This
Use the following menu options to navigate the Skylar One user interface:
- To view a pop-out list of menu options, click the menu icon (
 ).
). - To view a page containing all of the menu options, click the Advanced menu icon (
 ).
).
Using Dynamic Component Mapping and Relationships with AWS
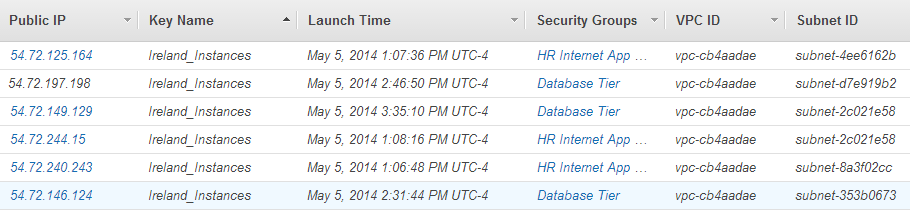
The AWS Management Console does not always make it clear where the user is deploying instances . For example, Subnets and VPCs are often identified only by hexadecimal identifiers, e.g. "subnet-4ee6162b", instead of human-readable names:
When configuring a large number of devices, it is possible to accidentally provision an instance into the correct VPC but the incorrect subnet. It's also possible to provision the instance into the incorrect VPC.
Validating VPC Subnets Using Custom Views
Users can create custom maps by defining a device group. When the map for that device group is viewed, Skylar One then automatically includes all the relationships between the included devices. The view in this section includes all Amazon EC2 Instances, VPC Instances, and VPC Subnets in a specific organization:
-
Go to the tab and expand the My Customized Maps section of the left NavBar. Select the device group that you want to view.
-
To see the relations between EC2 instances and subnets, but not the relationships between ECS instances and VPCs, click the filter button.
-
In the Link Types section, deselect the checkbox for AWS VPC/EC2.
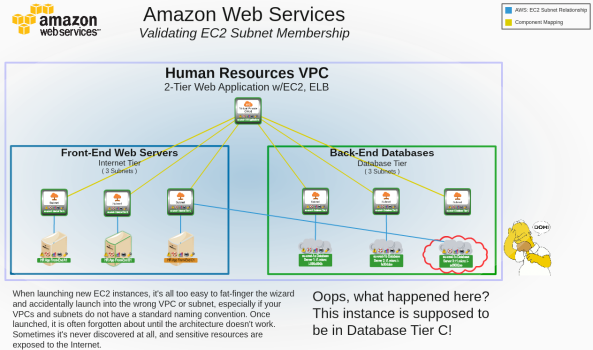
In this example, the devices in the device group represent a two-tier application with three web servers and three database servers. The devices are in three availability zones in the Ireland AWS region.
The relationships, which were automatically discovered, are automatically included on the map:
In this example, the circled EC2 instance was accidentally launched into the wrong subnet. It was supposed to be launched into the "Database Tier 3" subnet, but it was launched into "Internet Tier 3" instead, exposing the database server.