This section describes how to configure Windows Server 2012 and later and Windows desktop systems for monitoring by Skylar One using SNMP.
Use the following menu options to navigate the Skylar One user interface:
- To view a pop-out list of menu options, click the menu icon (
 ).
). - To view a page containing all of the menu options, click the Advanced menu icon (
 ).
).
Configuring WMI on Windows 2012 and Later Servers
Windows Management Instrumentation, or WMI, is the infrastructure that provides information about operations and management on Windows-based operating systems. WMI can be configured to respond to remote requests from Skylar One.
To configure a Windows device to respond to remote requests, you must perform the following steps:
- Configure Services
- Configure the Windows Firewall
- Configure a user account and permissions
- Configuring a fixed port for WMI
Most remote requests can be performed by a standard (non-administrator) user account that has been granted specific privileges. However, some requests can be performed only by a user with elevated permissions. For requests performed by Skylar One to a Windows server, the following users have elevated permissions:
- The default "Administrator" user account.
- A user account in the Administrators group on a Windows server that has User Account Control disabled.
- A user account in the Administrators group on a Windows server where a registry entry has been added to disable remote User Account Control filtering.
For a list of WMI classes that require elevated permissions, see http://msdn.microsoft.com/en-us/library/windows/desktop/aa826699%28v=vs.85%29.aspx
For a list of default WMI Dynamic Applications that require elevated permissions, see the chapter on Dynamic Applications for Windows Devices.
Step 1: Configuring Services
The following services must be running for a Windows device to respond to remote WMI requests:
ScienceLogic recommends you set all these services to automatically start.
- COM+ Event System
- DCOM Server Process Launcher
- Remote Procedure Call (RPC)
- Remote Registry
- Server
- Windows Management Instrumentation
To ensure a service is running, perform the following steps:
- In the left pane of the Server Manager window, expand the Configuration section, and then select Services.
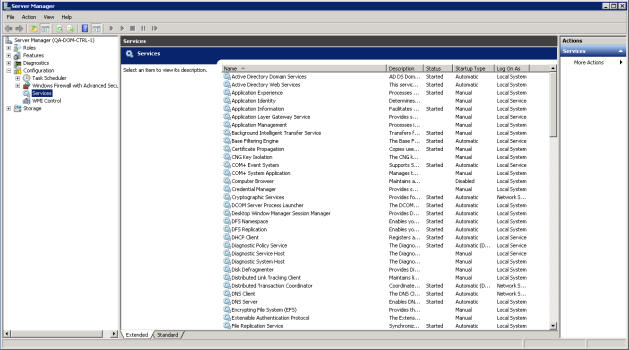
- For each required service, the Startup Type column should display Automatic. If a service does not have a Startup Type of Automatic, double-click on that service. The Properties window for that service is displayed:
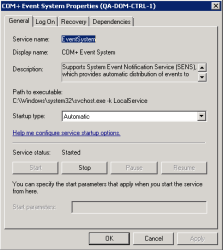
- In the Startup Type field, select Automatic.
- Click the button.
- If the service has not already started, click the button.
Step 2: Configuring the Windows Firewall
To configure Windows Firewall to accept remote WMI requests:
- Click the magnifying glass icon in the bottom-left corner and type "Command Prompt" in the Search Windows field.
- Execute the following two commands in the Command Prompt window:
netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes
netsh advfirewall firewall set rule group="remote administration" new enable=yes
- If the result of the second command is "No rules match the specified criteria", run the following two commands:
netsh firewall set service remoteadmin enable
netsh advfirewall firewall set rule group="remote administration" new enable=yes
Step 3: Configuring a User Account and Permissions
There are three ways to configure the user account that Skylar One will use to perform WMI requests:
- To monitor the Windows server using WMI Dynamic Applications that require standard permissions, you can configure a standard user account for use by Skylar One. The user account for use by Skylar One must be included in the Distributed COM Users and Performance Monitor Users groups. (For more information, consult Microsoft's documentation.)
- To monitor the Windows server using WMI Dynamic Applications that require elevated permissions, you can use the default "Administrator" user account. If you use the "Administrator" user account, you do not need to make changes to the User Account Control settings.
- To monitor the Windows server using WMI Dynamic Applications that require elevated permissions, you can also use a user account that is included in the Administrators group. However, you must perform one of the following additional steps to use this type of user account:
- Option 1: Make the user a member of the Distributed COM Users and Performance Monitor Users groups, in addition to the Administrator group. (For more information, consult Microsoft's documentation.)
- Option 2: Configure User Access Control to allow elevated permissions.
Configuring Namespace and DCOM Security Permissions
For each of these methods, you must ensure that the configured Namespace and DCOM security permissions allow that user to perform remote requests.
To configure the Namespace and DCOM security permissions:
- In the left pane of the Server Manager window, expand the Configuration section.
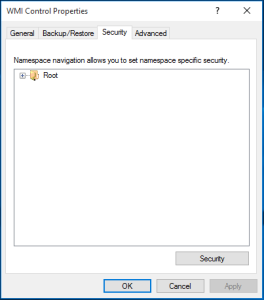
- Right-click on the WMI Control entry and then select Properties.
- In the Security tab, select the Root entry from the navigation pane and then select the button. The Security for Root window appears.
- In the Security for Root window, select the button. The Advanced Security Settings for Root window is displayed:
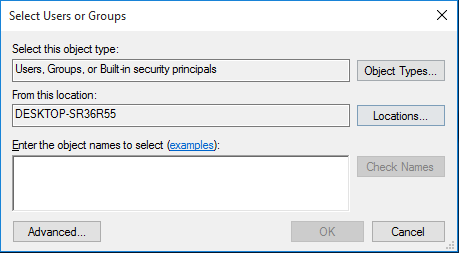
- In the Advanced Security Settings for Root window, click the button. The Select User, Computer, Service Account, or Group window appears.
- In the Enter the object name to select field, enter the name of the user account that Skylar One will use to perform WMI requests or the name of a group that includes that user account.
- Click the button to verify the name and then click the button.
- Select This namespace and subnamespaces in the Apply to field and select the Allow checkbox for all permissions.
- Click the button.
- In the Advanced Security Settings for Root window, click the button.
- Click the button in each open window to exit.
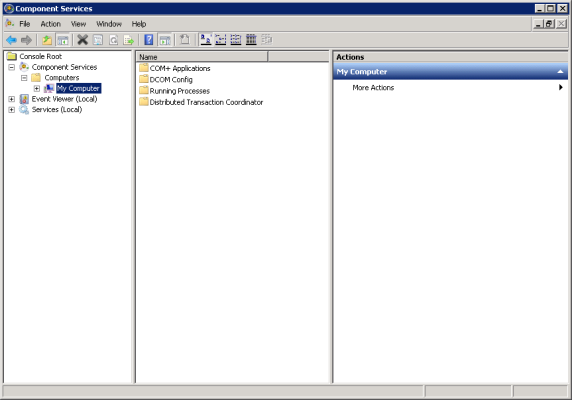
- Go to the Start menu and select .
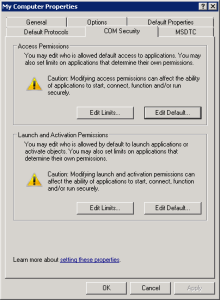
- In the left pane, expand Component Services > Computers. Right-click on My Computer and select Properties. The My Computer Properties window is displayed.
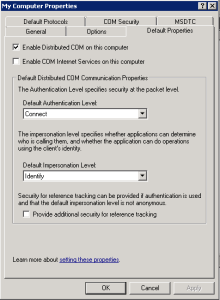
- Ensure that the Enable Distributed COM on this computer checkbox is selected.
- Select Connect in the Default Authentication Level drop-down list.
- Select Identify in the Default Impersonation Level drop-down list.
- If you made changes in the tab, click the button.
- Select the tab:
- Select the button in the Access Permissions pane.
- In the window that appears, click the button. The Select Users, Computers, Service Accounts, or Groups window is displayed.
- Enter the name of the user account that Skylar One will use to perform WMI requests or the name of a group that includes that user account.
- Click the Check Names button to verify the name and then click the button.
- Select the group or user you added in the Group or user names pane and then select the Allow checkbox for all permissions.
- Click the button.
- Click the button in the Access Permissions pane, then repeat steps 16 - 19.
- Click the button in the Launch and Activation Permissions pane, then repeat steps 16 - 19.
- Click the button in the Launch and Activation Permissions pane, then repeat steps 16 - 19.
- Click the button.
- Click in the confirmation window.
Configuring User Account Control to Allow Elevated Permissions
If you want to use WMI Dynamic Applications that require elevated permissions to monitor a Windows server and you are using a user account other than the default "Administrator" user account, you must perform one of the following two tasks:
- Option 1: Disable User Account Control.
- Option 2: Add a registry entry that disables remote User Account Control filtering.
Option 1: Disabling User Account Control
To disable User Account Control:
- Open the Control Panel in Large Icon or Small Icon view.
- Select User Accounts.
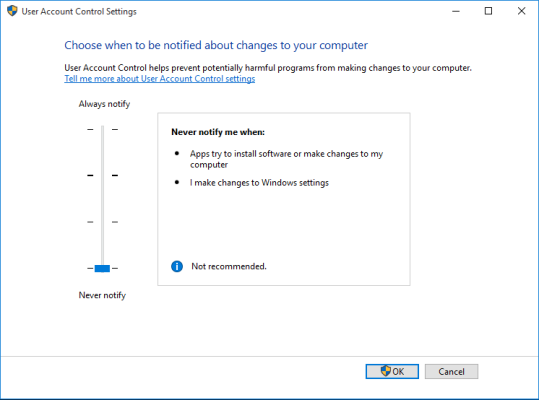
- Select Change User Account Control Settings. The User Account Control Settings window is displayed:
- Move the slider to Never Notify.
- Click the button.
- Restart the Windows server.
Option 2: Adding a Registry Entry that Disables Remote User Account Control Filtering
To add a registry entry that disables remote User Account Control filtering:
- To disable the filter, open a text editor and add the following lines to a new file:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"LocalAccountTokenFilterPolicy"=dword:00000001
- Save the file with a ".reg" extension.
- In Windows Explorer, double click on the .reg file.
- Select in the pop-up window.
Step 4: Configuring a Fixed Port for WMI
Specific ports must be opened to allow WMI monitoring when there is a separate firewall between the Data Collector and the device. This can occur when the default configuration of the Windows Firewall blocks incoming network traffic for the Windows Management Instrumentation (WMI) connection.
For the WMI connection to succeed, the remote machine must permit incoming network traffic on TCP ports 135, 445, and additional dynamically-assigned ports, typically in the range of 1025 to 5000 and 49152 to 65535.
To set up a fixed port for WMI, see the Microsoft documentation on Setting Up a Fixed Port for WMI.
Configuring WMI for Windows Desktop Systems
This section describes how to configure devices that are running a desktop version of the Windows operating system for monitoring by Skylar One using WMI.
Before performing the tasks described in this section, you must know the IP address of each Skylar One appliance in your network. If you have not installed a Skylar One appliance, you must know the future IP address that will be used by each Skylar One appliance.
To be monitored by Skylar One, a Windows device must be running the Windows 7 operating system or later.
TCP/IP must be installed and configured before you can install SNMP on a Windows device.
Windows Management Instrumentation (WMI) is the infrastructure that provides information about operations and management on Windows-based operating systems. WMI can be configured to respond to remote requests from Skylar One. To configure a device running a desktop version of the Windows operating system to respond to remote requests, you must perform the following steps:
- Configure Services
- Configure the Windows Firewall
- Set Default Namespace Security
- Set the DCOM Security Level
- Disable User Account Control
- Configuring a fixed port for WMI
The following instructions describe how to configure WMI on devices running a desktop version of the Windows 10 operating system. For instructions on how to configure WMI on earlier Windows versions, consult Microsoft's documentation.
Step 1: Configuring Services
The following services must be running for a Windows device to respond to remote WMI requests:
ScienceLogic recommends you set all these services to start automatically.
- COM+ Event System
- Remote Access Auto Connection Manager
- Remote Access Connection Manager
- Remote Procedure Call (RPC)
- Remote Procedure Call (RPC) Locator
- Remote Registry
- Server
- Windows Management Instrumentation
- WMI Performance Adapter
- Workstation
To ensure a service is running, perform the following steps:
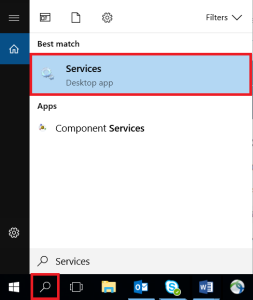
- Click the magnifying glass icon in the bottom-left corner and type "Services" in the Search Windows field.
- Click the Services Desktop app.
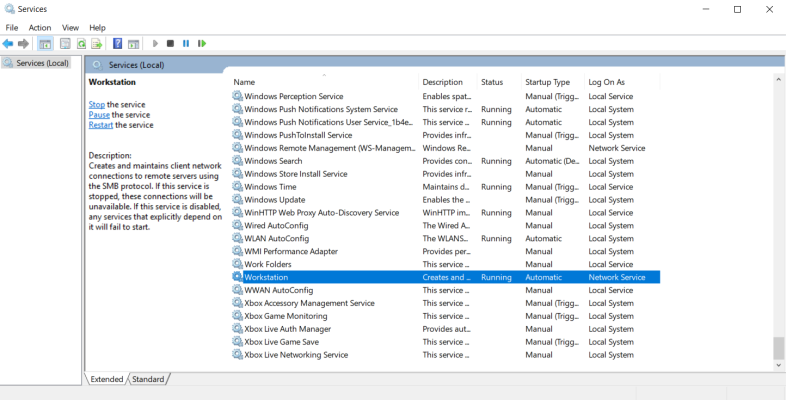
- From the list of services in the right pane, perform the remaining steps for each of the services you want to check. This example uses Workstation. However, you should check each of the following services:
- COM+ Event System
- Remote Access Auto Connection Manager
- Remote Access Connection Manager
- Remote Procedure Call (RPC)
- Remote Procedure Call (RPC) Locator
- Remote Registry
- Server
- Windows Management Instrumentation
- WMI Performance Adapter
- Workstation
- Double-click the name of the service. In this example, we double-clicked Workstation.
- In the Workstation Properties dialog box, click the tab and complete the following field:
- Startup Type. Select Automatic.
- Click the button.
- If the service has not already started, click the button.
- Repeat steps 4-7 for each service.
Step 2: Configuring Windows Firewall
To configure Windows Firewall to accept remote WMI requests:
- Click the magnifying glass icon in the bottom-left corner and type "Command Prompt" in the Search Windows field.
- Execute the following two commands in the Command Prompt window:
netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes
netsh advfirewall firewall set rule group="remote administration" new enable=yes
- If the result of the second command is "No rules match the specified criteria", run the following two commands:
netsh firewall set service remoteadmin enable
netsh advfirewall firewall set rule group="remote administration" new enable=yes
Step 3: Setting the Default Namespace Security
To set the default namespace security, perform the following steps:
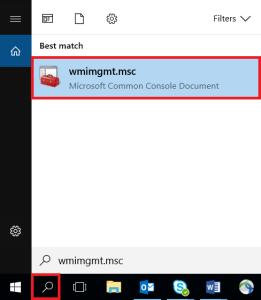
- Click the magnifying glass icon in the bottom-left corner and type "Services" in the Search Windows field.
- Click the wmimgmt.msc Microsoft Common Console Document.
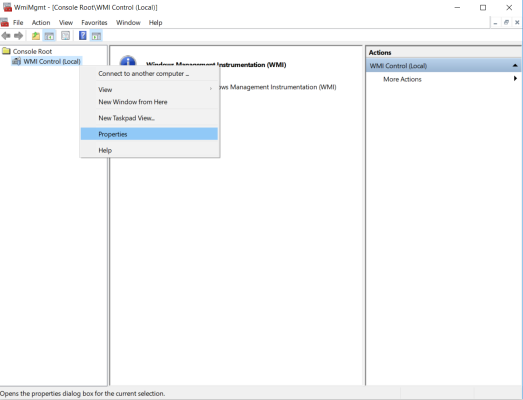
- In the WmiMgmt window, right click WMI Control (Local) and select Properties.
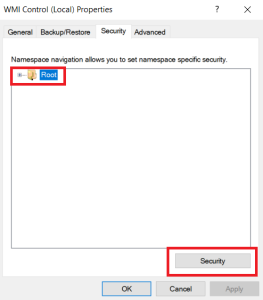
- In the WMI Control (Local) Properties window, click the tab, click Root, and then click the button.
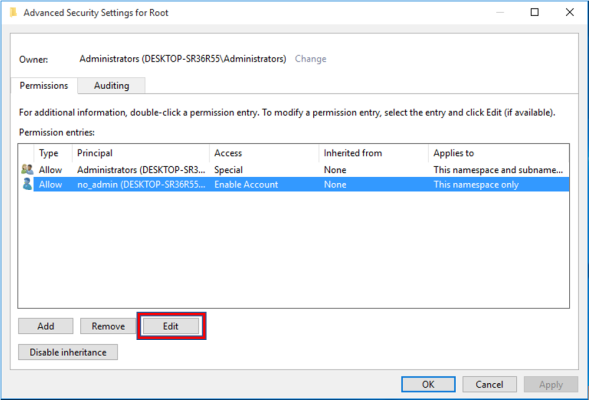
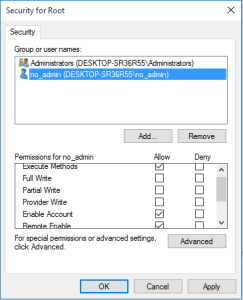
- In the Security for Root window, click Administrators, and then click the button.
- In the Advanced Security Settings for Root window, click Administrators, and then click the button.
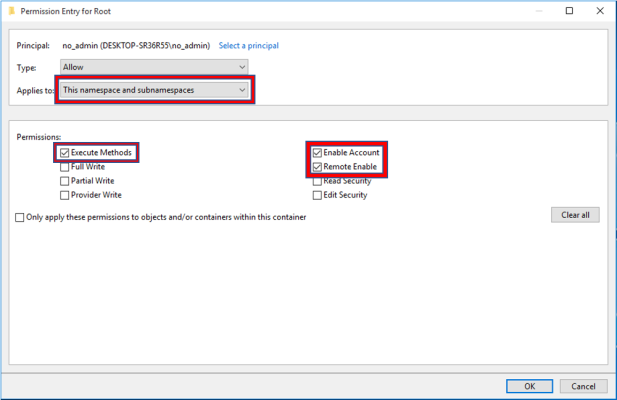
- In the Permission Entry for Root window, enter the following:
- Type. Select Allow.
- Applies to. Select This namespace and subnamespaces.
- Permissions. Select the Execute Methods, Full Write, Partial Write, Provider Write, Enable Account, Remote Enable, Read Security, and Edit Security checkboxes.
- Click OK in this window and the following windows, and then close the WmiMgmt window.
Step 4: Setting the DCOM Security Level
To set the DCOM Security Level, perform the following steps:
- Click the magnifying glass icon in the bottom-left corner and type "dcomcnfg.exe" in the Search Windows field.
- Click the dcomcnfg.exe command.
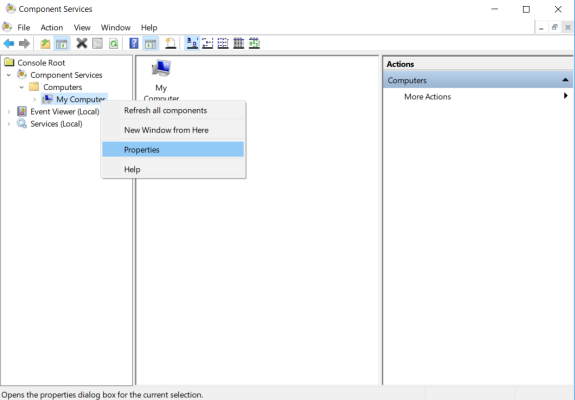
- In the Component Services window, expand Component Services > Computers, right-click My Computer, and then select Properties.
- In the My Computer Properties window, click the tab and then complete the following fields:
- Enable Distributed COM on this computer. Select this checkbox.
- Default Authentication Level. Select Connect.
- Default Impersonation Level. Select Identify.
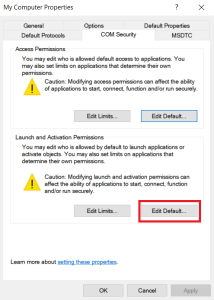
- In the My Computer Properties window, click the tab. Under Launch and Activation Permissions, click the button.
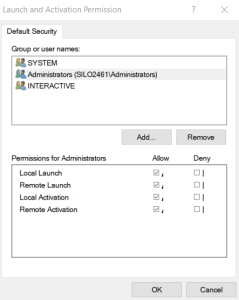
- In the Launch and Activation Permission window, select the following:
- Group or user names. Select Administrators.
- Permissions for Administrators. Set Local Launch, Remote Launch, Local Activation, and Remote Activationto Allow.
- Click .
- In the My Computer Properties window, in the Launch and Activation Permissions pane, click the button.
- In the Launch Permission window, select the following:
- Group or user names. Select Administrators.
- Permissions for Administrators. Set Local Launch, Remote Launch, Local Activation, and Remote Activationto Allow.
- Click OK in this window and the following windows, and then close the Component Services window.
- Restart the computer to save the settings.
Step 5: Disabling User Account Control
To monitor a device running Windows 7, 8, or 10, you must perform the following additional steps to disable the User Account Control (UAC) filter for remote logins:
- Use a text editor such as Notepad to create a new file.
- Include the following in the file.:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"LocalAccountTokenFilterPolicy"=dword:00000001
- Save the file with a name of your choice, like disableUAC.reg, to the directory of your choice. Make sure to save the new file with the .reg suffix.
- In Windows Explorer, double click on the .reg file to execute it.
Step 6: Configuring a fixed port for WMI
Specific ports must be opened to allow WMI monitoring when there is a separate firewall between the Data Collector and the device. This can occur when the default configuration of the Windows Firewall blocks incoming network traffic for the Windows Management Instrumentation (WMI) connection.
For the WMI connection to succeed, the remote machine must permit incoming network traffic on TCP ports 135, 445, and additional dynamically-assigned ports, typically in the range of 1025 to 5000 and 49152 to 65535.
To set up a fixed port for WMI, see the Microsoft documentation on Setting Up a Fixed Port for WMI.