and perform all actions and tasks.
- User. Accounts of type "user" are assigned Access Keys. Access Keys are customizable by the administrator, and grant users access to pages and tabs and permit users to view information and perform tasks in SL1. These Access Keys are defined by the system administrator from the Access Keys page (System > Manage > Access Keys).
- Password Strength, Password Expiration, Password Shadowing, Require Password Reset. These fields aren't used for LADAP/AD Authentication, so you can skip these fields.
- Authentication Method. Select LDAP/Active Directory. The user's username and password will then be authenticated by the Active Directory server or the LDAP server.
- Restrict to IP. If selected, the user will be allowed to access SL1 only from the specified IP. Specify the IP address in standard dotted-decimal notation.
- Event Console Default Display. Specifies how the Event Console page will appear by default. Choices are:
- Flat events table. Displays all events, grouped by severity. The filter-while-you-type fields and the advanced filter tool apply to the entire list of events. You can apply a single filter to events in multiple organizations.
- Group events table by organization. Events will be grouped by organization in the Event Console page. The filter-while-you-type fields and the advanced filter tool will appear for each organization grouping and will act only on the events in that organization grouping. You will not be able to apply a single filter to events in multiple organizations.
- Ticket Queue Memberships. Highlight one or more ticket queues of which users will be members.
- Primary Organization. Specifies the primary organization. This will be the default organization for user accounts created with this policy. You can select from a list of all organizations in SL1.
- Theme. Backgrounds, colors, fonts, and graphics that will appear when a user logs in. Themes are defined in the Theme Management page (System > Customize > Themes). You can select from a list of all themes in SL1.
- Time Zone. The time zone to associate with each user account created with this user policy. Dates and times in SL1 will be displayed for the selected time zone.
- Additional Organization Memberships. User accounts created with this user policy will be members of each selected organization. This allows users to view and access elements from multiple organizations. To select, highlight one or more organizations.
- Privilege Keys. The Privilege Keys pane displays a list of Access Keys that can be assigned to the user's account. Access Keys define the tabs and pages users have access to and the actions that a user may perform. These Access Keys are defined by the system administrator from the Access Keys page (System > Manage > Access Keys).
- To assign an Access Key to a user, select the checkbox. A check mark appears.
- To deny an Access Key to a user, do not select it.
- After clicking the button, all selected Access Keys will appear in red.
- Re-Apply All settings to All Policy Members. Because the Require Password Reset field is not used by LDAP/Ad Authentication, you can skip this field.
- Click the button to save your new user policy.
- Repeat these steps to create additional user policies for user accounts that will be imported from Active Directory or LDAP.
NOTE: The Login State must be set to Active before you can successfully import users from Active Directory or LDAP.
Defining a Credential for Importing Users from Active Directory or LDAP
Credentials are access profiles (username and password plus additional information) for external systems. These profiles allow SL1 to access external systems while maintaining the security of the access accounts. Users see only the name of the credential, not the username, password, and network information contained in the credential.
When you configure SL1 to automatically create user accounts for Active Directory users or LDAP users, you must define one or more credentials so SL1 can communicate with the Active Directory server or LDAP server. SL1 must communicate with the AD server or LDAP server, both to authenticate each user and to retrieve information about each user to include in each user's account.
To define a credential for accessing Active Directory or LDAP:
- Go to the Credential Management page (System > Manage > Credentials).
- In the Credential Management page, click the drop-down menu. Select Create LDAP/AD Credential.
- The Credential Editor modal page appears. In this page, you can define the new credential.
- Supply a value in each of the following fields:
- Profile Name. Name of the credential. Can be any combination of alphanumeric characters.
- LDAP Type. Specifies the type of LDAP implementation running on the directory server. Choices are LDAP or Active Directory.
- Hostname/IP. Hostname or IP address of the LDAP or Active Directory server.
- Secure. Specifies whether you are using LDAP over SSL.
- Port. Port number on the LDAP or Active Directory server to which SL1 will send requests. If you specified No in the Secure field, the default value is 389. If you specified Yes in the Secure field, the default value is 636. However, you can specify a custom port used by your organization.
- Timeout. Number of milliseconds during which the credential should continue to try to contact the LDAP or Active Directory server. After this time elapses, the credential will stop trying to contact the LDAP or Active Directory server.
- RDN (Bind DN / bind user). To configure SL1 to automatically create accounts when a user logs in with an AD name and password or LDAP name and password, you must include the %u variable in this field.
- If the LDAP or Active Directory structure does not contain all users in a single branch, in this field, you must specify a Bind DN that is allowed to search the LDAP or Active Directory for the user who is logging in. You must also supply a password for this Bind DN in the Bind Password field. SL1 will use the specified Bind DN and password to search the entire LDAP or Active Directory structure for the user who is logging in. When SL1 finds the user who is logging in, it will perform a bind using that user's Bind DN and the password supplied during login.
- If the LDAP or Active Directory structure contains all users in a single branch, you can use a variable for username and then explicitly specify the appropriate ou and dc. In many LDAP or AD configurations, each user has read-access to his/her own account. Therefore, you might find it most useful to include the %u variable in this field. When an LDAP or AD user logs in to SL1, SL1 stores the username in the %u variable. SL1 then uses the %u variable to build the bind DN, uses the bind DN to communicate with the LDAP or AD server, and then authenticates the current user.
- An example entry in the RDN field might be: uid=%u, ou=People, dc=sciencelogic, dc=com
- This creates a DN using the current ScienceLogic login name as the uid.
- You can also include the %d variable in this field. The %d variable represents the name of the LDAP domain, as specified in the LDAP Domain field.
- Bind Password. Password that allows access to the Active Directory server or the LDAP server. In most cases, when you specify a bind password in a credential, you are creating a "write" credential (that is, a credential that allows SL1 to make changes to the LDAP or AD server). Most Active Directory and LDAP configurations do not require a password for "read-only" access. To import information from the AD server or LDAP server and authenticate the imported user, SL1 requires only "read-only" access.
- LDAP Domain. If your LDAP or Active Directory configuration includes multiple domains, specify the domain components to bind to in this field. For example, you could specify:
dc=reston, dc=ScienceLogic, dc=local.
- This example would bind to the sub-domain "reston", in the domain "sciencelogic", in the domain "local".
- User Search Base. Specify the area in the AD directory or LDAP directory where users to be authenticated and automatically added to SL1 reside, using RDN notation. The search base tells SL1 which part of the external directory tree to search. For example, if you want all users in the ou called "Users", in the parent ou called "ScienceLogicHQ", in the domain ScienceLogic.local to be automatically added to SL1, you could specify the RDN that includes those ous and that specific domain.
ou=Users,ou=ScienceLogicHQ,dc=ScienceLogic, dc=local
- This example would allow SL1 to authenticate users in the ou called "Users" in the parent ou "ScienceLogicHQ", and also authenticate all users in any ou underneath "Users".
NOTE: For details on search syntax for Active Directory, see http://msdn.microsoft.com/en-us/library/aa746475(VS.85).aspx. For details on the search syntax for LDAP, see http://www.faqs.org/rfcs/rfc2254.html.
- User Search Scope. In this field, you specify whether SL1 should search only the directory specified in User Search Base or whether EM7 should search the directory specified in User Search Base and all its child branches.
- Subtree. SL1 should search the directory specified in the User Search Base field and also search all its child branches.
- One Level.SL1 should search only the directory specified in the User Search Base field.
- Click the button to save your changes to the credential.
Creating an LDAP/AD Authentication Resource
An Authentication Resource is a configuration policy that describes how SL1 should communicate with a user store. In this
In the LDAP/AD Auth Resource Editor page (System > Settings > Authentication > Resources > create/edit LDAP/AD Resource), you can:
- Specify the credential that allows SL1 to communicate with the Active Directory server or the LDAP server.
- Specify the area in the Active Directory server or LDAP server that contains the users to be imported.
- Specify the user policy to use for each imported user account. You can use multiple user polices and map policies to user accounts (using AD attributes and LDAP attributes).
- Map the values from an Active Directory account or LDAP account to corresponding values in the new account.
- Specify whether SL1 should automatically update each user's account in SL1 when the corresponding account is edited in Active Directory or LDAP.
- Specify whether SL1 should automatically update each user's account in Active Directory or LDAP when the corresponding account is edited in SL1.
Additionally, Authentication Profiles are policies that align user accounts with one or more Authentication Resource. Authentication Profiles are described later in this
To create an LDAP/AD Authentication Resource:
- Go to the Authentication Resource Manager page (System > Settings > Authentication > Resources).
- In the Authentication Resource Manager page, click the menu and then select Create LDAP/AD Resource. The LDAP/AD Auth Resource Editor page appears.
- Complete he following fields:
Basic Settings
- Name. Name of the LDAP/AD Authentication Resource.
- User Display Name. The username, email address, or preferred display name. This value is determined by the user's authentication resource settings. Select what name to display from the following options:
- disable. Uses the current default behavior, which displays the user's username in the SL1 user interface and in the logs.
- e-mail address. Displays the user's email address in the SL1 user interface and in the logs.
- user principal name. Displays the value from the UPN field on this page in the SL1 user interface and in the logs.
- UPN. "User principal name." The value that displays in the SL1 user interface and in the logs. If you select user principal name in the User Display Name field, then the value from this field displays in the SL1 user interface and in the logs. This field is blank by default for all existing (pre-11.2.1) authentication resources, but can be manually updated. For new authentication resources, enter one of the following:
- e-mail address. Displays the user's email address in the SL1 user interface and in the logs.
- user principal name. Displays the value from the UPN field on this page in the SL1 user interface and in the logs.
- Read Credential. Credential that allows SL1 to read data from an LDAP or Active Directory server. Select from a list of all LDAP and Active Directory credentials to which you have access. If this field has been set to a credential to which you do not have access, this field will display the value Restricted Credential. If you set this field to a different credential, the entry for Restricted Credential will be removed from the field; you will not be able to re-align the field with the Restricted Credential.
- Write Credential. Credential that allows SL1 to write data to an LDAP or Active Directory server. Select from a list of all LDAP and Active Directory credentials to which you have access. If this field has been set to a credential to which you do not have access, this field will display the value Restricted Credential. If you set this field to a different credential, the entry for Restricted Credential will be removed from the field; you will not be able to re-align the field with the Restricted Credential.
NOTE: Your organization membership(s) might affect the list of credentials you can see in the Read
- User Name Suffix. Optional field. Because SL1 can authenticate against multiple LDAP or Active Directory servers, there is a risk of collision among user names. In this field, you can enter a string to append to the user name in SL1, to minimize risk of collision. For example:
- You can supply the value %attribute_name%, where attribute_name is an AD or LDAP attribute. SL1 will use the value of the attribute as the username.
- You can enter one or more AD or LDAP attribute names, surrounded by percent signs (%), with text preceding it and/or text appended. SL1 will retrieve the value of the attribute and use that value plus any preceding text or appended text as the username.
- You can enter a string, with no AD or LDAP attribute specified. When you don't specify an AD or LDAP attribute in this field, SL1 will retrieve the uid attribute and append the string you specify in this field. SL1 will then use the value in the the uid plus the appended string as the username.
- Suppose we entered @ad.local in this field.
Suppose the next LDAP/AD user logs into SL1 with the username bishopbrennan.
SL1 will log in that user as bishopbrennan@ad.local.
- Suppose we entered %sn%-external in this field.
Suppose the next SSO user logs in to SL1 with their sn (last name) attribute of krilly.
SL1 will log in that user as krilly-external.
NOTE: As a best practice, use email addresses as usernames to avoid collisions.
- Search Filter. Specifies where to find the user's account information in LDAP or Active Directory. You must tell SL1 where to find the LDAP or AD attribute that maps to the user's account name in SL1.
For example, an LDAP user might use his/her uid value to log in to SL1. In the user account in SL1, that uid value will then become the user's Account Login Name.
You can use the following variables in the search filter:
- . Login name in SL1.
- %e. Email address.
- An example search filter for LDAP might be:
(&(objectClass=person)(uid=%u))
This says to search in the object class called "person" for the uid that matches the login name entered when the user logs in to SL1 and then stored in the variable %u.
- An example search filter for Active Directory might be:
(samaccountname=%u)
This says to search for the samaccountname attribute that matches the login name (entered when the user logs in to SL1 and then store in the variable %u).
- For more information on the syntax of LDAP and AD search filters, see RFC 4515.
- Sync directory values to EM7 on login. If an LDAP or AD administrator makes changes to an LDAP or AD account, SL1 will automatically retrieve those updates and apply them to the user's account in SL1 (in the Account Properties page) the next time the user logs in to SL1.
- Sync EM7 values to directory on save. If an administrator made changes to the user account in SL1, SL1 will automatically write those changes to the user's account in LDAP or Active Directory. This option requires a write credential.
Attribute Mapping
If you have configured SL1 to automatically create accounts in SL1 for LDAP or AD users, these fields specify the LDAP or AD attribute value that will be automatically inserted into each field in each user's Account Properties page.
SL1 automatically populates as many of these fields as possible. You can edit or delete the default values provided by SL1.
For example, SL1 automatically inserts the value of the LDAP/AD attribute "sn" (surname) into the Last Name field in each user's Account Properties page (Registry > Devices > Device Manager.
NOTE: SL1 requires that the LDAP or AD attribute name that you specify in each field uses all lowercase characters.
- First Name. Specifies the LDAP or AD attribute value that will be automatically inserted into the First Name field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "givenname" into this field.
- Last Name. Specifies the LDAP or AD attribute value that will be automatically inserted into the Last Name field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "sn" into this field.
- Title. Specifies the LDAP or AD attribute value that will be automatically inserted into the Title field in each user's Account Properties page.
- Department. Specifies the LDAP or AD attribute value that will be automatically inserted into the Department field in each user's Account Properties page.
- Phone. Specifies the LDAP or AD attribute value that will be automatically inserted into the Phone field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "telephonenumber" into this field.
- Fax. Specifies the LDAP or AD attribute value that will be automatically inserted into the Fax field in each user's Account Properties page.
- Mobile. Specifies the LDAP or AD attribute value that will be automatically inserted into the Mobile field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "mobile" into this field.
- Pager. Specifies the LDAP or AD attribute value that will be automatically inserted into the Pager field in each user's Account Properties page.
- MFA User. Specifies the LDAP or AD attribute value that will be automatically inserted into the MFA User field in each user's Account Permissions page.
NOTE: For details on configuring multi-factor authentication, see
- Primary Email. Specifies the LDAP or AD attribute value that will be automatically inserted into the Primary Email field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "mail" into this field.
- Secondary Email. Specifies the LDAP or AD attribute value that will be automatically inserted into the Secondary Email field in each user's Account Properties page.
- Street Address. Specifies the LDAP or AD attribute value that will be automatically inserted into the Street Address field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "streetaddress" into this field.
- Suite/Building. Specifies the LDAP or AD attribute value that will be automatically inserted into the Suite/Building field in each user's Account Properties page.
- City. Specifies the LDAP or AD attribute value that will be automatically inserted into the City field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "l" into this field.
- State. Specifies the LDAP or AD attribute value that will be automatically inserted into the State field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "st" into this field.
- Postal Code. Specifies the LDAP or AD attribute value that will be automatically inserted into the Postal Code field in each user's Account Properties page. By default, SL1 inserts the value of the LDAP/AD attribute "postalcode" into this field.
- Country. Specifies the LDAP or AD attribute value that will be automatically inserted into the Country field in each user's Account Properties page.
- Organization. Specifies the LDAP or AD attribute value that will be used to automatically define the Primary Organization field in each user's Account Permissions page. You must also specify one of the following:
- directory attribute specifies organization ID. The attribute in the Organization field specifies an organization ID.
- directory attribute specifies organization name. The attribute in the Organization field specifies an organization name.
- directory attribute specifies organization CRM ID. The attribute in the Organization field specifies the CRM ID of an organization.
NOTE: To use Attribute Mapping for Organization, your LDAP/AD schema must include an attribute that maps to Organization names in SL1, Organization IDs in SL1, or Organization CRM IDs in SL1.
NOTE: When you create a new LDAP/AD user, you must align a user policy with that user. If the aligned user policy specifies an organization for the user, the value from the user policy will overwrite the value from Attribute Mapping.
User Policy Alignment
- Type. Specifies whether SL1 should automatically create accounts in SL1 for each LDAP or Active Directory user in the search base (which is specified in the credential), whether SL1 should simply use LDAP or Active Directory to authenticate one or more users, or whether SL1 will refuse to authenticate specific users. Choices are:
- Do not authenticate new users from directory. Only those users who have an account already created in SL1 can log in to SL1. However, if one or more users' Account Permissions page specifies LDAP /Active Directory in the Authentication Method field, SL1 will authenticate those users with either LDAP or Active Directory, using the settings and credentials specified in this page.
- Static policy alignment. If an LDAP or AD user logs in to SL1 using the LDAP or AD attribute specified in the Search Filter field, SL1 will automatically create an account for that user. SL1 will use one user policy (specified in the Policy field) to create all imported LDAP or AD user accounts. SL1 will also use the settings and credentials specified in this page when creating the account.
- Dynamic policy alignment. If an LDAP or AD user logs in to SL1 using the LDAP or AD attribute specified in the Search Filter field, SL1 will automatically create an account for that user. SL1 will choose from among multiple user policies to create imported LDAP or AD user accounts. For example, some imported user accounts might use "user policy A"; other imported user accounts might use "user policy B". SL1 will also use the settings and credentials specified in this page when creating the account.
NOTE: If you have dynamic policy alignment configured, each time a user logs in using an account that is aligned with a user policy that uses LDAP/AD authentication, SL1 will perform the attribute match and reassign a user policy if the attribute has changed.
If you selected Static policy alignment in the Type field, you must supply a value in the Policy field:
- Policy. Specifies the user policy to use to automatically create an account in SL1 for each LDAP or AD user. Select from a list of all user policies that specify LDAP /Active Directory in the Authentication Method field.
If you selected Dynamic policy alignment in the Type field, you must supply values in the Attribute, Value, and Policy fields.
- In the Attribute field, specify the LDAP or AD attribute you want to use to differentiate imported user accounts. For example, you could select the attribute "department" and then assign different user policies to import user accounts from different departments. You can also use this field to exclude LDAP or AD accounts for which you do not want to create an account in SL1.
- In the Value field, specify one of the possible LDAP or AD attribute values (specified in the Attribute field). SL1 will compare the value in this field to the retrieved value for the Attribute.
- In the corresponding Policy field, choose one of the following:
- Do Not Authenticate. If the retrieved value of the specified Attribute matches the value in the Value field, SL1 will not authenticate the user. This setting applies to new users for whom LDAP or Active Directory would have to create a new account in SL1 and for users who already have an account in SL1.
- the policy you want to associate with that value. Select from a list of all user policies that specify LDAP /Active Directory in the Authentication Method field.
- For example, suppose you specified "department" in the Attribute field. Suppose that the "department" attribute could have two possible values: "Sales" or "NOC".
- Suppose you created two user policies. One user policy, called "Sales User Policy", includes the appropriate ticket queues and access keys for Sales personnel. Another user policy, called "NOC User Policy", includes the appropriate ticket queues and access keys for NOC personnel.
- In one of the Value fields, you could specify "Sales". In the corresponding Policy field, you could then specify "Sales User Policy".
- In the next Value field, you could specify "NOC". In the corresponding Policy field, you could specify "NOC User Policy.
- After defining these two Value fields and corresponding Policy fields, user accounts from the Sales department would be imported into SL1 using the Sales User Policy.
- User accounts from the NOC department would be imported into SL1 using the NOC User Policy.
- You could also specify status in the Attribute field. Suppose that the status attribute could have two possible values: active or terminated.
- Whenever an LDAP or AD entry for a user included the status attribute with the value terminated, SL1 could apply the policy Do Not authenticate.
- To define additional Value and Policy fields, click the green plus-sign icon (
 ).
).
NOTE: If a user matches multiple Value entries, SL1 will find the first match and then stop searching. Therefore, it is important to define the Value/Policy field pairs in the order in which you want them applied to users.
- Click the button to save your changes to the new Authentication Resource.
Creating an Authentication Profile
An Authentication Profile is a policy for user authentication. Authentication Profiles align user accounts with one or more Authentication Resources.
- Alignment by pattern matching. SL1 uses the URL or IP address that a user enters in a browser to connect to an Administration Portal, Database Server, or All-In-One Appliance. If the URL or IP address matches the criteria specified in an authentication profile, SL1 will automatically use the matching profile to perform user authentication.
- Credential Source. Specifies from where SL1 should extract the user name and password or certificate to be authenticated. These credentials are passed to SL1 via HTTP. SL1 then passes the credentials to each Authentication Resource specified in the Authentication Profile. The Authentication Resources authenticate the credentials with user stores.
- Authentication Resource. Specifies the connector to use to communicate with the user store, the credential to use to connect to the user store (if applicable), and the URLs to examine during authentication. Also maps attributes from the user's account in the user store to fields in the SL1 user account.
- Multi-factor Resource. Specifies the connector to use to communicate with the multi-factor endpoint. A Multi-factor Resource specifies the hostname or IP address of the Authentication Agent, the access key for communicating with the endpoint, and the URL of the RSA REST endpoint.
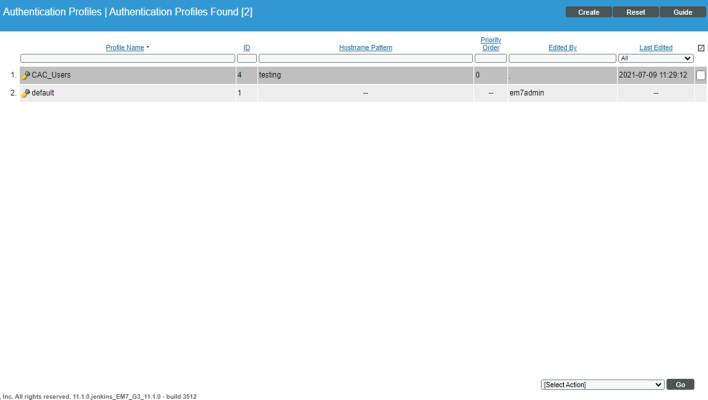
To create a new authentication profile:
- Go to the Authentication Profiles page (System > Settings > Authentication > Profiles).
- Click the button. The Authentication Profile Editor modal appears.
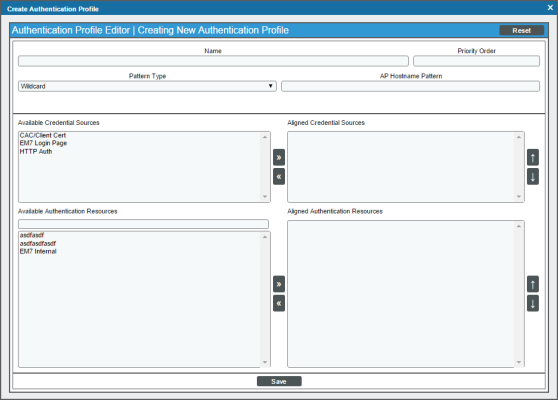
- Enter values in the following fields:
- Name. Name of the authentication profile.
- Priority Order. If your SL1 System includes multiple authentication profiles, SL1 evaluates the authentication profiles in ascending priority order. SL1 will apply the authentication profile that matches the hostname or IP in the current URL AND has the lowest value in the Priority Order field.
- Pattern Type. Specifies how SL1 will evaluate the value in the AP Hostname Pattern field. Choices are:
- Wildcard. SL1 will perform a text match, with wildcard characters (asterisks).
- Regex. SL1 will use regular expressions to compare the AP Hostname Pattern to the current session information.
- AP Hostname Pattern. This field is used to match the URL or IP address that a user enters in a browser to connect to an Administration Portal, Database Server, or All-In-One Appliance. If the URL or IP address matches the value in this field, SL1 applies the authentication profile to the user for the current session.
- For example, if you specify "*" (asterisk), any IP address or URL will match. SL1 will then apply this authentication profile to every session on an Administration Portal, Database Server, or All-In-One Appliance.
- If you enter "192.168.38.235", SL1 will apply the authentication profile to each session on an Administration Portal, Database Server, or All-In-One Appliance where the user enters "192.168.38.235" into the browser.
- If you enter "*.sciencelogic.local", SL1 will apply the authentication profile to each session on an Administration Portal, Database Server, or All-In-One Appliance where the user enters a URL ending with ".sciencelogic.local" into the browser.
- Available Credential Sources. This field tells SL1 how to retrieve the user's credentials from the HTTP request to SL1. To align a credential source with the authentication profile, highlight the credential source and click the right-arrow button. You can select zero, one, or multiple credential sources for the authentication profile. Initially, this pane displays a list of all the credential sources:
For CAC authentication, align the CAC/Client Cert credential source. If this is your primary method of logging in to SL1, align CAC/Client Cert as the number one credential source. ScienceLogic recommends having EM7 Login Page aligned, as well, for administrator or maintenance access.
- CAC/Client Cert. SL1 will retrieve a certificate from the HTTP request.
- EM7 Login Page. SL1 will retrieve a user name and password from the ScienceLogic login page fields.
- HTTP Auth. SL1 will retrieve a user name and password from the HTTP request.
- Aligned Credentials Sources. This field displays the list of credential sources that have been aligned with the authentication profile. The authentication profile will examine each credential source in the order in which it appears in this list. When the authentication profile find the user's credential, the authentication profile stops examining any remaining credential sources in the list.
- Available Authentication Resources. This field tells SL1 which authentication resources to use to authenticate the retrieved credentials. To align an authentication resource with the authentication profile, highlight the authentication resource and click the right-arrow button. You must select at least one authentication resource (but can select more than one). For details on creating an authentication resource, see the section on Authentication Resources.
- Aligned Authentication Resources. This field displays the list of authentication resources that have been aligned with the authentication profile. The authentication profile will examine each authentication resource in the order in which it appears in this list. When an authentication resource successfully authenticates the user, the authentication profile stops executing any remaining authentication resources in the list.
If you are using Single Sign-On (SSO) authentication, the Available Credential Sources field is ignored. You do not have to align a credential source because credentials are submitted directly to an Identity Provider (IdP) instead of SL1.
- Click the button to save your changes to the new authentication profile.