The following sections describe how to use the Run Book Action policies and Run Book Automation policies that are included in the "Microsoft: Azure" PowerPack:
Azure Run Book Automation Permissions
If you have a custom user or are using RDS instead of the central database credential that connects as root, you will need to set the following permissions in your database to use the Run Book automations in the "Microsoft: Azure" PowerPack:
GRANT EXECUTE ON PROCEDURE 'master'.'process_unmerge_devices' TO 'azure_pp_rba'@'%';
GRANT EXECUTE ON FUNCTION 'master'.'primary_db_id' TO 'azure_pp_rba'@'%';
GRANT EXECUTE ON PROCEDURE 'master'.'process_merge_devices' TO 'azure_pp_rba'@'%';
About the Azure Run Book Actions and Automations
The "Microsoft: Azure" PowerPack includes Run Book Actions and Run Book Automation policies that can be used to:
- Automatically disable data collection for Virtual Machines, Virtual Machine Scale Sets (VMSS), and Storage Disks based on their VM tag
- Automatically disable data collection for Databricks based on tags
- Automatically create and start a discovery session using the public or private IP address of a Virtual Machine, and after the device is discovered, merge the physical device with the corresponding component
- Automatically move a Virtual Machine to a vanished state if the component is in a terminated state
The following table describes the Run Book Automation policies and what they do:
| Run Book Automation Policy Name | Result |
|---|---|
| Microsoft Azure: Disable and Discover from IP | If a component device belongs to the Virtual Machines device group and has a relevant Azure tag, Skylar One disables the device. |
| Microsoft Azure: Disable Storage Disks | If a component device belongs to the Storage Disks device group and has a relevant Azure tag, Skylar One disables the device. |
| Microsoft Azure: Discover from IP | Skylar One automatically discovers VM instances by public or private IP address. |
| Microsoft Azure: Merge with VM | If Skylar One finds the "Device Record Created" event on the newly discovered physical device, Skylar One merges the newly discovered physical device with the corresponding component device. |
| Microsoft Azure: Vanish Terminated VMs | If a device is in a terminated or terminating state, Skylar One un-merges the VM instance and physical device (if applicable), clears the device's associated events, and then moves the device to a vanished state. |
| Microsoft: Azure Data Lake Devices Classification Required | Assigns the correct device class to Storage Account devices. |
| Microsoft: Azure Resource Reclassification |
Aligns the correct device class to fully-supported Azure services, and then tries to unalign the Resource List Configuration Dynamic Application. |
| Microsoft Azure: Disable Databricks | If a component device belongs to the Databricks device group and has a relevant Azure tag, Skylar One disables the device. |
The Run Book Automation policies in the "Microsoft: Azure" PowerPack are disabled by default. To use these Run Book Automations, you must enable the Run Book Automation policies and modify the parameters in the Run Book Actions as needed. See the following procedures for more information.
As a prerequisite for discovering physical devices, make sure that traffic to the following ports is allowed in the inbound security rules on the Azure Portal for a Virtual Machine:
- Port 161. Allows the discovery session to use SNMP credentials.
- Ports 5985, 5986. Allows the discovery session to use PowerShell credentials.
If the above ports are not open or cannot be opened, you can include extra credentials for the discovery session by modifying the following parameter in the "Microsoft Azure: Discover from IP" Run Book Action, using a comma-separated list of credential IDs:
EXTRA_CREDS = "<ID1>,<ID2>,<ID3>"
NOTE: When a discovery session is given a list of credentials, the first credential that successfully authenticates is used to discover a physical device.
For more information about Microsoft Azure inbound security rules, see the following Microsoft article: How to open ports to a virtual machine with the Azure portal.
Disabling VMs or Storage Disks by VM Tag
NOTE: The following Run Book Automation policies do not enable data collection for Azure VMs or Storage Disks. You must manually enable data collection for these VMs or Storage Disks.
Run Book Automation Policy: Disable and Discover from IP
The "Disable and Discover from IP" Run Book Automation policy runs only on newly discovered VMs. The policy takes no action for existing VMs.
The automation for disabling Azure VMs or Azure VMSSs includes the following Run Book Actions, which are executed in the following order:
- Microsoft Azure: Get Unique ID. This action retrieves the unique ID of the component. This action runs on the Database Server.
- Microsoft Azure: Collect VM Configuration. This action retrieves the VM configuration, including the tags used to disable the VM. This action runs on the Collector.
- Microsoft Azure: Disable By VM Tag. If a newly discovered VM contains the tags specified in the snippet, this action disables collection for this component.
- Microsoft Azure: Discover from IP. If the VM is running and is newly discovered, this action creates the discovery session and runs automatically to discover the physical device. This action will not create a discovery session for a discovered VM that was disabled right after being discovered. By default the snippet uses the public IP address and PowerShell (unless you specify SNMP) to create the discovery session. You can update these parameters as needed.
The following Run Book Automation policy triggers the above Run Book Actions:
- Microsoft Azure: Disable and Discover from IP. This Run Book Automation policy executes when the "Component Device Record Created" event is active on the matching devices, immediately after the devices are discovered in the system. Enable this Run Book Automation policy if you want to disable VM instances by Azure tag and want to enable automated discovery of VM instances by public or private IP address. This policy is configured to run both processes in the correct order for VM instances.
Run Book Automation Policy: Disable Storage Disks
The "Disable Storage Disks" Run Book Automation policy runs only on newly discovered Storage Disks. The policy takes no action for existing Storage Disks.
The automation for disabling Azure Storage Disks includes the following Run Book Actions, which are executed in the following order:
- Microsoft Azure: Get Unique ID. This action retrieves the unique ID of the component. This action runs on the Database Server.
- Microsoft Azure: Collect Storage Disk Configuration. This action retrieves disk and VM configurations, including the tags that belong to the VM used by the Storage Disk. This action runs on the Collector.
- Microsoft Azure: Disable By VM Tag. If a newly discovered Storage Disk belongs to a VM that contains the tags specified in the snippet, this action disables collection for the component.
The following Run Book Automation policy triggers the above actions:
- Microsoft Azure: Disable Storage Disks. This Run Book Automation policy executes when the "Component Device Record Created" event is active on the matching devices, immediately after the devices are discovered in the system. Enable this policy if you want to disable Storage Disk instances by Azure tag, but do not want to enable automated discovery of Storage Disk instances by public or private IP address.
Configuration Steps
To use these automations, you must:
- Modify the parameters of the "Disable By VM Tag" Run Book Action
- Enable the "Component Device Record Created" event policy
- Enable the Run Book Automation policies
- Configure your system to preserve these changes
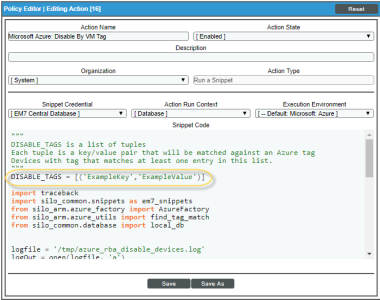
Modifying the Parameters of the "Disable By VM Tag" Run Book Action
The snippet for the "Microsoft Azure: Disable by VM Tag" Run Book Action includes the pre-defined list of key/value pairs that Skylar One compares to the tags collected from Azure. You must modify this list to include the key/value pairs that you want to use to disable VM instances.
To modify the parameters for the "Microsoft Azure: Disable by VM Tag" Run Book Action:
- Go to the Action Policy Manager page (Registry > Run Book > Actions).
- Click the wrench icon (
 ) for the "Microsoft Azure: Disable by VM Tag" Run Book Action.
) for the "Microsoft Azure: Disable by VM Tag" Run Book Action.
- In the Snippet Code field, locate and edit the following line:
DISABLE_TAGS = [('ExampleKey','ExampleValue')]
The line must be in the following format, with each key and each value inside single-quotes and each key/value pair comma-separated inside parentheses, with commas separating each key/value pair.
DISABLE_TAGS [('Key','Value'),('Key','Value'),...,('Key','Value')]
For example, suppose you want to disable a VM instance where the "Environment" key is either "dev" or "test" or the "Owner" key is "Sales". You would update the line so it looks like this:
DISABLE_TAGS [('Environment','dev'),('Environment','test'),('Owner','Sales')]
- When you are done editing, click the button.
Enabling the "Component Device Record Created" Event Policy
To enable the "Component Device Record Created" event policy:
- Go to the Event Policy Manager page (Registry > Events > Event Manager).
- Click the wrench icon (
 ) for the "Component Device Record Created" event policy.
) for the "Component Device Record Created" event policy. - In the Operational State field, select Enabled.
- Click .
To prevent this change from being overwritten when the PowerPacks installed on the system are updated, you can enable the Selective PowerPack Field Protection option. To enable this option:
- Go to the Behavior Settings page (System > Settings > Behavior).
- Check the Enable Selective PowerPack Field Protection checkbox.
- Click .
Enabling the Run Book Automation Policies
To enable one or more Run Book Automation policies in the "Microsoft: Azure" PowerPack:
- Go to the Automation Policy Manager page (Registry > Run Book > Automation).
- Click the wrench icon (
 ) for the Run Book Automation policy you want to enable.
) for the Run Book Automation policy you want to enable. - In the Policy State field, select Enabled.
- Click .
Preserving Automation Changes
If you have modified Run Book Actions and Run Book Automation policies that are included in the "Microsoft: Azure" PowerPack, those changes will be overwritten when the PowerPack is updated in your system. If you have modified Run Book Actions and Run Book Automation policies that are included in the PowerPack, you can:
- Re-implement those changes after each update of the "Microsoft: Azure"PowerPack.
- Remove the content from the PowerPack on your system. When the "Microsoft: Azure" PowerPack is updated in your system, updated versions of this content will not be installed on your system and your local changes will be preserved.
To remove Run Book Action or Run Book Automation policy content from the "Microsoft: Azure" PowerPack on your system:
- Go to the PowerPack Manager page (System > Manage > PowerPacks).
- Click the wrench icon (
 ) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears.
) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears. - In the left NavBar of the Editing PowerPack page, select the type of content you want to remove:
- To remove a Run Book Action, click Run Book Actions. The Embedded Run Book Actions and Available Run Book Actions panes appear.
- To remove a Run Book Automation policy, click Run Book Policies. The Embedded Run Book Policies and Available Run Book Policies panes appear.
- In the upper pane, click the delete icon (
 ) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
Disabling Databricks by Tag
NOTE: The following Run Book Automation policy does not enable data collection for Azure Databricks. You must manually enable data collection for these Databricks.
Run Book Automation Policy: Disable Databricks
The "Disable Databricks" Run Book Automation policy runs only on newly discovered Databricks. The policy takes no action for existing Databricks.
The automation for disabling Azure Databricks includes the following Run Book Actions, which are executed in the following order:
-
Microsoft: Azure Get Unique ID. This action retrieves the unique ID of the component. This action runs on the Database Server.
-
Microsoft: Azure Collect Databricks Configuration. This action retrieves Databrick configurations, including the tags. This action runs on the Collector.
-
Microsoft: Azure Disable By Databrick Tag. If a newly discovered Databrick contains the tags specified in the snippet, this action disables collection for the component. This action runs on the Database Server.
The following Run Book Automation policy triggers the above actions:
-
Microsoft Azure: Disable Databricks. This Run Book Automation policy executes when the "Component Device Record Created" event is active on the matching devices, immediately after the devices are discovered in the system. Enable this policy if you want to disable Databrick instances by Azure tag.
Configuration Steps
To use these automations, you must:
- Modify the parameters of the "Disable by Databrick Tag" Run Book Action
- Enable the "Component Device Record Created" event policy
- Enable the Run Book Automation policies
- Configure your system to preserve these changes
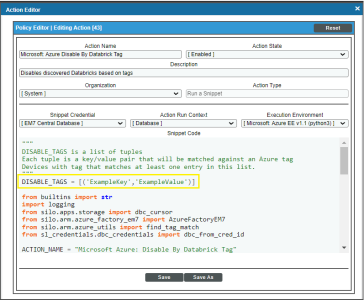
Modifying the Parameters of the "Disable By Databrick Tag" Run Book Action
The snippet for the "Microsoft: Azure Disable By Databrick Tag" Run Book Action includes the pre-defined list of key/value pairs that Skylar One compares to the tags collected from Azure. You must modify this list to include the key/value pairs that you want to use to disable Databrick instances.
To modify the parameters for the "Microsoft: Azure Disable By Databrick Tag" Run Book Action:
-
Go to the Action Policy Manager page (Registry > Run Book > Actions).
-
Click the wrench icon (
 ) for the "Microsoft: Azure Disable By Databrick Tag" Run Book Action.
) for the "Microsoft: Azure Disable By Databrick Tag" Run Book Action.
-
In the Snippet Code field, locate and edit the following line:
DISABLE_TAGS = [('ExampleKey','ExampleValue')]
The line must be in the following format, with each key and each value inside single-quotes and each key/value pair comma-separated inside parentheses, with commas separating each key/value pair.
DISABLE_TAGS [('Key','Value'),('Key','Value'),...,('Key','Value')]
For example, if you want to disable a VM instance where the "Environment" key is "dev", "test", or the "Owner" key is "Sales", update the line so it looks like this:
DISABLE_TAGS [('Environment','dev'),('Environment','test'),('Owner','Sales')]
-
When you are done editing, click the button.
Enabling the "Component Device Record Created" Event Policy (Discover from IP Only)
To enable the "Component Device Record Created" event policy:
- Go to the Event Policy Manager page (Registry > Events > Event Manager).
- Click the wrench icon (
 ) for the "Component Device Record Created" event policy.
) for the "Component Device Record Created" event policy. - In the Operational State field, select Enabled.
- Click .
To prevent this change from being overwritten when the PowerPacks installed on the system are updated, you can enable the Selective PowerPack Field Protection option. To enable this option:
- Go to the Behavior Settings page (System > Settings > Behavior).
- Check the Enable Selective PowerPack Field Protection checkbox.
- Click .
Enabling the Run Book Automation Policies
To enable one or more Run Book Automation policies in the "Microsoft: Azure" PowerPack:
- Go to the Automation Policy Manager page (Registry > Run Book > Automation).
- Click the wrench icon (
 ) for the Run Book Automation policy you want to enable.
) for the Run Book Automation policy you want to enable. - In the Policy State field, select Enabled.
- Click .
Preserving Automation Changes
If you have modified Run Book Actions and Run Book Automation policies that are included in the "Microsoft: Azure" PowerPack, those changes will be overwritten when the PowerPack is updated in your system. If you have modified Run Book Actions and Run Book Automation policies that are included in the PowerPack, you can:
- Re-implement those changes after each update of the "Microsoft: Azure"PowerPack.
- Remove the content from the PowerPack on your system. When the "Microsoft: Azure" PowerPack is updated in your system, updated versions of this content will not be installed on your system and your local changes will be preserved.
To remove Run Book Action or Run Book Automation policy content from the "Microsoft: Azure" PowerPack on your system:
- Go to the PowerPack Manager page (System > Manage > PowerPacks).
- Click the wrench icon (
 ) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears.
) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears. - In the left NavBar of the Editing PowerPack page, select the type of content you want to remove:
- To remove a Run Book Action, click Run Book Actions. The Embedded Run Book Actions and Available Run Book Actions panes appear.
- To remove a Run Book Automation policy, click Run Book Policies. The Embedded Run Book Policies and Available Run Book Policies panes appear.
- In the upper pane, click the delete icon (
 ) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
Discovering VMs and Merging Physical Devices with Components
Run Book Automation Policy: Discover from IP
The "Discover from IP" Run Book Automation policy runs only on newly discovered VMs. The policy takes no action for existing VMs.
The automation for discovering Azure VMs or VMSSs by public or private IP addresses and then discovering the physical device includes three Run Book Actions that are executed in the following order:
- Microsoft Azure: Get Unique ID. This action retrieves the unique ID of the component. This action runs on the Database Server.
- Microsoft Azure: Collect VM Configuration. This action retrieves the VM configuration, including public or private IP address and open ports. This action runs on the Collector.
- Microsoft Azure: Discover from IP. If the VM is running and is newly discovered, this action creates the discovery session and runs automatically to discover the physical device. The discovery session name uses the following format: Azure_VM-IP_address.
The following Run Book Automation policy triggers the above Run Book Actions:
- Microsoft Azure: Discover From IP. This Run Book Automation policy executes when the "Component Device Record Created" event is active on the matching devices, immediately after the devices are discovered in the system. Use this action to enable automated discovery of VM instances by public or private IP address. By default the snippet uses the public IP address and PowerShell (unless you specify SNMP) to create the discovery session. You can update these parameters as needed.
Note: If a VM was created as "Stopped" by default, and that VM was discovered by the PowerPack, the Run Book Action will not create a discovery session. The action cannot collect an IP address for a stopped VM.
Run Book Automation Policy: Merge with VM
When the "Merge with VM" Run Book Automation policy finds the "Device Record Created" event on the newly discovered physical device, the policy triggers the following Run Book Action:
- Microsoft Azure: Merge Physical with Component. This action merges the newly discovered physical device with the corresponding component device.
The "Merge with VM" Run Book Automation policy runs only on newly discovered devices. The policy takes no action for existing VMs. The discovery session created with the "Discover from IP" Run Book Action, above, will discover the physical device.
Configuration Steps
To use these automations, you must:
- Modify the parameters of the Run Book Actions
- Enable the "Component Device Record Created" event policy (Discover from IP policy only)
- Enable the "Device Record Created" event policy
- Enable the Run Book Automation policies
- Configure your system to preserve these changes
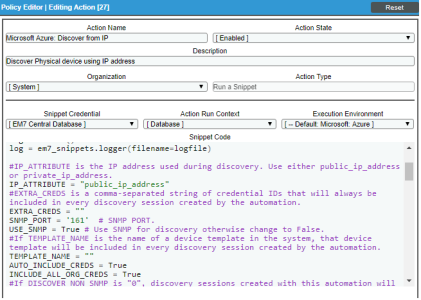
Modifying the Parameters of the Run Book Actions
The snippet for the "Microsoft Azure: Discover from IP" Run Book Action includes parameters that define how the Run Book Action creates discovery sessions. By default the snippet uses the public IP address and PowerShell (unless you specify SNMP) to create the discovery session. You can update these parameters as needed.
To modify the parameters for the "Microsoft Azure: Discover from IP" Run Book Action:
- Go to the Action Policy Manager page (Registry > Run Book > Actions).
- Click the wrench icon (
 ) for the "Microsoft Azure: Discover from IP" Run Book Action.
) for the "Microsoft Azure: Discover from IP" Run Book Action. - In the Snippet Code field, locate and edit the lines for the parameters you want to change:
- As needed, update the following lines:
- Discovery will use the PowerShell credential by default.
For Linux servers, add the user-defined credentials in the EXTRA_CREDS parameter.
- To change from the default public IP address to private IP address:
IP_ATTRIBUTE = 'private_ip_address'
If you change the IP address value to private for this Run Book Action, then you must also update the following line in the "Microsoft Azure: Merge with VM" Run Book Action: IP_ATTRIBUTE = 'c-VM-public_ipaddress".
- To include additional user-defined credentials in the discovery session, use a comma-separated list of credential IDs:
EXTRA_CREDS = "<ID1>,<ID2>,<ID3>"
- If you want to use EXTRA_CREDS only, set AUTO_INCLUDE_CREDS to False:
AUTO_INCLUDE_CREDS = False
- To apply a device template to all newly discovered physical devices, specify the name of the template:
TEMPLATE_NAME = "<Name>"
- To disable the automatic alignment of credentials to the discovery session, change this line to:
AUTO_INCLUDE_CREDS = False
- If INCLUDE_ALL_ORG_CREDS is "True" and the AUTO_INCLUDE_CREDS parameter is "True", credentials that are aligned with all organizations (credentials that do not have an explicit organization alignment) are automatically included in the discovery session when that credential meets the other requirements for being automatically included in the discovery session.
INCLUDE_ALL_ORG_CREDS = True
- To enable discovery using SNMP credentials, update the following lines:
USE_SNMP = True
DISCOVER_NON_SNMP = '0'
- Click the wrench icon (
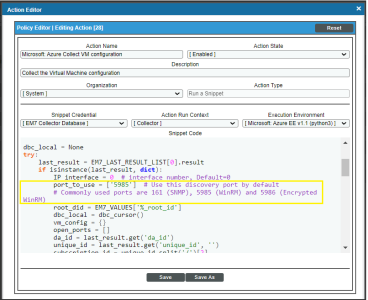
 ) for the "Microsoft Azure: Collect VM configuration" Run Book Action.
) for the "Microsoft Azure: Collect VM configuration" Run Book Action. - In the Snippet Code field, locate and edit the port_to_use variable with the desired discovery port.
- When you are done editing, click the button.
Enabling the "Component Device Record Created" Event Policy (Discover from IP Only)
To enable the "Component Device Record Created" event policy:
- Go to the Event Policy Manager page (Registry > Events > Event Manager).
- Click the wrench icon (
 ) for the "Component Device Record Created" event policy.
) for the "Component Device Record Created" event policy. - In the Operational State field, select Enabled.
- Click .
To prevent this change from being overwritten when the PowerPacks installed on the system are updated, you can enable the Selective PowerPack Field Protection option. To enable this option:
- Go to the Behavior Settings page (System > Settings > Behavior).
- Check the Enable Selective PowerPack Field Protection checkbox.
- Click .
Enabling the "Device Record Created" Event Policy
To enable the "Device Record Created" event policy:
- Go to the Event Policy Manager page (Registry > Events > Event Manager).
- Click the wrench icon (
 ) for the "Device Record Created" event policy.
) for the "Device Record Created" event policy. - In the Operational State field, select Enabled.
- Click .
To prevent this change from being overwritten when the PowerPacks installed on the system are updated, you can enable the Selective PowerPack Field Protection option. To enable this option:
- Go to the Behavior Settings page (System > Settings > Behavior).
- Check the Enable Selective PowerPack Field Protection checkbox.
- Click .
Enabling the Run Book Policies
To enable one or more Run Book Automation policies in the "Microsoft: Azure" PowerPack:
- Go to the Automation Policy Manager page (Registry > Run Book > Automation).
- Click the wrench icon (
 ) for the Run Book Automation policy you want to enable.
) for the Run Book Automation policy you want to enable. - In the Policy State field, select Enabled.
- Click .
Preserving Automation Changes
If you have modified Run Book Actions and Run Book Automation policies that are included in the "Microsoft: Azure" PowerPack, those changes will be overwritten when the PowerPack is updated in your system. If you have modified Run Book Actions and Run Book Automation policies that are included in the PowerPack, you can:
- Re-implement those changes after each update of the "Microsoft: Azure"PowerPack.
- Remove the content from the PowerPack on your system. When the "Microsoft: Azure" PowerPack is updated in your system, updated versions of this content will not be installed on your system and your local changes will be preserved.
To remove Run Book Action or Run Book Automation policy content from the "Microsoft: Azure" PowerPack on your system:
- Go to the PowerPack Manager page (System > Manage > PowerPacks).
- Click the wrench icon (
 ) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears.
) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears. - In the left NavBar of the Editing PowerPack page, select the type of content you want to remove:
- To remove a Run Book Action, click Run Book Actions. The Embedded Run Book Actions and Available Run Book Actions panes appear.
- To remove a Run Book Automation policy, click Run Book Policies. The Embedded Run Book Policies and Available Run Book Policies panes appear.
- In the upper pane, click the delete icon (
 ) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
Vanishing Terminated or Terminating VM Instances
If a device is in a terminated or terminating state, the "Vanish Terminated VMs" Run Book Action un-merges the VM instance and physical device (if applicable), clears the device's associated events, and then moves the device to a vanished state.
The "Vanish Terminated VMs" Run Book Automation policy runs only on newly discovered VMs. The policy takes no action for existing VMs.
The automation for vanishing terminated VM instances includes the following Run Book Actions:
- Microsoft Azure: Get Unique ID. This action retrieves the unique ID of the component. This action runs on the Database Server.
- Microsoft Azure: Check VM Availability. This action uses the unique ID of the component to get the device availability status. If the device availability status is "Terminated", this action moves to the following Run Book Action, "Vanish Terminated VMs". This action runs on the Collector.
- Microsoft Azure: Vanish Terminated VMs. This action moves the device to the Vanish state when the VM has been terminated in the Azure Portal. This action runs on the Database Server. This action determines if the component was merged with a physical device:
- If the component was not merged, the action will delete the device's events and move the device to a Vanish state.
- If the component was merged, the action will un-merge the component with the physical device, and then it will clear the device's events and move the device to a Vanish state.
- If the component was merged, but the VM was powered off, the action will not do anything until the VM is powered on, at which point the action will update the IP address of the physical device.
When a merged device is un-merged, the component device vanishes, and the physical device is moved to an automatically created Collector group named "Virtual Group".
The following Run Book Automation policy triggers the above actions:
- Microsoft Azure: Vanish Terminated Instances. This Run Book Automation policy executes when the "Availability Check Failed" event is raised on the virtual machine when it terminated.
To use this automation, you must:
Enabling the Run Book Automation Policies
To enable one or more Run Book Automation policies in the "Microsoft: Azure" PowerPack:
- Go to the Automation Policy Manager page (Registry > Run Book > Automation).
- Click the wrench icon (
 ) for the Run Book Automation policy you want to enable.
) for the Run Book Automation policy you want to enable. - In the Policy State field, select Enabled.
- Click .
Preserving Automation Changes
If you have modified Run Book Actions and Run Book Automation policies that are included in the "Microsoft: Azure" PowerPack, those changes will be overwritten when the PowerPack is updated in your system. If you have modified Run Book Actions and Run Book Automation policies that are included in the PowerPack, you can:
- Re-implement those changes after each update of the "Microsoft: Azure"PowerPack.
- Remove the content from the PowerPack on your system. When the "Microsoft: Azure" PowerPack is updated in your system, updated versions of this content will not be installed on your system and your local changes will be preserved.
To remove Run Book Action or Run Book Automation policy content from the "Microsoft: Azure" PowerPack on your system:
- Go to the PowerPack Manager page (System > Manage > PowerPacks).
- Click the wrench icon (
 ) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears.
) for the "Microsoft: Azure" PowerPack. The Editing PowerPack page appears. - In the left NavBar of the Editing PowerPack page, select the type of content you want to remove:
- To remove a Run Book Action, click Run Book Actions. The Embedded Run Book Actions and Available Run Book Actions panes appear.
- To remove a Run Book Automation policy, click Run Book Policies. The Embedded Run Book Policies and Available Run Book Policies panes appear.
- In the upper pane, click the delete icon (
 ) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.
) for each Run Book Action or Run Book Automation policy that you want to remove from the "Microsoft: Azure" PowerPack on your system.