Active Directory Authentication
With Active Directory Authentication the requestor will authenticate by using the Kerberos protocol.
When using Active Directory authentication it should be noted that if your Skylar One collector is not already configured for Kerberos authentication, it will be automatically configured at collection time.
This means that if your credential references an active directory host & domain combination not already present in your /etc/krb5.conf file an entry will be automatically added. Please take care to enter these details correctly as incorrect entries may have to be manually removed.
Active Directory authentication will also generate a Kerberos ticket on the collector file system. This ticket will be refreshed hourly.
Active Directory authentication is only supported in Skylar One >= 12.1.0
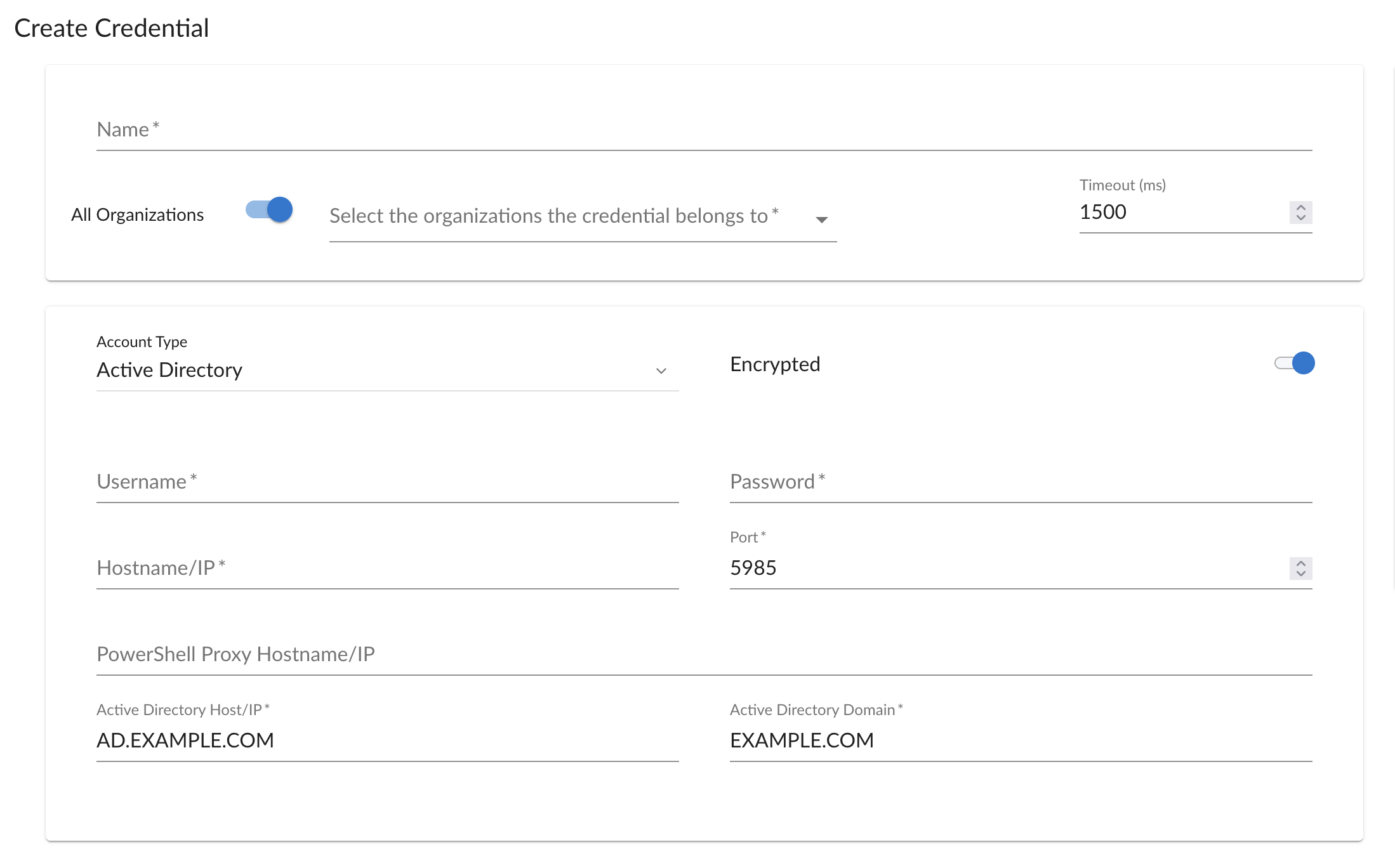
The fields available with Active Directory Authentication are:
Account Type
The type of account specified in the credential. Accounts can be of type Local or Active Directory.
Hostname/IP
The device hostname or IP address for the connection. This field is required.
Username
The username for an SSH or user account on the device.
Password
The password for an SSH or user account on the device.
Timeout (ms)
The timeout value to use when authenticating with the credential. The value specified should be in milliseconds.
Encrypted
If the communication with remote hosts will make use of HTTPS or not.
Port
The port number for the WinRM connection. Default:
5986. This field is required.Proxy Hostname/IP
This field is not supported.
Active Directory Hostname/IP
The Active Directory hostname.
Domain
The Active Directory domain you wish to authenticate with.
Note
Active Directory Hostname should be fully resolvable.
Note
If you make use of self signed certificates when using Encrypted communication between hosts, you will have to anchor an intermediate or root certificate to the Skylar One collector’s trust bundle. In Skylar One this is located at /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem.
Note
Powershell Proxy Hostname/IP field is not supported.