The following sections describe how to configure Microsoft Azure resources for monitoring by Skylar One using the "Microsoft: Azure" PowerPack:
NOTE: The "Microsoft: Azure" PowerPack can monitor Microsoft Azure resources, Microsoft Azure Government resources, and Microsoft Azure resources in Germany and China regions.
Configuring an Azure Active Directory Application
To create a SOAP/XML credential that allows Skylar One to access Microsoft Azure, you must provide the following information about an Azure application that is already registered with an Azure AD tenant:
- Application ID
- Subscription ID (if monitoring a single subscription)
- Tenant ID
- Secret key
To capture the above information, you must first create (or already have) an application that is registered with Azure Active Directory. The registered application must have Reader access in the subscription. You can then enter the required information about the application when configuring the SOAP/XML credential in Skylar One. The registered application and the ScienceLogic credential allow Skylar One to retrieve information from Microsoft Azure.
TIP: For details on registering an Azure application, see https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app.
Creating an Active Directory Application in the Azure Portal
When configuring a SOAP/XML credential in Skylar One, you must provide the application ID, subscription ID, tenant ID, and secret key of an application that is registered with Azure Active Directory. You will use this registered application to authenticate your Azure account.
You must have Service Administrator rights to create an Azure Active Directory application.
To create an application in Azure and register it with Azure Active Directory:
- Log in to the Azure portal and type "active directory" in the Search field at the top of the window.
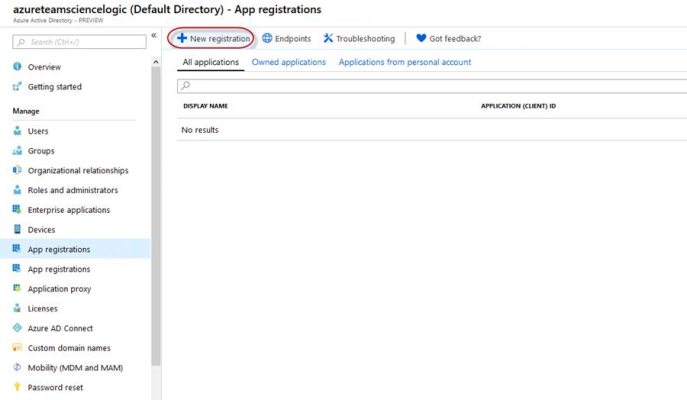
- From the search results, select Azure Active Directory, and then click App registrations. The App registrations page appears:
- Click the button.
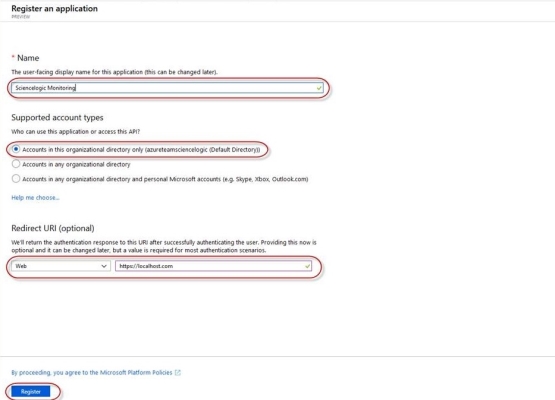
- When the Register an application page appears, enter your application's registration information:
- Name. Type a name for the application.
- Supported account types. Select Accounts in this organizational directory only.
- Redirect URI (optional). Select Web in the drop-down menu and type a valid URL.
- Click the button. A message appears confirming that your application was added.
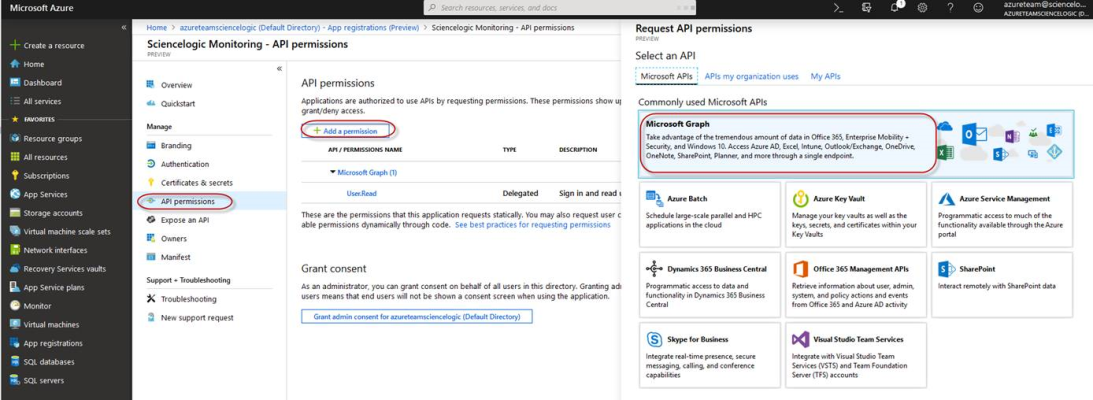
Adding Microsoft Graph APIs Permissions to the Application
By default, any new Application has Microsoft Graph API permission. At a minimum, the Microsoft Graph APIs must have permission to directly read data.
To add the Microsoft Graph APIs:
- In the Search field of the Azure portal (https://portal.azure.com), type "active directory".
- Click , and then click on the name of the Azure Active Directory application you will use to authenticate your Azure account.
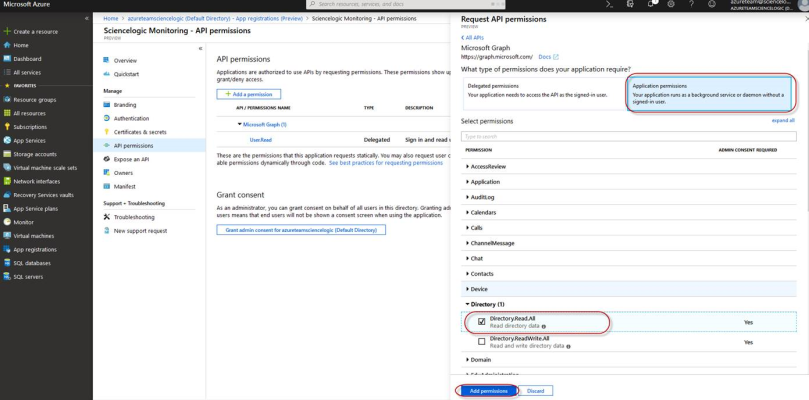
- Click API Permissions, and then click . Next, select the Microsoft Graph option.
- In the Request API permissions pane, under Select permissions, click the arrow next to Directory to open the submenu and select the checkbox for Directory.Read.all permission.
- After you have added the Read directory data, in the API permissions page, click the button.
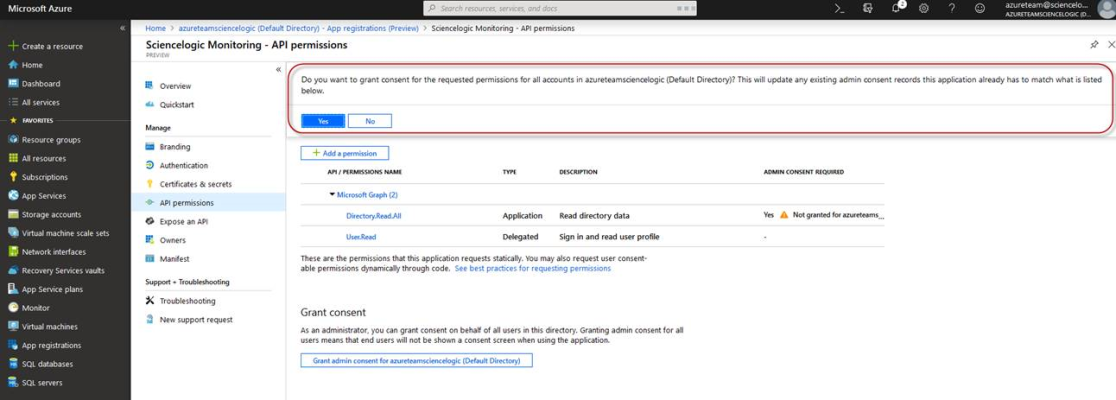
- Click .
- A pop-up window appears asking if you grant consent for the required permissions for all accounts in your directory. Click .
Generating the Secret Key
When configuring a SOAP/XML credential for Azure in Skylar One, you need to provide a secret key for the Azure Active Directory application that you will use to authenticate your account.
To generate a secret key:
- Log in to the Azure portal at https://portal.azure.com, and type "active directory" in the Search field at the top of the window.
- From the search results, select Azure Active Directory, and then click App registrations.
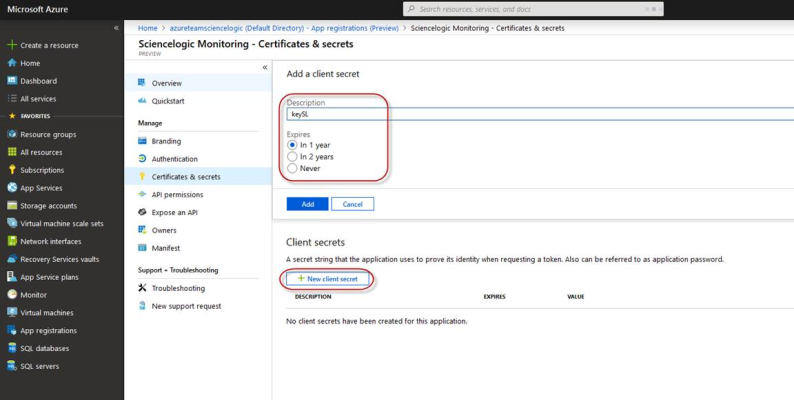
- Select the app and then click .
- In the Client secrets pane, click .
- In the Add a client secret pane, type a name in the Description field and select a duration in the Expires field.
- Click to generate the secret key. A new key value displays in the Client secrets pane.
- Copy and save the key value.
Locating the Application ID and Tenant ID
When configuring a SOAP/XML credential for Azure in Skylar One, you need to provide the Application ID of the Azure Active Directory application you will use to authenticate your Azure account.
To locate the Application ID:
- Log in to the Azure portal at https://portal.azure.com, and type "active directory" in the Search field at the top of the window.
- From the search results, select Azure Active Directory, and then click App registrations.
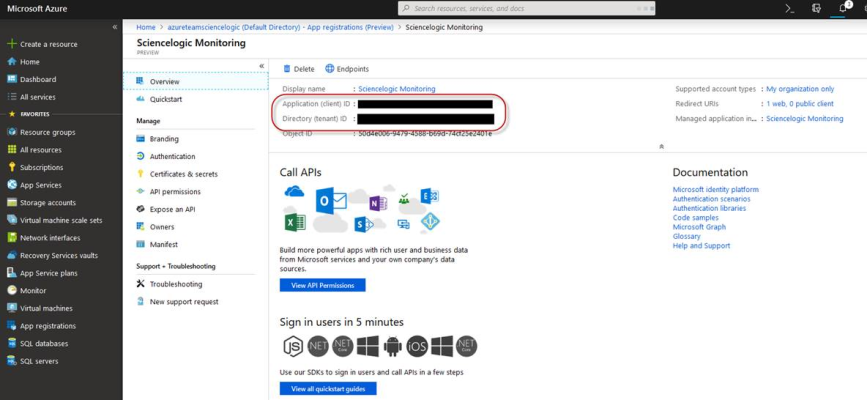
- Click the name of the Active Directory application you will use to authenticate your Azure account. The Application ID and Tenant ID appear in the Overview section.
- Copy and save the values in the corresponding credential fields.
Locating the Subscription ID
If you are monitoring only a single Azure subscription, you must provide the Subscription ID of the Azure Active Directory application you will use to authenticate your account when you configure your SOAP/XML credential for Azure in Skylar One.
If you are monitoring an account with multiple child subscriptions, you can skip this section.
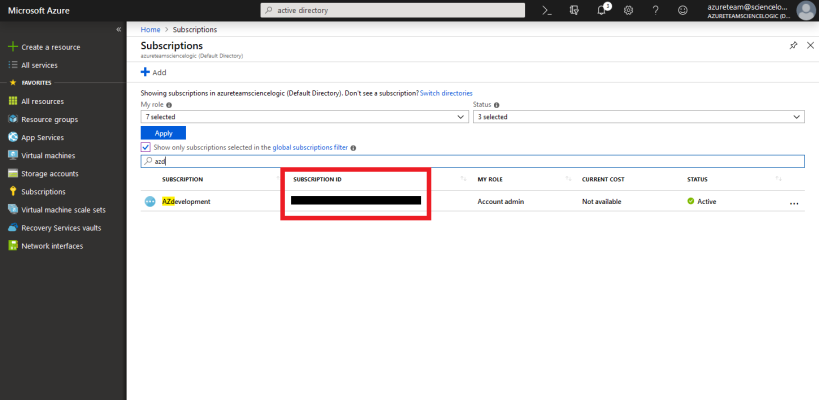
To locate the Subscription ID:
- In the left pane of the Azure portal (https://portal.azure.com), click .
- Copy and save the Subscription ID of the subscription where you created the Azure Active Directory application you will use to authenticate your account.
Adding Reader Access to the Active Directory Application
To allow ScienceLogic to access your Azure account, you must specify the type of access the user whose information you will use in your SOAP/XML credential has to the Active Directory application used to authenticate your account. Use the Reader access role, which is a read-only user that can view everything but cannot make changes.
To specify the access role to the Azure Active Directory application:
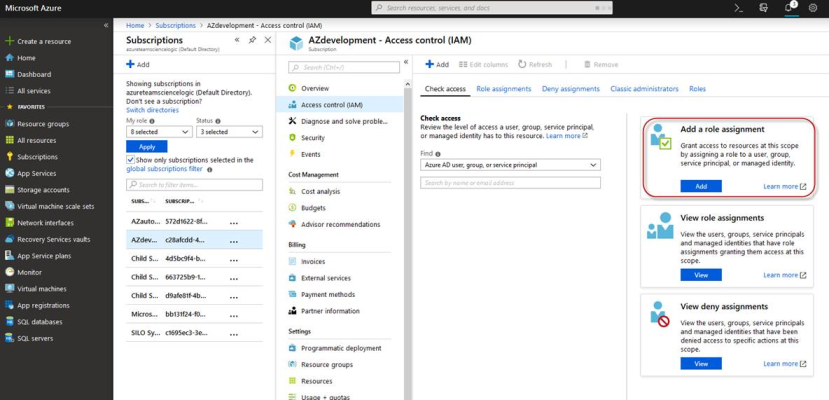
- In the left pane of the Azure Portal (https://portal.azure.com), click .
- Click the name of your subscription, and then click .
- In the Access Control (IAM) pane, click the button in the Add a role assignment section.
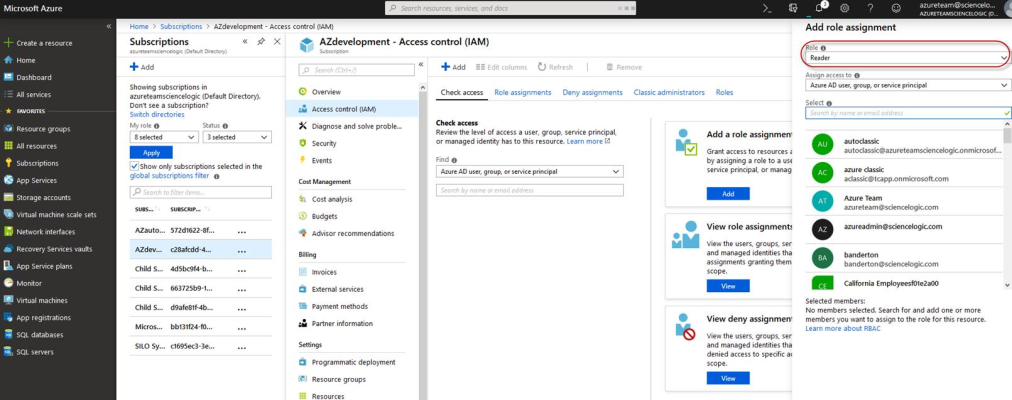
- In the Add a role assignment pane, select Reader in the Role field.
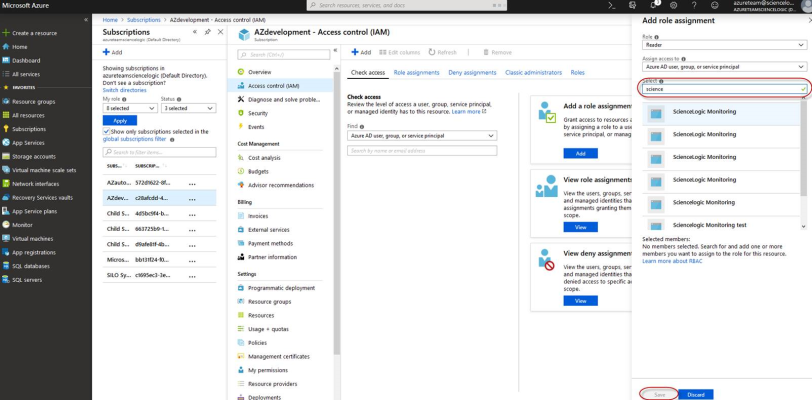
- In the Select field, type the name of the Azure Active Directory application you will use to authenticate your account.
- Select the application from the search results and click .
Setting Up a Proxy Server
Depending on your needs, you can optionally enable Skylar One to connect to Azure through a third-party proxy server such as SQUID. With this configuration, Skylar One connects to the proxy server, which then connects to Azure. Azure relays information to the proxy server and Skylar One then retrieves that information from the proxy.
You can connect to Azure via a proxy server regardless of whether you are monitoring a single subscription or an account with multiple child subscriptions. You can connect to Microsoft Azure, Microsoft Azure Government, and Microsoft Azure Germany and China regions via a proxy server.
The "Microsoft: Azure" PowerPack is certified to work with SQUID version 3.5.12 proxy servers.
If you choose to use a proxy server, configure the third-party proxy server based on the third-party documentation. Depending on the type of authentication you require, you might need to specify a user name and password for the proxy server configuration. Also, make a note of the port you opened for the configuration, as this information is needed when creating the SOAP/XML credential.
Network Requirements
The following URLs need to be whitelisted to allow communication from the collector to the Azure APIs.
-
Commercial Portal (portal.azure.com)
-
https://management.core.windows.net/
-
https://management.azure.com
-
https://login.microsoftonline.com/{tenant_id}/oauth2/v2.0/token
-
https://graph.microsoft.com/v1.0/
-
https://batch.core.windows.net/
-
https://*.batch.azure.com
-
https://*.table.core.windows.net
-
-
US Government Portal (portal.azure.us)
-
https://management.core.usgovcloudapi.net/
-
https://batch.core.usgovcloudapi.net
-
https://*.batch.usgovcloudapi.net
-
https://management.usgovcloudapi.net/
-
https://graph.microsoft.us
-
https://login.microsoftonline.us/{tenant_id}/oauth2/v2.0/token
-
https://*.table.core.usgovcloudapi.net
-
-
China Portal (portal.azure.cn)
-
https://management.core.chinacloudapi.cn
-
https://batch.core.chinacloudapi.cn/
-
https://*.batch.chinacloudapi.cn
-
https://management.chinacloudapi.cn
-
https://login.chinacloudapi.cn/{tenant_id}/oauth2/v2.0/token
-
https://microsoftgraph.chinacloudapi.cn
-
https://*.table.core.chinacloudapi.cn
-
Creating an Azure Credential for Use in Guided Discovery
To configure Skylar One to monitor Microsoft Azure, you must first create an Azure credential. This credential allows the Dynamic Applications in the "Microsoft: Azure" PowerPack to connect with the Azure Active Directory Application.
Skylar One includes an Azure credential type that you can use to connect with the Azure service during guided discovery. This credential type uses field names and terminology that are specific to the Azure service.
Alternatively, you could monitor Azure using a generic SOAP/XML credential that does not include Azure-specific fields. For more information, see
Currently, this process does not support discovery for Government, Germany or China accounts because the required HTTP headers cannot be added. ScienceLogic recommends creating the credentials for these accounts using the generic SOAP/XML credential for Azure.
To define an Azure-specific credential:
- Go to the Credentials page (System > Manage > Credentials).
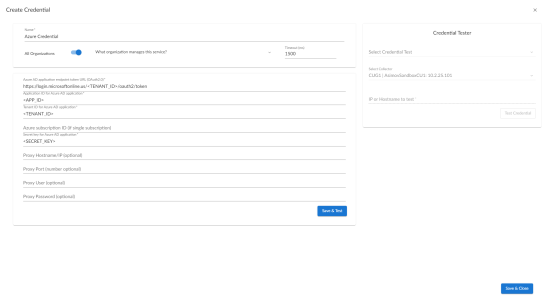
- Click the button and then select Create Azure Credential. The Create Credential modal page appears:
- Supply values in the following fields:
- Name. Name of the credential. Can be any combination of alphanumeric characters.
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Timeout (ms). Time, in milliseconds, after which Skylar One will stop trying to communicate with the device from which you want to retrieve data.
- Azure AD application endpoint token URL (OAuth2.0). The AD application endpoint token URL for the Azure Active Directory application.
- Application ID for Azure AD application. The Application ID for the Azure Active Directory application.
- Tenant ID for Azure AD application. The Tenant ID for the Azure Active Directory application.
- Azure subscription ID (if single subscription). The subscription ID for the Azure Active Directory application. This field is required only if you are monitoring a single Azure subscription.
- Secret key for Azure AD application. The secret key for the Azure Active Directory application.
Proxy Settings
If you use a proxy server in front of the Azure Active Directory applications you want to communicate with, enter values in these fields. Otherwise, you can skip these fields.
- Proxy Hostname/IP. The host name or IP address of the proxy server.
- Proxy Port. Port on the proxy server to which you will connect.
- Proxy User. Username to use to access the proxy server.
- Proxy Password. Password to use to access the proxy server.
- Click .
If you would like to test your credential using the Credential Tester panel, click . For detailed instructions on using the Credential Tester panel, see the Testing the Azure Credential section.
Testing the Azure Credential Using the Credential Tester Panel
The "Microsoft: Azure" PowerPack includes a Credential Test for Microsoft Azure. Credential Tests define a series of steps that Skylar One can execute on demand to validate whether a credential works as expected.
To test the Azure credential using the Credential Tester panel:
- After defining an Azure credential, click the button. This activates the Credential Tester fields.
- In the Credential Tester panel, supply values in the following fields:
- Select Credential Test. Select a credential test to run. This drop-down list includes the ScienceLogic Default Credential Tests, credential tests included in any PowerPacks that have been optionally installed on your system, and credential tests that users have created on your system.
- Select Collector. Select the All-In-One Appliance or Data Collector that will run the test.
- IP or Hostname to test. Type a hostname or IP address that will be used during the test. For example, if you are testing an SNMP credential, the hostname/IP address you supply will be used to perform a test SNMP request.
- Click button to run the credential test. The Testing Credential window appears.
- Step. The name of the step.
- Description. A description of the action performed during the step.
- Log Message. The result of the step for this execution of the credential test.
- Status. Whether the result of this step indicates the credential and/or the network environment is configured correctly (Passed) or incorrectly (Failed).
- Step Tip. Mouse over the question mark icon (
 ) to display the tip text. The tip text recommends what to do to change the credential and/or the network environment if the step has a status of "Failed".
) to display the tip text. The tip text recommends what to do to change the credential and/or the network environment if the step has a status of "Failed".
The Testing Credential window displays a log entry for each step in the credential test. The steps performed are different for each credential test. The log entry for each step includes the following information:
Creating a SOAP/XML Credential for Azure
If you want to create a SOAP/XML credential without Azure-specific fields, note the application ID, subscription ID, tenant ID, and secret key of the application (that is registered with Azure Active Directory) that you will use to authenticate your Azure account. This credential allows the Dynamic Applications in the "Microsoft: Azure" PowerPack to communicate with your Azure subscriptions.
If you want to connect to your Azure account through a third-party proxy server, you must also add the proxy information in the credential. This applies to Microsoft Azure, Microsoft Azure Government, and the Microsoft Azure German and Chinese regions.
The "Microsoft: Azure" PowerPack includes multiple sample credentials you can use as templates for creating SOAP/XML credentials for Azure. They are:
- Azure Credential - China, for users who connect to an Azure data center in a Chinese region
- Azure Credential - Germany, for users who connect to an Azure data center in a German region (requires a subscription in Germany or Europe)
- Azure Credential Gov Example, for users who subscribe to Microsoft Azure Government
- Azure Credential Proxy Example, for users who connect to Azure through a third-party proxy server
- Azure Credential - Example, for all other users.
NOTE: If you are using a Skylar One system prior to version 11.1.0, the new user interface does not include the Duplicate option for sample credential(s). ScienceLogic recommends that you use the classic user interface and the Save As button to create new credentials from sample credentials. This will prevent you from overwriting the sample credential(s).
To create a SOAP/XML credential for Azure:
- Go to the Credentials page (Manage > Credentials).
- Locate the sample credential you want to use, click its icon (
 ) and select Duplicate. A copy of the credential appears.
) and select Duplicate. A copy of the credential appears. - Click the icon (
 ) for the credential copy and select Edit. The Edit Credential modal page appears.
) for the credential copy and select Edit. The Edit Credential modal page appears.
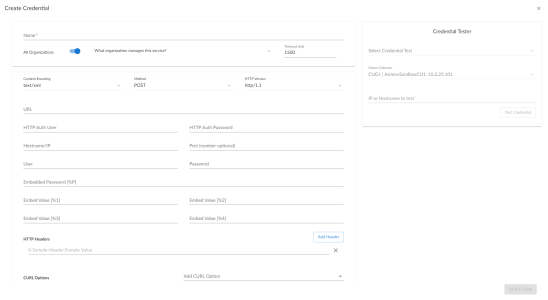
- Supply values in the following fields:
- Name. Type a new name for the Azure credential.
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Timeout (ms). Type "120".
- Content Encoding. Select text/xml.
- Method. Select POST.
- HTTP Version. Select HTTP/1.1.
- URL. Type the tenant ID in the appropriate place in the URL provided in the sample credential.
- HTTP Auth User. Leave this field blank.
- HTTP Auth Password. Leave this field blank.
Proxy Settings
- Hostname/IP. If you are connecting to Azure via a proxy server, type the server's hostname or IP address. Otherwise, leave this field blank.
- Port. If you are connecting to Azure via a proxy server, type the port number you opened when setting up the proxy server. Otherwise, leave this field blank.
- User. If you are connecting to Azure via a proxy server using basic authentication, type the server's administrator username. Otherwise, leave this field blank.
- Password. If you are connecting to Azure via a proxy server using basic authentication, type the server's administrator password. Otherwise, leave this field blank.
SOAP Options
- Embedded Password [%P]. Type the secret key for the Azure Active Directory application.
- Embed Value [%1]. Type the Application ID for the Azure Active Directory application.
- Embed Value [%2]. Type the Tenant ID for the Azure Active Directory application.
- Embed Value [%3]. If you are monitoring only a single Azure subscription, type the Subscription ID for the Azure Active Directory application. If you are monitoring multiple subscriptions, leave this field blank.
- Embed Value [%4]. Leave this field blank.
HTTP Headers
- HTTP Headers. Leave this field blank, unless one of the following scenarios applies to you:
- If you are using Microsoft Azure Government, this field contains the text "AZGOV".
- If you are monitoring Microsoft Azure resources in Germany, this field contains the text "AZGER".
- If you are monitoring Microsoft Azure resources in China, this field contains the text "AZCHINA".
- If you would like to enable extended logging, enter "LOGGING" in to a header field. The log file is located at /data/logs/azure.log in the data collector.
- SSL certification verification is enabled by default, but you can disable it in a header field by entering "VERIFY:FALSE".
cURL Options
- CURL Options. Do not make any selections in this field.
- Click .
If you would like to test your credential using the Credential Tester panel, click . For detailed instructions on using the Credential Tester panel, see the Using the Credential Tester Panel section.
Load-Balancing an Account with Multiple Subscriptions
When monitoring an account with multiple child subscriptions, instead of discovering all child subscriptions in a single dynamic component map under their parent account, you can load-balance subscriptions and their components across multiple Data Collectors.
To do this:
- The Collector Group that discovers a group of subscriptions can contain only one Data Collector. You cannot use multiple Data Collectors to discover the Azure components in a single dynamic component map or discover the same device in multiple dynamic component maps.
- To group multiple Azure subscriptions into a single dynamic component map, you need to create a shared credential for that group of subscriptions.
- To create the credential:
- Perform all of the steps in the section on Configuring an Azure Active Directory Application.
- Align each subscription in the group with the same application that you registered with Azure AD.
- In the credential, enter the application ID in the Embed Value [%1] field.
- In the credential, leave the Embed Value [%3] field blank.
- During discovery, use this credential to discover the group of subscriptions.
- During discovery, specify the Data Collector you want to use for the group of subscriptions.
- The discovered subscriptions will reside in a common dynamic component map.
- Repeat these steps for each group of subscriptions.
Testing the Azure Credential
You can test a credential from the Credentials page using a predefined credential test.
To run a credential test from the Credentials page:
- Go to the Credentials page (Manage > Credentials).
- Click the Actions button (
 ) of the credential that you want to test, and then select Edit/Test.
) of the credential that you want to test, and then select Edit/Test. - The Credential Tester modal page appears. Fill out the following fields on this page:
- Select Credential Test. Select a credential test to run. This drop-down list includes the ScienceLogic Default Credential Tests, credential tests included in any PowerPacks that have been optionally installed on your system, and credential tests that users have created on your system.
- Collector. Select the All-In-One Appliance or Data Collector that will run the test.
- IP or Hostname to Test. Type a hostname or IP address that will be used during the test. For example, if you are testing an SNMP credential, the hostname/IP address you supply will be used to perform a test SNMP request.
- Click button to run the credential test. The Credential Test starts and the Testing Completed modal displays the results.
The Testing Completed window displays a log entry for each step in the credential test. The steps performed are different for each credential test.
Creating a SOAP/XML Credential for Azure in the Skylar One Classic User Interface
After you note the application ID, subscription ID, tenant ID, and secret key of the application (that is registered with Azure Active Directory) that you will use to authenticate your Azure account, you can create a SOAP/XML credential for Azure in Skylar One. This credential allows the Dynamic Applications in the "Microsoft: Azure" PowerPack to communicate with your Azure subscriptions.
If you want to connect to your Azure account through a third-party proxy server, you must also add the proxy information in the credential. This applies to Microsoft Azure, Microsoft Azure Government, and the Microsoft Azure German and Chinese regions.
The "Microsoft: Azure" PowerPack includes multiple sample credentials you can use as templates for creating SOAP/XML credentials for Azure. They are:
- Azure Credential - China, for users who connect to an Azure data center in a Chinese region
- Azure Credential - Germany, for users who connect to an Azure data center in a German region (requires a subscription in Germany or Europe)
- Azure Credential Gov Example, for users who subscribe to Microsoft Azure Government
- Azure Credential Proxy Example, for users who connect to Azure through a third-party proxy server
- Azure Credential - Example, for all other users.
To create a SOAP/XML credential for Azure:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the sample credential you want to use and then click its wrench icon (
 ). The Edit SOAP/XML Credential modal page appears.
). The Edit SOAP/XML Credential modal page appears. - Enter values in the following fields:
Basic Settings
- Profile Name. Type a new name for the Azure credential.
- Content Encoding. Select text/xml.
- Method. Select POST.
- HTTP Version. Select HTTP/1.1.
- URL. Type the tenant ID in the appropriate place in the URL provided in the sample credential.
- HTTP Auth User. Leave this field blank.
- HTTP Auth Password. Leave this field blank.
- Timeout (seconds). Type "120".
Proxy Settings
- Hostname/IP. If you are connecting to Azure via a proxy server, type the server's hostname or IP address. Otherwise, leave this field blank.
- Port. If you are connecting to Azure via a proxy server, type the port number you opened when setting up the proxy server. Otherwise, leave this field blank.
- User. If you are connecting to Azure via a proxy server using basic authentication, type the server's administrator username. Otherwise, leave this field blank.
- Password. If you are connecting to Azure via a proxy server using basic authentication, type the server's administrator password. Otherwise, leave this field blank.
CURL Options
- CURL Options. Do not make any selections in this field.
SOAP Options
- Embedded Password [%P]. Type the secret key for the Azure Active Directory application.
- Embed Value [%1]. Type the Application ID for the Azure Active Directory application.
- Embed Value [%2]. Type the Tenant ID for the Azure Active Directory application.
- Embed Value [%3]. If you are monitoring only a single Azure subscription, type the Subscription ID for the Azure Active Directory application. If you are monitoring multiple subscriptions, leave this field blank.
- Embed Value [%4]. Leave this field blank.
HTTP Headers
- HTTP Headers. Leave this field blank, unless one of the following scenarios applies to you:
- If you are using Microsoft Azure Government, this field contains the text "AZGOV".
- If you are monitoring Microsoft Azure resources in Germany, this field contains the text "AZGER".
- If you are monitoring Microsoft Azure resources in China, this field contains the text "AZCHINA".
- If you would like to enable extended logging, enter "LOGGING" in to a header field. The log file is located at /data/logs/azure.log in the data collector.
- SSL certification verification is enabled by default, but you can disable it in a header field by entering "VERIFY:FALSE".
- Click .
- In the confirmation message, click .
Load-Balancing an Account with Multiple Subscriptions
When monitoring an account with multiple child subscriptions, instead of discovering all child subscriptions in a single dynamic component map under their parent account, you can load-balance subscriptions and their components across multiple Data Collectors.
To do this:
- The Collector Group that discovers a group of subscriptions can contain only one Data Collector. You cannot use multiple Data Collectors to discover the Azure components in a single dynamic component map or discover the same device in multiple dynamic component maps.
- To group multiple Azure subscriptions into a single dynamic component map, you need to create a shared credential for that group of subscriptions.
- To create the credential:
- Perform all of the steps in the section on Configuring an Azure Active Directory Application.
- Align each subscription in the group with the same application that you registered with Azure AD.
- In the credential, enter the application ID in the Embed Value [%1] field.
- In the credential, leave the Embed Value [%3] field blank.
- During discovery, use this credential to discover the group of subscriptions.
- During discovery, specify the Data Collector you want to use for the group of subscriptions.
- The discovered subscriptions will reside in a common dynamic component map.
- Repeat these steps for each group of subscriptions.
Testing the Azure Credential in the Skylar One Classic User Interface
The "Microsoft: Azure" PowerPack includes a Credential Test for Microsoft Azure. Credential Tests define a series of steps that Skylar One can execute on demand to validate whether a credential works as expected.
The "Azure Credential Test - ARM" can be used to test a SOAP/XML credential for monitoring Azure using the Dynamic Applications in the "Microsoft: Azure" PowerPack. The "Azure Credential Test - ARM" performs the following steps:
- Test Port Availability. Performs an NMAP request to test the availability of the Azure endpoint HTTPS port.
- Test Name Resolution. Performs an nslookup request on the Azure endpoint.
- Make connection to Azure account. Attempts to connect to the Azure service using the account specified in the credential.
- Validate Azure Microsoft Graph Permission. Verifies that the Azure Active Directory application has Microsoft Graph API permissions.
- Validate Azure subscription assignments. Verifies that the Azure Active Directory application is assigned to the subscription.
To test the Azure credential:
- Go to the Credential Test Management page (System > Customize > Credential Tests).
- Locate the Azure Credential Test - ARM and click its lightning bolt icon (
 ). The Credential Tester modal page appears:
). The Credential Tester modal page appears: - Supply values in the following fields:
- Test Type. This field is pre-populated with the credential test you selected.
- Credential. Select the credential to test. This drop-down list includes only credentials that you have access to that can be tested using the selected credential test.
- Hostname/IP. Leave this field blank.
- Collector. Select the All-In-One Appliance or Data Collector that will run the test.
- Click the button. The Test Credential window appears, displaying a log entry for each step in the credential test. The steps performed are different for each credential test. The log entry for each step includes the following information:
- Step. The name of the step.
- Description. A description of the action performed during the step.
- Log Message. The result of the step for this credential test.
- Status. Whether the result of this step indicates the credential or the network environment is configured correctly (Passed) or incorrectly (Failed).
- Step Tip. Mouse over the question mark icon (
 ) to display the tip text. The tip text recommends what to do to change the credential or the network environment if the step has a status of "Failed".
) to display the tip text. The tip text recommends what to do to change the credential or the network environment if the step has a status of "Failed".