The following sections describe the different methods of discovery that can be used with the "Amazon Web Services" PowerPack:
Discovering Amazon Web Services
Skylar One currently supports the following methods to discover your AWS accounts:
- Manual Discovery. Requires the creation of a virtual device, manual alignment of Dynamic Applications, and an IAM key. This process needs to be repeated for each AWS account.
- Automated Discovery using Assume Role with single IAM key. Provides an automated mechanism to discover all your AWS accounts within an organization using a single IAM key. This is the recommended method of discovery when your Data Collector is not an EC2 instance.
- Automated Discovery when the Data Collector runs as an EC2 instance. Provides a fully automated mechanism to discover all your AWS accounts when your Data Collectors are running as EC2 instances. Skylar One does not need any AWS credentials in this case. This is the recommended approach when your Data Collectors are EC2 instances.
- AWS Guided Discovery. Uses guided workflows in Skylar One. This method is recommended when you want to use a separate IAM key for each AWS account. The guided worfklows provide a more user-friendly version of the manual process. Choose from the following workflows:
- AWS EC2
- AWS IAM
- AWS Assume Role
NOTE: These Guided Discovery Workflows are available in Skylar One version 11.2.0 and later. A basic Guided Discovery Workflow is available in earlier versions of Skylar One.
Before determining your method of discovery, it is recommended to define the minimum permissions policy in AWS. This policy defines the minimum permissions needed to monitor all AWS services and is needed regardless of which of the above methods is used.
You can discover a maximum of 10 accounts with the following requirements on the Data Collector:
- 8 cores
- 32 GB of RAM
- 100 GB of HDD
Preparing your AWS Organization or AWS Account for Discovery
You can discover your AWS organization or individually configured AWS accounts using the "Amazon Web Services" PowerPack. There are two options available for configuration of AWS Organization Discovery :
- IAM User
- EC2 "Credential-less" for Skylar One platforms hosted within Amazon Web Services.
Individual accounts can only be configured for discovery via the IAM User option.
Organization Account
The "Amazon Web Services" PowerPack supports the discovery of individually configured organizations. Each variation leverages the AssumeRole capability to provide monitoring insight to individual accounts. To complete this configuration, you will need to configure on IAM User and corresponding IAM Role within each account you want to monitor. For Skylar One systems hosted in Amazon Web Services/EC2, you do not need an IAM User. For more information about AWS/EC2 configuration, see the EC2 Credential-less section.
IAM User
Before you configure an IAM User for Organization Discovery, you must assign the following "Delegated Administrator" Policy to your organization.
- Replace the <Account ID> with an account ID from withing your AWS organization.
ScienceLogic recommends that you do not use your Management Account ID for this step.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement",
"Effect": "Allow",
"Principal": {
"AWS": "<Account_ID>
},
"Action": [
"organizations:ListAccounts",
"organizations:DescribeAccount",
"organizations:DescribeOrganization"
],
"Resource": "*"
}
]
}
- After you have replaced your <Account ID>, you can create the IAM User (e.g. Skylar One-Service-User) within the account you just delegated the above actions.
ScienceLogic does not recommend that this IAM User have access to the AWS Management Console.
- When prompted to add the permissions, select "Attach policies directly".Each account within the organization that you want to monitor should be represented and ScienceLogic does not recommend using Wildcards or non-explicit configurations. Follow the prompts to create a policy with JSON similar to the example below.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"organizations:ListAccounts",
"organizations:DescribeOrganization",
"organizations:DescribeAccount"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": [
"arn:aws:iam::<Account ID 1>:role/Sciencelogic-Monitor",
"arn:aws:iam::<Account ID 2>:role/Sciencelogic-Monitor",
"arn:aws:iam::<Account ID 3>:role/Sciencelogic-Monitor"
]
}
]
}
- When you are finished navigating the IAM User creation wizard, you should see your newly created user appear on the IAM User list. Select your user and then select "Security Credentials" and then "Access Key" to customize the role for the new IAM User.
- Create a role called ScienceLogic-Monitor, which is case sensitive, for each account that you specified in Step 1.
- Assign the following policy to each role:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"acm-pca:ListCertificateAuthorities",
"airflow:ListEnvironments",
"amplify:ListApps",
"apigateway:GET",
"appflow:ListFlows",
"apprunner:ListServices",
"appstream:DescribeFleets",
"appsync:ListGraphqlApis",
"athena:ListDatabases",
"athena:ListDataCatalogs",
"athena:ListWorkGroups",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"backup:ListBackupPlans",
"cassandra:Select",
"chime:ListAccounts",
"chime:ListVoiceConnectors",
"cloudfront:GetDistribution",
"cloudfront:GetStreamingDistribution",
"cloudfront:ListDistributions",
"cloudfront:ListInvalidations",
"cloudfront:ListStreamingDistributions",
"cloudhsm:DescribeClusters",
"cloudsearch:DescribeDomains",
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarmHistory",
"cloudwatch:DescribeAlarms",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListMetricStreams",
"codebuild:ListProjects",
"codeguru-profiler:ListProfilingGroups",
"codeguru-reviewer:ListRepositoryAssociations",
"cognito-identity:ListIdentityPools",
"config:GetDiscoveredResourceCounts",
"connect:ListInstances",
"databrew:ListProjects",
"dataexchange:ListDataSets",
"datasync:ListAgents",
"datapipeline:ListPipelines",
"dax:DescribeClusters",
"devops-guru:ListMonitoredResources",
"directconnect:DescribeConnections",
"directconnect:DescribeTags",
"directconnect:DescribeVirtualInterfaces",
"dlm:GetLifecyclePolicies",
"dms:DescribeReplicationInstances",
"dynamodb:DescribeTable",
"dynamodb:ListTables",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeClientVpnEndpoints",
"ec2:DescribeFleets",
"ec2:DescribeElasticGpus",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeNatGateways",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshots",
"ec2:DescribeSpotFleetRequests",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ecs:DescribeClusters",
"ecs:DescribeContainerInstances",
"ecs:DescribeServices",
"ecs:DescribeTaskDefinition",
"ecs:DescribeTasks",
"ecs:ListClusters",
"ecs:ListContainerInstances",
"ecs:ListServices",
"ecs:ListTagsForResource",
"ecs:ListTasks",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticache:DescribeCacheClusters",
"elasticache:ListTagsForResource",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironmentHealth",
"elasticbeanstalk:DescribeEnvironmentResources",
"elasticbeanstalk:DescribeEnvironments",
"elasticbeanstalk:DescribeInstancesHealth",
"elasticfilesystem:DescribeFileSystems",
"elastic-inference:DescribeAccelerators",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticmapreduce:ListClusters",
"elasticmapreduce:ListInstances",
"elastictranscoder:ListPipelines",
"es:ListDomainNames",
"events:ListRules",
"finspace:ListEnvironments",
"firehose:ListDeliveryStreams",
"forecast:ListDatasetGroups",
"frauddetector:GetDetectors",
"fsx:DescribeFileSystems",
"gamelift:ListFleets",
"geo:ListMaps",
"glacier:GetVaultNotifications",
"glacier:ListTagsForVault",
"glacier:ListVaults",
"glue:ListJobs",
"greengrass:ListCoreDevices",
"groundstation:ListSatellites",
"guardduty:ListDetectors",
"healthlake:ListFHIRDatastores",
"iam:GetAccountAuthorizationDetails",
"iam:GetUser",
"inspector2:ListUsageTotals",
"iot:DescribeThing",
"iot:ListScheduledAudits",
"iot:ListSecurityProfiles",
"iot:ListTagsForResource",
"iot:ListThings",
"iotanalytics:ListDatastores",
"iotevents:ListDetectorModels",
"iotsitewise:ListAssetModels",
"iottwinmaker:ListWorkspaces",
"ivs:ListChannels",
"ivschat:ListRooms",
"kafka:ListClusters",
"kendra:ListIndices",
"kinesis:ListStreams",
"kinesisvideo:ListStreams",
"kms:DescribeKey",
"kms:ListAliases",
"kms:ListKeys",
"kms:ListResourceTags",
"lakeformation:ListResources",
"lambda:GetAccountSettings",
"lambda:GetPolicy",
"lambda:ListAliases",
"lambda:ListEventSourceMappings",
"lambda:ListFunctions",
"lambda:ListTags",
"lex:ListBots",
"lightsail:GetBundles",
"lightsail:GetInstanceMetricData",
"lightsail:GetInstances",
"lightsail:GetRegions",
"logs:DescribeLogGroups",
"lookoutequipment:ListDatasets",
"lookoutmetrics:ListAnomalyDetectors",
"lookoutvision:ListProjects",
"mediaconnect:ListFlows",
"mediaconvert:ListJobs",
"mediaconvert:ListQueues",
"medialive:ListChannels",
"mediapackage-vod:ListPackagingConfigurations",
"mediapackage-vod:ListPackagingGroups",
"mediapackage:ListChannels",
"mediatailor:ListPlaybackConfigurations",
"mq:ListBrokers",
"network-firewall:ListFirewalls",
"nimble:ListStudios",
"opsworks:DescribeInstances",
"opsworks:DescribeStacks",
"panorama:ListDevices",
"personalize:ListDatasets",
"polly:ListLexicons",
"qldb:ListLedgers",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBSubnetGroups",
"rds:ListTagsForResource",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"rekognition:DescribeProjects",
"robomaker:ListSimulationJobs",
"route53:GetHostedZone",
"route53:ListHealthChecks",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"rum:ListAppMonitors",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketTagging",
"s3:GetBucketWebsite",
"s3:GetObject",
"s3:ListAllMyBuckets",
"s3:ListBucket",
"sagemaker:ListDomains",
"states:ListStateMachines",
"secretsmanager:ListSecrets",
"ses:ListIdentities",
"servicecatalog:SearchProductsAsAdmin",
"shield:DescribeEmergencyContactSettings",
"shield:GetSubscriptionState",
"shield:ListAttacks",
"shield:ListProtections",
"sns:ListSubscriptions",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"ssm:GetInventory",
"ssm:GetParameters",
"storagegateway:ListGateways",
"storagegateway:ListVolumes",
"sts:GetCallerIdentity",
"swf:ListDomains",
"synthetics:DescribeCanaries",
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues",
"timestream:ListDatabases",
"transcribe:ListTranscriptionJobs",
"transfer:ListServers",
"translate:ListTextTranslationJobs",
"waf-regional:GetRateBasedRule",
"waf-regional:GetRule",
"waf-regional:GetRuleGroup",
"waf-regional:GetWebACL",
"waf-regional:ListResourcesForWebACL",
"waf-regional:ListWebACLs",
"waf:GetRateBasedRule",
"waf:GetRule",
"waf:GetRuleGroup",
"waf:GetWebACL",
"waf:ListWebACLs",
"workmail:ListOrganizations",
"workspaces-web:ListPortals",
"workspaces:DescribeWorkspaceDirectories",
"workspaces:DescribeWorkspaces"
],
"Resource": "*"
}
]
}
- Update the trust policy so that the IAM User you created is able to assume this role.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::<Account ID>:user/Skylar One-Service-User"
]
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
You should now be able to discover your organization within ScienceLogic.
EC2 "Credential-less"
The following configuration process is designed for ScienceLogic systems (e.g. database servers, data collectors) that are hosted within Amazon Web Services in EC2. As with the IAM User approach, you must assign the following "Delegated Administrator" Policy to your organization.
- Replace the <Account ID> with an account ID from withing your AWS organization.
ScienceLogic recommends that you do not use your Management Account ID for this step.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement",
"Effect": "Allow",
"Principal": {
"AWS": "<Account_ID>
},
"Action": [
"organizations:ListAccounts",
"organizations:DescribeAccount",
"organizations:DescribeOrganization"
],
"Resource": "*"
}
]
}
- Within the AWS account that you assigned the above permissions, create the IAM Role with the following policy attached (e.g. Skylar One-Org-Read).
ScienceLogic recommends you take note of the Amazon Resource Number (ARN) of this IAM Role as it will be required for the Skylar One credential setup in future steps.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"organizations:ListAccounts",
"organizations:DescribeOrganization",
"organizations:DescribeAccount"
],
"Resource": "*"
}
]
}
- Within the AWS Account that hosts the ScienceLogic platform, create the following IAM Role (e.g. "Skylar One-EC2-Collector") and assign the following policy:
ScienceLogic recommends you take note of the Amazon Resource Number (ARN) of this IAM Role as it will be required in a future step.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": [
"arn:aws:iam::<Account ID>:role/Skylar One-Org-Read",
"arn:aws:iam::<Account ID>:role/ScienceLogic-Monitor",
"arn:aws:iam::<Account ID>:role/ScienceLogic-Monitor",
"arn:aws:iam::<Account ID>:role/ScienceLogic-Monitor"
]
}
]
}
- You must assign the role above to each EC2 instance that hosts a Skylar One component. Navigate to the Modify IAM role menu. Select the role you created and assign it to each of the EC2 instances that runs ScienceLogic components.
- After you create the IAM Role, you must update the trust policy of the Skylar One-Org-Read role. An example follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<Account ID>:role/Skylar One-EC2-Collector"
},
"Action": "sts:AssumeRole"
}
]
}
- Within each of the AWS accounts that you want to monitor you must create an IAM Role named ScienceLogic-Monitor, which is case sensitive, and assign the following policy:
For GovCloud recommendations, see the Appendix at the end of this chapter.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"acm-pca:ListCertificateAuthorities",
"airflow:ListEnvironments",
"amplify:ListApps",
"apigateway:GET",
"appflow:ListFlows",
"apprunner:ListServices",
"appstream:DescribeFleets",
"appsync:ListGraphqlApis",
"athena:ListDatabases",
"athena:ListDataCatalogs",
"athena:ListWorkGroups",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"backup:ListBackupPlans",
"cassandra:Select",
"chime:ListAccounts",
"chime:ListVoiceConnectors",
"cloudfront:GetDistribution",
"cloudfront:GetStreamingDistribution",
"cloudfront:ListDistributions",
"cloudfront:ListInvalidations",
"cloudfront:ListStreamingDistributions",
"cloudhsm:DescribeClusters",
"cloudsearch:DescribeDomains",
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarmHistory",
"cloudwatch:DescribeAlarms",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListMetricStreams",
"codebuild:ListProjects",
"codeguru-profiler:ListProfilingGroups",
"codeguru-reviewer:ListRepositoryAssociations",
"cognito-identity:ListIdentityPools",
"config:GetDiscoveredResourceCounts",
"connect:ListInstances",
"databrew:ListProjects",
"dataexchange:ListDataSets",
"datasync:ListAgents",
"datapipeline:ListPipelines",
"dax:DescribeClusters",
"devops-guru:ListMonitoredResources",
"directconnect:DescribeConnections",
"directconnect:DescribeTags",
"directconnect:DescribeVirtualInterfaces",
"dlm:GetLifecyclePolicies",
"dms:DescribeReplicationInstances",
"dynamodb:DescribeTable",
"dynamodb:ListTables",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeClientVpnEndpoints",
"ec2:DescribeFleets",
"ec2:DescribeElasticGpus",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeNatGateways",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshots",
"ec2:DescribeSpotFleetRequests",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ecs:DescribeClusters",
"ecs:DescribeContainerInstances",
"ecs:DescribeServices",
"ecs:DescribeTaskDefinition",
"ecs:DescribeTasks",
"ecs:ListClusters",
"ecs:ListContainerInstances",
"ecs:ListServices",
"ecs:ListTagsForResource",
"ecs:ListTasks",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticache:DescribeCacheClusters",
"elasticache:ListTagsForResource",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironmentHealth",
"elasticbeanstalk:DescribeEnvironmentResources",
"elasticbeanstalk:DescribeEnvironments",
"elasticbeanstalk:DescribeInstancesHealth",
"elasticfilesystem:DescribeFileSystems",
"elastic-inference:DescribeAccelerators",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticmapreduce:ListClusters",
"elasticmapreduce:ListInstances",
"elastictranscoder:ListPipelines",
"es:ListDomainNames",
"events:ListRules",
"finspace:ListEnvironments",
"firehose:ListDeliveryStreams",
"forecast:ListDatasetGroups",
"frauddetector:GetDetectors",
"fsx:DescribeFileSystems",
"gamelift:ListFleets",
"geo:ListMaps",
"glacier:GetVaultNotifications",
"glacier:ListTagsForVault",
"glacier:ListVaults",
"glue:ListJobs",
"greengrass:ListCoreDevices",
"groundstation:ListSatellites",
"guardduty:ListDetectors",
"healthlake:ListFHIRDatastores",
"iam:GetAccountAuthorizationDetails",
"iam:GetUser",
"inspector2:ListUsageTotals",
"iot:DescribeThing",
"iot:ListScheduledAudits",
"iot:ListSecurityProfiles",
"iot:ListTagsForResource",
"iot:ListThings",
"iotanalytics:ListDatastores",
"iotevents:ListDetectorModels",
"iotsitewise:ListAssetModels",
"iottwinmaker:ListWorkspaces",
"ivs:ListChannels",
"ivschat:ListRooms",
"kafka:ListClusters",
"kendra:ListIndices",
"kinesis:ListStreams",
"kinesisvideo:ListStreams",
"kms:DescribeKey",
"kms:ListAliases",
"kms:ListKeys",
"kms:ListResourceTags",
"lakeformation:ListResources",
"lambda:GetAccountSettings",
"lambda:GetPolicy",
"lambda:ListAliases",
"lambda:ListEventSourceMappings",
"lambda:ListFunctions",
"lambda:ListTags",
"lex:ListBots",
"lightsail:GetBundles",
"lightsail:GetInstanceMetricData",
"lightsail:GetInstances",
"lightsail:GetRegions",
"logs:DescribeLogGroups",
"lookoutequipment:ListDatasets",
"lookoutmetrics:ListAnomalyDetectors",
"lookoutvision:ListProjects",
"mediaconnect:ListFlows",
"mediaconvert:ListJobs
"mediaconvert:ListQueues",
"medialive:ListChannels",
"mediapackage-vod:ListPackagingConfigurations",
"mediapackage-vod:ListPackagingGroups",
"mediapackage:ListChannels",
"mediatailor:ListPlaybackConfigurations",
"mq:ListBrokers",
"network-firewall:ListFirewalls",
"nimble:ListStudios",
"opsworks:DescribeInstances",
"opsworks:DescribeStacks",
"panorama:ListDevices",
"personalize:ListDatasets",
"polly:ListLexicons",
"qldb:ListLedgers",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBSubnetGroups",
"rds:ListTagsForResource",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"rekognition:DescribeProjects",
"robomaker:ListSimulationJobs",
"route53:GetHostedZone",
"route53:ListHealthChecks",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"rum:ListAppMonitors",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketTagging",
"s3:GetBucketWebsite",
"s3:GetObject",
"s3:ListAllMyBuckets",
"s3:ListBucket",
"sagemaker:ListDomains",
"states:ListStateMachines",
"secretsmanager:ListSecrets",
"ses:ListIdentities",
"servicecatalog:SearchProductsAsAdmin",
"shield:DescribeEmergencyContactSettings",
"shield:GetSubscriptionState",
"shield:ListAttacks",
"shield:ListProtections",
"sns:ListSubscriptions",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"ssm:GetInventory",
"ssm:GetParameters",
"storagegateway:ListGateways",
"storagegateway:ListVolumes",
"sts:GetCallerIdentity",
"swf:ListDomains",
"synthetics:DescribeCanaries",
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues",
"timestream:ListDatabases",
"transcribe:ListTranscriptionJobs",
"transfer:ListServers",
"translate:ListTextTranslationJobs",
"waf-regional:GetRateBasedRule",
"waf-regional:GetRule",
"waf-regional:GetRuleGroup",
"waf-regional:GetWebACL",
"waf-regional:ListResourcesForWebACL",
"waf-regional:ListWebACLs",
"waf:GetRateBasedRule",
"waf:GetRule",
"waf:GetRuleGroup",
"waf:GetWebACL",
"waf:ListWebACLs",
"workmail:ListOrganizations",
"workspaces-web:ListPortals",
"workspaces:DescribeWorkspaceDirectories",
"workspaces:DescribeWorkspaces"
],
"Resource": "*"
}
]
}
- Once you finished creating the IAM Role, the trust policy should be updated to the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::<Account ID>:role/Skylar One-EC2-Collector"
]
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
Individual Account
To configure an individual AWS account monitored by ScienceLogic, you must create an IAM User within the particular account you want to monitor.
ScienceLogic does not recommend that this IAM User have access to the AWS Management Console.
- After you create the IAM User, you must assign several policies. Assign the first policy below:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"acm-pca:ListCertificateAuthorities",
"airflow:ListEnvironments",
"amplify:ListApps",
"apigateway:GET",
"appflow:ListFlows",
"apprunner:ListServices",
"appstream:DescribeFleets",
"appsync:ListGraphqlApis",
"athena:ListDatabases",
"athena:ListDataCatalogs",
"athena:ListWorkGroups",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"backup:ListBackupPlans",
"cassandra:Select",
"chime:ListAccounts",
"chime:ListVoiceConnectors",
"cloudfront:GetDistribution",
"cloudfront:GetStreamingDistribution",
"cloudfront:ListDistributions",
"cloudfront:ListInvalidations",
"cloudfront:ListStreamingDistributions",
"cloudhsm:DescribeClusters",
"cloudsearch:DescribeDomains",
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarmHistory",
"cloudwatch:DescribeAlarms",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListMetricStreams",
"codebuild:ListProjects",
"codeguru-profiler:ListProfilingGroups",
"codeguru-reviewer:ListRepositoryAssociations",
"cognito-identity:ListIdentityPools",
"config:GetDiscoveredResourceCounts",
"connect:ListInstances",
"databrew:ListProjects",
"dataexchange:ListDataSets",
"datasync:ListAgents",
"datapipeline:ListPipelines",
"dax:DescribeClusters",
"devops-guru:ListMonitoredResources",
"directconnect:DescribeConnections",
"directconnect:DescribeTags",
"directconnect:DescribeVirtualInterfaces",
"dlm:GetLifecyclePolicies",
"dms:DescribeReplicationInstances",
"dynamodb:DescribeTable",
"dynamodb:ListTables",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeClientVpnEndpoints",
"ec2:DescribeFleets",
"ec2:DescribeElasticGpus",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeNatGateways",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshots",
"ec2:DescribeSpotFleetRequests",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ecs:DescribeClusters",
"ecs:DescribeContainerInstances",
"ecs:DescribeServices",
"ecs:DescribeTaskDefinition",
"ecs:DescribeTasks",
"ecs:ListClusters",
"ecs:ListContainerInstances",
"ecs:ListServices",
"ecs:ListTasks",
"ecs:ListTagsForResource",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticache:DescribeCacheClusters",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironmentHealth",
"elasticbeanstalk:DescribeEnvironmentResources",
"elasticbeanstalk:DescribeEnvironments",
"elasticbeanstalk:DescribeInstancesHealth",
"elasticfilesystem:DescribeFileSystems",
"elastic-inference:DescribeAccelerators",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticmapreduce:ListClusters",
"elasticmapreduce:ListInstances",
"elastictranscoder:ListPipelines",
"es:ListDomainNames",
"events:ListRules",
"finspace:ListEnvironments",
"firehose:ListDeliveryStreams",
"forecast:ListDatasetGroups",
"frauddetector:GetDetectors",
"fsx:DescribeFileSystems",
"gamelift:ListFleets",
"geo:ListMaps",
"glacier:GetVaultNotifications",
"glacier:ListTagsForVault",
"glacier:ListVaults",
"glue:ListJobs",
"greengrass:ListCoreDevices",
"groundstation:ListSatellites",
"guardduty:ListDetectors",
"healthlake:ListFHIRDatastores",
"iam:GetAccountAuthorizationDetails",
"iam:GetUser",
"inspector2:ListUsageTotals",
"iot:DescribeThing",
"iot:ListScheduledAudits",
"iot:ListSecurityProfiles",
"iot:ListTagsForResource",
"iot:ListThings",
"iotanalytics:ListDatastores",
"iotevents:ListDetectorModels",
"iotsitewise:ListAssetModels",
"iottwinmaker:ListWorkspaces",
"ivs:ListChannels",
"ivschat:ListRooms",
"kafka:ListClusters",
"kendra:ListIndices",
"kinesis:ListStreams",
"kinesisvideo:ListStreams",
"kms:DescribeKey",
"kms:ListAliases",
"kms:ListKeys",
"kms:ListResourceTags",
"lakeformation:ListResources",
"lambda:GetAccountSettings",
"lambda:GetPolicy",
"lambda:ListAliases",
"lambda:ListEventSourceMappings",
"lambda:ListFunctions",
"lambda:ListTags",
"lex:ListBots",
"lightsail:GetBundles",
"lightsail:GetInstanceMetricData",
"lightsail:GetInstances",
"lightsail:GetRegions",
"logs:DescribeLogGroups",
"lookoutequipment:ListDatasets",
"lookoutmetrics:ListAnomalyDetectors",
"lookoutvision:ListProjects"
],
"Resource": "*"
}
]
}
- The second policy, which is a continuation of the first, contains the remaining required permissions. Two separate policies are required due to character limitations on specific types of policies. Assign the second policy below:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"mediaconnect:ListFlows",
"mediaconvert:ListJobs",
"mediaconvert:ListQueues",
"medialive:ListChannels",
"mediapackage-vod:ListPackagingConfigurations",
"mediapackage-vod:ListPackagingGroups",
"mediapackage:ListChannels",
"mediatailor:ListPlaybackConfigurations",
"mq:ListBrokers",
"network-firewall:ListFirewalls",
"nimble:ListStudios",
"opsworks:DescribeInstances",
"opsworks:DescribeStacks",
"panorama:ListDevices",
"personalize:ListDatasets",
"polly:ListLexicons",
"qldb:ListLedgers",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBSubnetGroups",
"rds:ListTagsForResource",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"rekognition:DescribeProjects",
"robomaker:ListSimulationJobs",
"route53:GetHostedZone",
"route53:ListHealthChecks",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"rum:ListAppMonitors",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketTagging",
"s3:GetBucketWebsite",
"s3:GetObject",
"s3:ListAllMyBuckets",
"s3:ListBucket",
"sagemaker:ListDomains",
"states:ListStateMachines",
"secretsmanager:ListSecrets",
"ses:ListIdentities",
"servicecatalog:SearchProductsAsAdmin",
"shield:DescribeEmergencyContactSettings",
"shield:GetSubscriptionState",
"shield:ListAttacks",
"shield:ListProtections",
"sns:ListSubscriptions",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"ssm:GetInventory",
"ssm:GetParameters",
"storagegateway:ListGateways",
"storagegateway:ListVolumes",
"sts:GetCallerIdentity",
"swf:ListDomains",
"synthetics:DescribeCanaries",
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues",
"timestream:ListDatabases",
"transcribe:ListTranscriptionJobs",
"transfer:ListServers",
"translate:ListTextTranslationJobs",
"waf-regional:GetRateBasedRule",
"waf-regional:GetRule",
"waf-regional:GetRuleGroup",
"waf-regional:GetWebACL",
"waf-regional:ListResourcesForWebACL",
"waf-regional:ListWebACLs",
"waf:GetRateBasedRule",
"waf:GetRule",
"waf:GetRuleGroup",
"waf:GetWebACL",
"waf:ListWebACLs",
"workmail:ListOrganizations",
"workspaces-web:ListPortals",
"workspaces:DescribeWorkspaceDirectories",
"workspaces:DescribeWorkspaces"
],
"Resource": "*"
}
]
}
- After you configured the IAM User policies, you must create the access key. Select the IAM User you created from the IAM User list.
- Choose the Security credentials and then choose "Create Access Key". You will need the key and secret when you configure your ScienceLogic platform to discover your account.
Discovering your AWS Organization or AWS Account
After you complete the configuration of the AWS Organization or Account, you can monitor them within Skylar One.
If you use Guided Discovery and need to upgrade to a new version of the "Amazon Web Services" PowerPack, do not first uninstall the PowerPack on Skylar One versions 11.2.0 and later as you will lose your Guided Discovery workflows. To avoid losing your workflows, see the upgrade instructions in the "Amazon Web Services" PowerPack Release Notes.
To discover your organization or account:
- Navigate to Devices and select . The Guided Discovery workflow wizard appears. You can choose from three paths to follow when mapping your organization or account. You should choose the one that corresponds to the configuration options you previously set up:
- AWS Universal EC2 Guided Discovery (Organization Credential-less)
- AWS Universal IAM Guided Discovery (Individual Account)
- AWS Universal Assume Role Guided Discovery (Organization IAM)
AWS Universal EC2 Guided Discovery (Organization Credential-less)
To define an AWS Universal EC2 Guided Discovery credential:
- Choose AWS from the Guided Discovery workflow wizard.
- Select the AWS Universal EC2 Guided Discovery radio button and click . The credential modal appears.
- Click to create the credential.
- Supply the following values:
- Name. Type a new name for your AWS credential.
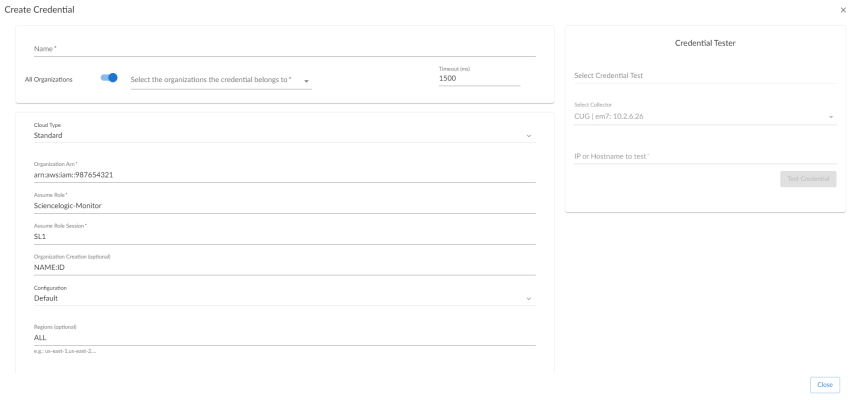
- Organization. This is the ARN of the role you created within the account you delegated adminstrator to. eg. (arn:aws:iam::123456789:role/Skylar One-Org-Read). Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Timeout (ms). Keep the default value.
- AssumeRole. The name (case sensitive) of the role you created on each of the accounts with the assigned monitoring policy.
- AssumeRole Session. Session name used associated with AssumeRole sessions.
- Organization-Creation. Type in the pattern used to create the ScienceLogic Organization. Your options are:
- Any combination
- Name:ID
- ID:Name
- Name, ID
- Configuration. Keep the default value.
- Regions. You can filter which regions discover. Specify either an allow list (eg. us-east-1,us-east-2) of regions or a block list (eg. !us-east-1,!us-west-1 will prevent us-east-1 and us-west-1 from discovering).
- Filter by Tags (optional). You can filter some discoveries by tags.
- Proxy Hostname IP/Port etc (optional). You can configure proxy requests made by the PowerPack.
- Proxy Protocol. HTTPS by default, optionally HTTP. For HTTPS, SSL Verification is based off of the Skylar One’s systems certificate trust bundle so you can configure it.
- Enable SSL Verification for Skylar One API. Enabled by default. If your Skylar One environment is configured with self signed or self generated certificates you should set this to disabled. Toggle on (blue) to enable, or toggle off (gray) to disable.
- Click .
To discover AWS Gov with credential-less discovery, you must use the classic Skylar One user interface credential option.
AWS Universal IAM Guided Discovery (Individual Account)
To define an AWS Universal IAM Guided Discovery credential:
- Choose AWS from the Guided Discovery workflow wizard.
- Select the AWS Universal IAM Guided Discovery radio button and click . The credential modal appears.
- Click to create the credential.
- Supply the following values:
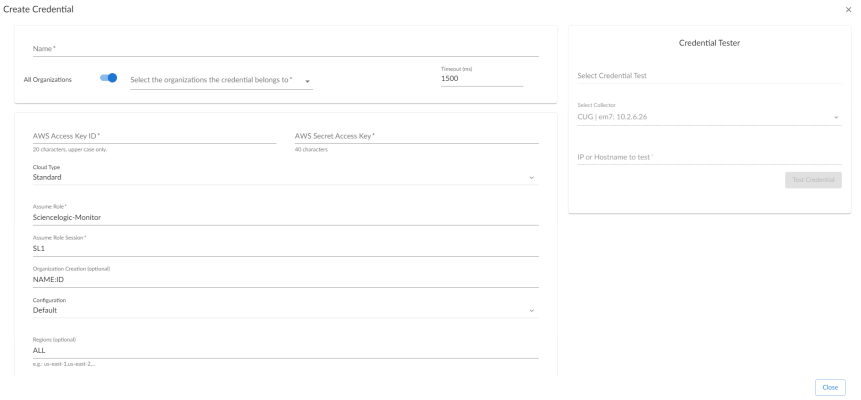
- Name. Type a new name for your AWS credential.
- Timeout (ms). Keep the default value.
- AWS Access Key ID. Type your Access Key ID.
- AWS Secret Access Key. Type your Secret Access Key.
- Cloud Type. Choose Standard, or GovCloud, if you provisioned this user in GovCloud. The Beijing option has been depreciated.
- Configuration. Keep the default value.
- Regions. You can filter which regions discover. Specify either an allow list (eg. us-east-1,us-east-2) of regions or a block list (eg. !us-east-1,!us-west-1 will prevent us-east-1 and us-west-1 from discovering).
- Filter by Tags (optional). You can filter some discoveries by tags.
- Proxy Hostname IP/Port etc (optional). You can configure proxy requests made by the PowerPack.
- Proxy Protocol. HTTPS by default, optionally HTTP. For HTTPS, SSL Verification is based off of the Skylar One’s systems certificate trust bundle so you can configure it.
- Enable SSL Verification for Skylar One API. Enabled by default. If your Skylar One environment is configured with self signed or self generated certificates you should set this to disabled. Toggle on (blue) to enable, or toggle off (gray) to disable.
- Click .
AWS Universal Assume Role Guided Discovery (Organization IAM)
If you are upgrading the PowerPack and had previously discovered accounts within an organization separately and now want to use a different discovery method, you must first disable the "AWS: Account Discovery" Dynamic Application in each account that is being upgraded.
To define an AWS Universal Assume Role Guided Discovery credential:
- Choose AWS from the Guided Discovery workflow wizard.
- Select the AWS Universal Assume Role Guided Discovery radio button and click . The credential modal appears.
- Click to create the credential.
- Supply the following values:
- Name. Type a new name for your AWS credential.
- Timeout (ms). Keep the default value.
- AWS Access Key ID. Type your Access Key ID.
- AWS Secret Access Key. Type your Secret Access Key.
- Assume Role. The name (case sensitive) of the role you created on each of the accounts with the assigned monitoring policy.
- Organization-Creation. Type in the pattern used to create the ScienceLogic Organization. Your options are:
- Any combination
- Name:ID
- ID:Name
- Name, ID
- Configuration. Keep the default value.
- Regions. You can filter which regions discover. Specify either an allow list (eg. us-east-1, us-east-2) of regions or a block list (eg. !us-east-1, !us-west-1 will prevent us-east-1 and us-west-1 from discovering).
- Filter by Tags (optional). You can filter some discoveries by tags.
- Proxy Hostname IP/Port etc (optional). You can configure proxy requests made by the PowerPack.
- Proxy Protocol. HTTPS by default, optionally HTTP. For HTTPS, SSL Verification is based off of the Skylar One’s systems certificate trust bundle so you can configure it.
- Enable SSL Verification for Skylar One API. Enabled by default. If your Skylar One environment is configured with self signed or self generated certificates you should set this to disabled. Toggle on (blue) to enable, or toggle off (gray) to disable.
- Click .
After you complete the credential creation, the guided workflow will prompt you to provide a name for the root virtual device and select a collector group to align it to. When the form is complete, the new virtual device will have an "Amazon Web Services" PowerPack Dynamic Application aligned to it.
Discovering your AWS Organization or AWS Account in the Classic Skylar One User Interface
Before you can discover and monitor your AWS organization or account, you must create the credential for the specific account you created.
Creating Credential in the Classic Skylar One User Interface
You can discover your organization or individual account in the classic Skylar One user interface using a number of ample SOAP-type credentials that are shipped in the "Amazon Web Services" PowerPack. In the classic user interface you must override the SOAP-type credentials for each of the following:
- AWS Credential (Individual Account)
- AWS Credential - EC2 Instance (Organization "Credential-less")
- AWS Credential - Master Account (Organization IAM)
AWS Credential (Individual Account)
To discover AWS using the manual discovery method, you must first define an AWS credential in Skylar One.
To define an AWS credential:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the AWS Credential sample credential and click its wrench icon (
 ). The Credential Editor modal page appears.
). The Credential Editor modal page appears.
- Enter values in the following fields:
Basic Settings
- Profile Name. Type a new name for your AWS credential.
- URL. Not required.
- HTTP Auth User. Type your Access Key ID.
- HTTP Auth Password. Type your Secret Access Key. The characters appear as asterisks to protect your password privacy.
Proxy Settings
- Hostname/IP. Optional.
- Port. Optional.
- User. Optional.
- Password. Optional.
All requests made with the "Amazon Web Services" PowerPack will be performed via HTTPs proxy with provided configuration.
SOAP Options
- Embed Value [%1]. To monitor a GovCloud account, type "us-gov-west-1" or "us-gov-east-1". Otherwise, leave this field blank.
HTTPS Headers
- Regions. Optional. Type specific regions to discover or which regions you do not want to discover.
- Regions:ALL Automatically discovers regions where your resources have been deployed.
- Regions:us-east-1, us-west-2 Discovers only us-east-1 and us-west-2.
- Regions:!us-east-1 Does not discover us-east-1, but will discover any other region with resources.
Region Allow List and Block List options cannot be combined.
- SL1APISSLVerify. Optional. This True or False header can be provided to disable SSL Verification to the Skylar One API if your Skylar One stack is deployed with self signed certificates.
- ProxyProtocol. Optional. HTTPS or HTTP header can be provided to override the default use of HTTPS for proxy settings. When HTTPS is used, SSL Verification is based on the Skylar One systems trust bundle.
- Click .
AWS Credential - Master Account (Organization IAM)
To discover AWS using the manual discovery method, you must first define an AWS credential in Skylar One.
To define an AWS credential:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the AWS Credential - Master Account sample credential and click its wrench icon (
 ). The Credential Editor modal page appears.
). The Credential Editor modal page appears.
- Enter values in the following fields:
Basic Settings
- Profile Name. Type a new name for your AWS - Master Account credential.
- URL. For commercial AWS accounts, the URL should be left as default. If you wish to discover a AWS GovCloud Organization the value should be: https://organizations.us-gov-west-1.amazonaws.com
- HTTP Auth User. Type your Access Key ID.
- HTTP Auth Password. Type your Secret Access Key. The characters appear as asterisks to protect your password privacy.
Proxy Settings
- Hostname/IP. Optional.
- Port. Optional.
- User. Optional.
- Password. Optional.
All requests made with the "Amazon Web Services" PowerPack will be performed via HTTPs proxy with provided configuration.
HTTPS Headers
- Assume Role. Type the role which you configured in each of your AWS Organization’s accounts that you wish to monitor.
- Assume Role Session. Type the session name used with the "Amazon Web Services" PowerPack AssumeRole sessions.
- Organization-Creation. Type in the pattern used to create the ScienceLogic Organization. Your options are:
- Any combination
- Name:ID
- ID:Name
- Name, ID
- Regions. Optional. Type specific regions to discover or which regions you do not want to discover.
- Regions:ALL Automatically discovers regions where your resources have been deployed.
- Regions:us-east-1, us-west-2 Discovers only us-east-1 and us-west-2.
- Regions:!us-east-1 Does not discover us-east-1, but will discover any other region with resources.
Region Allow List and Block List options cannot be combined.
- SL1APISSLVerify. Optional. This True or False header can be provided to disable SSL Verification to the Skylar One API if your Skylar One stack is deployed with self signed certificates.
- ProxyProtocol. Optional. HTTPS or HTTP header can be provided to override the default use of HTTPS for proxy settings. When HTTPS is used, SSL Verification is based on the Skylar One systems trust bundle.
- Click .
AWS Credential - EC2 Instance (Organization "Credential-less")
To discover AWS using the manual discovery method, you must first define an AWS credential in Skylar One.
To define an AWS credential:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the AWS Credential - EC2 Instance sample credential and click its wrench icon (
 ). The Credential Editor modal page appears.
). The Credential Editor modal page appears.
- Enter values in the following fields:
Basic Settings
- Profile Name. Type a new name for your AWS - EC2 Instance credential.
- URL. For commercial AWS accounts, the URL should be left as default. If you wish to discover a AWS GovCloud Organization the value should be: https://organizations.us-gov-west-1.amazonaws.com
- HTTP Auth User. Leave as default.
- HTTP Auth Password. Leave blank.
Proxy Settings
- Hostname/IP. Optional.
- Port. Optional.
- User. Optional.
- Password. Optional.
All requests made with the "Amazon Web Services" PowerPack will be performed via HTTPs proxy with provided configuration.
HTTPS Headers
- OrganizationARN. This is the ARN of the role you created within the account you delegated adminstrator to. eg. (arn:aws:iam::123456789:role/Skylar One-Org-Read). Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Assume Role. Type the role which you configured in each of your AWS Organization’s accounts that you wish to monitor.
- Assume Role Session. Type the session name used with the "Amazon Web Services" PowerPack AssumeRole sessions.
- Organization-Creation. Type in the pattern used to create the ScienceLogic Organization. Your options are:
- Any combination
- Name:ID
- ID:Name
- Name, ID
- Regions. Optional. Type specific regions to discover or which regions you do not want to discover.
- Regions:ALL Automatically discovers regions where your resources have been deployed.
- Regions:us-east-1, us-west-2 Discovers only us-east-1 and us-west-2.
- Regions:!us-east-1 Does not discover us-east-1, but will discover any other region with resources.
Region Allow List and Block List options cannot be combined.
- SL1APISSLVerify. Optional. This True or False header can be provided to disable SSL Verification to the Skylar One API if your Skylar One stack is deployed with self signed certificates.
- ProxyProtocol. Optional. HTTPS or HTTP header can be provided to override the default use of HTTPS for proxy settings. When HTTPS is used, SSL Verification is based on the Skylar One systems trust bundle.
- Click .
Launching the Discovery Session in the Classic Skylar One User Interface
AWS Organizations
For the both types of the AWS Organization discovery, you should create and launch a Discovery Session to start monitoring your AWS Organization. To discover AWS Accounts in an AWS Organization, perform the following steps:
- Go to the Discovery Control Panel page (System > Manage > Classic Discovery or System > Manage > Discovery in the classic user interface).
- Click the button. The Discovery Session Editor page appears.
- Supply values in the following fields:
- Name. Type the name you want to name your discovery session, such as "AWS Org Discovery".
- IP Address/Hostname. For commercial AWS type organizations.us-east-1.amazonaws.com. For GOVCloud type organizations.us-gov-west-1.amazonaws.com.
- Other Credentials. Select the credential you created.
- Discover Non-SNMP. Select this checkbox.
If your system can not discover a device via PING, please contact ScienceLogic Support for a manual workaround procedure.
- Click the button to launch the discovery session. Your AWS Organization will now discover over the course of the next several hours.
Individual Accounts
The procedure for the Individual Account configuration for the Classic Skylar One user interface has been simplified to creating a Virtual Device and then aligning the "AWS: Account Discovery" Dynamic Application to your credential.
To create a virtual device that represents your Amazon service:
- Go to the Device Manager page (Devices > Classic Devices, or Registry > Devices > Device Manager in the classic user interface in the Skylar One classic user interface).
- Click the button, then select Create Virtual Device. The Virtual Device modal page appears.
- Enter values in the following fields:
- Device Name. Type a name for your virtual device.
- Organization. Select the organization for this device. The organization the device is associated with limits the users that will be able to view and edit the device.
- Device Class. Select Service | AWS Service.
- Collector. Select the collector group that will monitor the device.
- Click the button to create the virtual device.
To discover your AWS account, you must manually align the "AWS: Account Discovery" Dynamic Application with the AWS virtual device. After you do so, the other Dynamic Applications in the "Amazon Web Services" PowerPack will automatically align to discover and monitor all of the components in your AWS account.
To align the "AWS: Account Discovery" Dynamic Application to your virtual device:
- Go to the Device Manager page (Devices > Classic Devices, or Registry > Devices > Device Manager in the classic user interface).
- Click the wrench icon (
 ) for your virtual device.
) for your virtual device. - In the Device Administration panel, click the tab. The Dynamic Application Collections page appears.
- Click the button, and then select Add Dynamic Application from the menu.
- In the Dynamic Application Alignment modal page, select AWS: Account Discovery in the Dynamic Applications field.
- In the Credentials field, select the credential you created for your AWS Individual Account.
- Click the button to align the Dynamic Application.
The only Dynamic Application you should ever need to manually align from the "Amazon Web Services" PowerPack is the "AWS: Account Discovery" Dynamic Application. Aligning any other Dynamic Application from the PowerPack will have unexpected results.
Appendix
To configure the AWS Organization EC2 "Credential-less" account for GovCloud, use the following minimum permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"acm-pca:ListCertificateAuthorities",
"apigateway:GET",
"appstream:DescribeFleets",
"athena:ListWorkGroups",
"athena:ListDatabases",
"athena:ListDataCatalogs",
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"backup:ListBackupPlans",
"cloudhsm:DescribeClusters",
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus",
"cloudwatch:DescribeAlarmHistory",
"cloudwatch:DescribeAlarms",
"cloudwatch:GetMetricData",
"cloudwatch:GetMetricStatistics",
"cloudwatch:ListMetrics",
"cloudwatch:ListMetricStreams",
"codebuild:ListProjects",
"cognito-identity:ListIdentityPools",
"config:GetDiscoveredResourceCounts",
"connect:ListInstances",
"databrew:ListProjects",
"datasync:ListAgents",
"directconnect:DescribeConnections",
"directconnect:DescribeTags",
"directconnect:DescribeVirtualInterfaces",
"dms:DescribeReplicationInstances",
"dynamodb:DescribeTable",
"dynamodb:ListTables",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeClientVpnEndpoints",
"ec2:DescribeFleets",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeNatGateways",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshots",
"ec2:DescribeSpotFleetRequests",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGateways",
"ec2:DescribeVolumes",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ecs:DescribeClusters",
"ecs:DescribeContainerInstances",
"ecs:DescribeServices",
"ecs:DescribeTaskDefinition",
"ecs:DescribeTasks",
"ecs:ListClusters",
"ecs:ListContainerInstances",
"ecs:ListServices",
"ecs:ListTasks",
"ecs:ListTagsForResource",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticache:DescribeCacheClusters",
"elasticbeanstalk:DescribeConfigurationSettings",
"elasticbeanstalk:DescribeEnvironmentHealth",
"elasticbeanstalk:DescribeEnvironmentResources",
"elasticbeanstalk:DescribeEnvironments",
"elasticbeanstalk:DescribeInstancesHealth",
"elasticfilesystem:DescribeFileSystems",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"elasticmapreduce:ListClusters",
"elasticmapreduce:ListInstances",
"es:ListDomainNames",
"events:ListRules",
"firehose:ListDeliveryStreams",
"fsx:DescribeFileSystems",
"glacier:GetVaultNotifications",
"glacier:ListTagsForVault",
"glacier:ListVaults",
"glue:ListJobs",
"greengrass:ListCoreDevices",
"guardduty:ListDetectors",
"iam:GetAccountAuthorizationDetails",
"iam:GetUser",
"inspector2:ListUsageTotals",
"iot:DescribeThing",
"iot:ListScheduledAudits",
"iot:ListSecurityProfiles",
"iot:ListTagsForResource",
"iot:ListThings",
"iotevents:ListDetectorModels",
"iotsitewise:ListAssetModels",
"kafka:ListClusters",
"kendra:ListIndices",
"kinesis:ListStreams",
"kms:DescribeKey",
"kms:ListAliases",
"kms:ListKeys",
"kms:ListResourceTags",
"lakeformation:ListResources",
"lambda:GetAccountSettings",
"lambda:GetPolicy",
"lambda:ListAliases",
"lambda:ListEventSourceMappings",
"lambda:ListFunctions",
"lambda:ListTags",
"logs:DescribeLogGroups",
"mq:ListBrokers",
"network-firewall:ListFirewalls",
"polly:ListLexicons",
"rds:DescribeDBClusters",
"rds:DescribeDBInstances",
"rds:DescribeDBSubnetGroups",
"rds:ListTagsForResource",
"redshift:DescribeClusters",
"redshift:DescribeLoggingStatus",
"rekognition:DescribeProjects",
"route53:GetHostedZone",
"route53:ListHealthChecks",
"route53:ListHostedZones",
"route53:ListResourceRecordSets",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketTagging",
"s3:GetBucketWebsite",
"s3:GetObject",
"s3:ListAllMyBuckets",
"s3:ListBucket",
"sagemaker:ListDomains",
"states:ListStateMachines",
"secretsmanager:ListSecrets",
"servicecatalog:SearchProductsAsAdmin",
"ses:ListIdentities",
"sns:ListSubscriptions",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListQueues",
"ssm:GetInventory",
"ssm:GetParameters",
"storagegateway:ListGateways",
"storagegateway:ListVolumes",
"sts:GetCallerIdentity",
"swf:ListDomains",
"synthetics:DescribeCanaries",
"tag:GetResources",
"tag:GetTagKeys",
"tag:GetTagValues",
"transcribe:ListTranscriptionJobs",
"transfer:ListServers",
"translate:ListTextTranslationJobs",
"workspaces:DescribeWorkspaceDirectories",
"workspaces:DescribeWorkspaces"
],
"Resource": "*"
}
]
}