Use the following menu options to navigate the Skylar One user interface:
- To view a pop-out list of menu options, click the menu icon (
 ).
). - To view a page containing all of the menu options, click the Advanced menu icon (
 ).
).
The following sections describe how to configure Cisco UC Voice Operating System (VOS) applications for monitoring by Skylar One using the "Cisco: UC VOS Applications" PowerPack:
Configuring Cisco UC VOS Applications for Monitoring
Before performing the other tasks in this
Configuring SNMP for Cisco VOS Applications
Skylar One uses SNMP to collect information about the following Cisco VOS applications:
- Cisco Contact Center Express (CCX)
- Cisco Unity Connection (CUC) servers
- Cisco Hosted Collaboration Mediation for Fulfillment (HCM-F)
- Cisco HCS Intelligent Loader
- Cisco IM & Presence (IM&P) servers (optional)
- Cisco Emergency Responder
- Cisco Prime Collaboration Deployment (PCD) servers (optional, but recommended)
- Cisco SocialMiner
To configure SNMP for Cisco VOS applications:
- Log in as an administrative user to the command-line interface of the Cisco VOS application that you want to monitor. You can also use SSH to connect to the application.
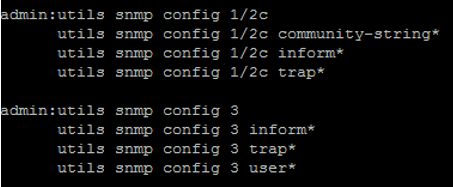
- Run the following command with additional parameters as needed:
utils snmp config
- When prompted, add additional SNMP information. The following image displays additional configuration parameters, based on SNMP version (version 1 or 2, or version 3):
- For additional SNMP configuration commands and instructions, see the Cisco Command Line Interface Reference Guide.
Creating the User Account for the Platform Administrative Web Services (PAWS) API
To get access to the Platform Administrative Web Services (PAWS) API, you can create a new user account by using the command-line interface on the console of the Cisco VOS application that you want to monitor. You can also use SSH to connect to the application.
You can then use this user account to connect to the following Cisco VOS applications:
- Cisco Contact Center Express (CCX)
- Cisco Unity Connection (CUC) servers
- Cisco Hosted Collaboration Mediation for Fulfillment (HCM-F)
- Cisco HCS Intelligent Loader
- Cisco IM & Presence (IM&P) servers
- Cisco Unified Communications Manager (CUCM)
- Cisco Prime License Manager (PLM)
- Cisco Prime Collaboration Deployment (PCD) servers
- Cisco SocialMiner
To create the PAWS API user account:
- Log in as an administrative user to the command-line interface of the Cisco VOS application that you want to monitor.
- To create the new account, run the following command:
set account name new_account_username
- The interface prompts you for the privilege level and password for the new account:
- Set the privilege level to 0.
- Type the password, then retype the password to confirm.
- Newer versions of Cisco Unified Communications products require that new accounts created with the command-line interface must change the password at the first login. This requirement blocks the account from accessing the PAWS API until you change the password. To remove the requirement for this account, run the following command:
set password change-at-login disable new_account_username
- To confirm that the user account works with the Cisco PAWS API, log in as an administrator to one of the following addresses:
-
https://ip-address-of-cisco-application:8443/platform-services/services/ProductService?wsdl
-
https://ip-address-of-cisco-application:8443/platform-services/services/ClusterNodesService?wsdl
If you receive a message that the user does not have permission to access a page, then the Cisco VOS application requires a user account like the one you just created to access the PAWS API. You might get this message if you are using Cisco Unified Communications products older than version 9, because those products do not use the PAWS API. In this situation, use the credential setup for non-PAWS API. Also, you cannot use any Dynamic Applications that use the PAWS API, but you can use the SNMP and Application APIs.
Configuring Cisco Unity Connection
You can create a user account for Cisco Unity Connection applications that gives you access to other Cisco APIs such as Administrative XML (AXL), Serviceability, and Real-Time Monitoring Service. You can configure this account using the web-based interfaces for the Cisco applications. This account does not have access to the PAWS API.
To create a PAWS API user account for Cisco Unity Connection, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
To create the user account for Cisco Unity Connection:
- In a browser window, navigate to the following address:
https://ip-address-of-cisco-application/cuadmin/home.do
- Navigate to the relevant Edit Users Basics page for your version of Cisco Unity Connection (User > Users).
- Create a new user and complete the fields as needed.
- Select the role of Technician or System Administrator.
- Save the new user account.
- To confirm that the user account works with the Cisco APIs, log into one of the following addresses:
-
https://ip-address-of-cisco-application:8443/realtimeservice/services/RisPort?wsdl
-
https://ip-address-of-cisco-application:8443/controlcenterservice/services/ControlCenterServicesPort?wsdl
- If you are not prompted for the username and password when testing the addresses, your previous administrative login might still be active. Close the browser and navigate to the addresses again.
Configuring Cisco Unified Communications Manager IM and Presence
You can use the same account for Cisco Unified Communication Manager (CUCM) IM and Presence that you already created for CUCM. If you are creating an account specifically for monitoring IM and Presence, you only need the Standard CCM Server Monitoring Group.
Because Skylar One does not access the Administrative XML API for IM and Presence, the Standard AXL API Access role is not required.
To create a user account for CUCM IM and Presence:
- In a browser window, navigate to the Cisco CUCM web interface:
https://ip-address-of-cisco-cucm/ccmadmin/showHome.do
- Navigate to the relevant User Management page for your version of Cisco CUCM (User Management > Application User).
- Click the [Add New] button and complete the required information for the new user account.
- In the Permissions Information section, select the Standard CCM Server Monitoring and the Admin-3rd Party API groups and save the user record.
To create the Level 0 PAWS API user account for CUCM, see Creating the User Account for the Platform Administrative Web Services (PAWS) API. The discovery process for IM and Presence queries the CUCM servers using this user account to determine the server role (IM and Presence or CUCM). As a result, the PAWS API user account needs to be enabled on the CUCM nodes during discovery for IM and Presence.
Configuring Cisco Prime License Manager
When Cisco Prime License Manager is co-resident with Cisco Unified Communications Manager, this release of the PowerPack cannot monitor Cisco Prime License Manager.
When Cisco Prime License Manager is installed as a standalone system, and is not co-resident with another Cisco product, you can only create administrative users for the application. You can use the existing administrator account or create a new account for monitoring.
To create a user account for Cisco Prime License Manager:
- In a browser window, navigate to the following address:
https://ip-address-of-application/elm-admin/faces/main.xhtml
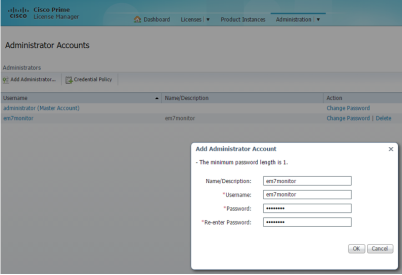
- Navigate to the Administrator Accounts page for your version of Cisco Prime License Manager (Administration > Administrator Accounts):
- Click Add Administrator and complete the required information.
- After you create the user account, you can use the following address to confirm that the new account works with the APIs:
https://ip-address-of-application/elm-admin/faces/license_usage.xhtml?
To create a PAWS API user account for Cisco Prime License Manager, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
Configuring Cisco Prime Collaboration Deployment
To create the PAWS API user account for Cisco Prime Collaboration Deployment, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
Using the PAWS API user account, use SSH to connect to the command-line interface of the application, and then run the following command to get service status:
utils service list
Configuring Cisco Collaboration Mediation Fulfillment
To create the PAWS API user account for Cisco Collaboration Mediation Fulfillment, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
After you create the account, you can use the following address to confirm that Skylar One can monitor Cisco Collaboration Mediation Fulfillment:
https://ip-address-of-application:8443/controlcenterservice/services/ControlCenterServicesPort?wsdl
Configuring Hosted Collaboration Solution Intelligent Loader
Cisco Hosted Collaboration Solution Intelligent Loader requires only a PAWS API user account. To create the PAWS API user account for Cisco Hosted Collaboration Solution Intelligent Loader, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
After you create the account, you can use the following address to confirm that Skylar One can monitor Cisco Hosted Collaboration Solution Intelligent Loader:
https://ip-address-of-application:8443/controlcenterservice/services/ControlCenterServicesPort?wsdl
Configuring Cisco Contact Center Express
Cisco Contact Center Express does not let you create additional accounts that can access the Application API. Instead of creating an Application Monitoring user account, you must use the administrative account that was assigned when the product was first installed.
To create the PAWS API user account for Cisco Contact Center Express, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
Configuring Cisco Emergency Responder
You can only use SNMP to monitor the Cisco Emergency Responder. To set up SNMP for the Cisco Emergency Responder, see Configuring SNMP for Cisco VOS applications.
Configuring Cisco SocialMiner
To set up SNMP for Cisco SocialMiner, see Configuring SNMP for Cisco VOS applications.
To create the PAWS API user account for Cisco SocialMiner, see Creating the User Account for the Platform Administrative Web Services (PAWS) API.
To use a Social Miner account, make sure that the account has Administrator credentials for API access. You can use an existing SocialMiner administrator account or create a new account for monitoring that has administrator permissions.
NOTE: Because Cisco SocialMiner is a virtual machine that does not support clusters, Skylar One creates a cluster for each SocialMiner device during the discovery process. Skylar One then uses that cluster to create a component level where it can use the relevant Cisco VOS dynamic applications. For more information, see Discovering VOS Devices.
Enabling Network Address Translation (NAT) for Cisco UC VOS Devices
If you are monitoring Cisco UC VOS devices in a Network Address Translation (NAT) environment, you should enable the "Use Server Hostname for NAT" threshold object in the "Cisco: VOS Node Classification and Cluster Creation" Dynamic Application. This will cause the VOS performance monitoring Dynamic Applications to embed the target devices' component names into associated SOAP requests, rather than the devices' IP addresses.
To enable NAT support for Cisco UC VOS devices:
- Go to the Dynamic Applications Manager page (System > Manage > Applications).
- Locate the "Cisco: VOS Node Classification and Cluster Creation" Dynamic Application and then click its wrench icon (
 ). The Dynamic Applications Properties Editor page appears.
). The Dynamic Applications Properties Editor page appears. - Click the tab. The Threshold Objects page appears.
- Click the wrench icon (
 ) for the "Use Server Hostname for NAT" Threshold Object.
) for the "Use Server Hostname for NAT" Threshold Object. - In the Threshold Value field, type "1". This signifies that NAT support is enabled.
To disable NAT support, type "0" in this field. "0" and "1" are the only two values you can type in this field for the "Use Server Hostname for NAT" Threshold Object.
This threshold is set on a per-device basis, and will affect all VOS performance Dynamic Applications aligned to a given device.
- Click .
Creating Cisco UC VOS Application Credentials
To configure Skylar One to monitor VOS applications, you must use Skylar One to create the credentials that enable Skylar One to connect with the devices in those application clusters. You can create the following credential types to monitor VOS applications:
- SNMP
- SOAP/XML (PAWS API)
- SOAP/XML (non-PAWS API)
- Basic/Snippet
Creating an SNMP Credential
Skylar One uses SNMP to collect information about the following devices that can be monitored using the Dynamic Applications in the "Cisco: UC VOS Applications" PowerPack:
- Cisco Contact Center Express (CCX)
- Cisco Unity Connection (CUC) servers
- Cisco Hosted Collaboration Mediation for Fulfillment (HCM-F)
- Cisco HCS Intelligent Loader
- Cisco IM & Presence (IM&P) servers (optional)
- Cisco Emergency Responder
- Cisco Prime Collaboration Deployment (PCD) servers (optional, but recommended)
- Cisco SocialMiner
To monitor these devices, you must first define one or more SNMP credentials that enable Skylar One to communicate with the applications.
To configure an SNMP credential:
- Go to the Credentials page (Manage > Credentials).
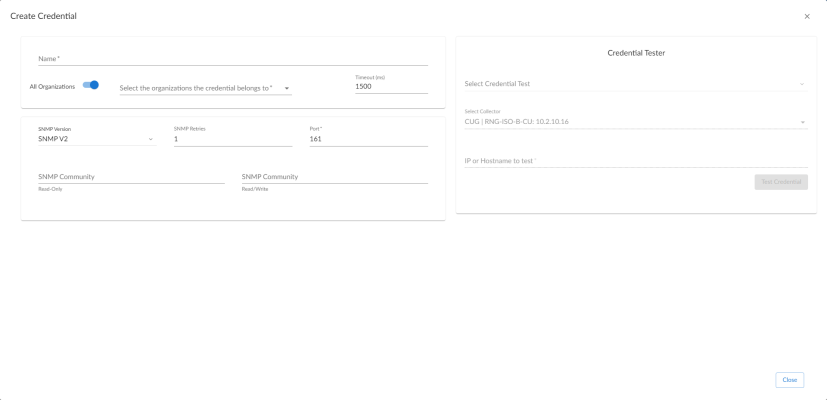
- Click the button and then select Create SNMP Credential. The Create Credential page appears:
- In the Name field, type a name for the credential.
If you are monitoring multiple VOS applications that have the same SNMP credential information, including community string, then you can create one common SNMP credential for those applications. Otherwise, each application should have its own unique SNMP credential. In that scenario, ScienceLogic recommends specifying the application type in the credential's Name (e.g., "Cisco VOS SNMP - CCX").
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- In the SNMP Version field, select SNMP V2.
- In the SNMP Community (Read-Only) field, type the community string for the VOS application you want to monitor.
- Supply values in the other fields on this page as needed. In most cases, you can accept the default values for the other fields.
- Click the button.
Creating an SNMP Credential in the Skylar One Classic User Interface
Skylar One uses SNMP to collect information about the following devices that can be monitored using the Dynamic Applications in the "Cisco: UC VOS Applications" PowerPack:
- Cisco Contact Center Express (CCX)
- Cisco Unity Connection (CUC) servers
- Cisco Hosted Collaboration Mediation for Fulfillment (HCM-F)
- Cisco HCS Intelligent Loader
- Cisco IM & Presence (IM&P) servers (optional)
- Cisco Emergency Responder
- Cisco Prime Collaboration Deployment (PCD) servers (optional, but recommended)
- Cisco SocialMiner
To monitor these devices, you must first define one or more SNMP credentials that enable Skylar One to communicate with the applications.
To configure an SNMP credential:
- Go to the Credential Management page (System > Manage > Credentials).
- Click the button.
- In the drop-down list that appears, select SNMP Credential. The Credential Editor page appears.
- In the Profile Name field, type a name for the credential.
If you are monitoring multiple VOS applications that have the same SNMP credential information, including community string, then you can create one common SNMP credential for those applications. Otherwise, each application should have its own unique SNMP credential. In that scenario, ScienceLogic recommends specifying the application type in the credential's Profile Name (e.g., "Cisco VOS SNMP - CCX").
- In the SNMP Version field, select SNMP V2.
- In the SNMP Community (Read Only) field, type the community string for the VOS application you want to monitor.
- Supply values in the other fields on this page as needed. In most cases, you can accept the default values for the other fields.
- Click the button.
Creating a SOAP/XML Credential (PAWS API)
Skylar One uses SOAP API queries, Cisco Platform Administrative Web Service (PAWS) API queries, and requests to an HTML-based user interface to monitor the following Cisco VOS applications:
- Cisco Contact Center Express (CCX) (SOAP and PAWS)
- Cisco Unity Connection (CUC) servers (SOAP and PAWS)
- Cisco Hosted Collaboration Mediation for Fulfillment (HCM-F) (PAWS only)
- Cisco HCS Intelligent Loader (PAWS only)
- Cisco IM & Presence (IM&P) servers (SOAP and PAWS)
- Cisco Prime License Manager (PLM) (PAWS and HTML)
- Cisco Prime Collaboration Deployment (PCD) servers (SOAP and PAWS)
- Cisco SocialMiner (SOAP and PAWS)
As a result, several of the Dynamic Applications (including all performance Dynamic Applications) in the "Cisco: UC VOS Applications" PowerPack must be aligned with a SOAP/XML credential that includes the SOAP API and PAWS API login information.
If you are configuring a credential for a Cisco VOS application that does not use the PAWS API, see Creating a SOAP/XML Credential (non-PAWS API).
When possible, ScienceLogic recommends using the same login information with read access for all of the APIs required to monitor a particular application. Doing so enables you to create a single SOAP/XML credential for each application with only the "Basic Settings" configured.
The PowerPack includes an example SOAP/XML credential that you can edit for your own use.
NOTE: If you are using a Skylar One system prior to version 11.1.0, the new user interface does not include the Duplicate option for sample credential(s). ScienceLogic recommends that you use the classic user interface and the Save As button to create new credentials from sample credentials. This will prevent you from overwriting the sample credential(s).
To configure a SOAP/XML credential:
- Go to the Credentials page (Manage > Credentials).
- Locate the Cisco VOS SOAP - Example credential, click its icon (
) and select Duplicate. A copy of the credential, called Cisco VOS SOAP - Example copy appears.
- Click the icon (
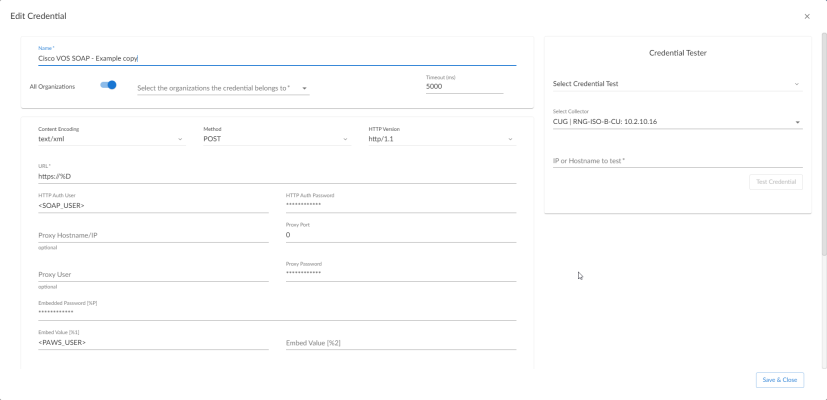
) for the Cisco VOS SOAP - Example copy credential and select Edit. The Edit Credential page appears:
- Name. Type a unique name for your VOS credential.
Each application should have its own unique SOAP/XML credential. ScienceLogic recommends specifying the application type in the credential's Name (e.g., "Cisco VOS SOAP - IM&P").
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Timeout (seconds). Type "10".
- Content Encoding. Select text/xml.
- Method. Select POST.
- HTTP Version. Select HTTP/1.1.
- URL. Type "http://%D" .
- HTTP Auth User. If the SOAP API and PAWS API login information is identical, then type the common login username. Otherwise, type the SOAP API login username.
- HTTP Auth Password. If the SOAP API and PAWS API login information is identical, then type the common login password. Otherwise, type the SOAP API login password.
- Proxy Hostname/IP. Leave this field blank.
- Proxy Port. Type "0".
- Proxy User. Leave this field blank.
- Proxy Password. Leave this field blank.
- Embedded Password [%P]. If the SOAP API and PAWS API login information differ, then type the PAWS API login password. Otherwise, leave this field blank.
- Embed Value [%1]. If the SOAP API and PAWS API login information differ, then type the PAWS API login username in this field. Otherwise, leave this field blank.
- Embed Value [%2]. Leave this field blank.
- Embed Value [%3]. Leave this field blank.
- Embed Value [%4]. Leave this field blank.
- HTTP Headers. Do not make any selections in this field.
- CURL Options. Do not make any selections in this field.
- Click the button.
Creating a SOAP/XML Credential (PAWS API) in the Skylar One Classic User Interface
Skylar One uses SOAP API queries, Cisco Platform Administrative Web Service (PAWS) API queries, and requests to an HTML-based user interface to monitor the following Cisco VOS applications:
- Cisco Contact Center Express (CCX) (SOAP and PAWS)
- Cisco Unity Connection (CUC) servers (SOAP and PAWS)
- Cisco Hosted Collaboration Mediation for Fulfillment (HCM-F) (PAWS only)
- Cisco HCS Intelligent Loader (PAWS only)
- Cisco IM & Presence (IM&P) servers (SOAP and PAWS)
- Cisco Prime License Manager (PLM) (PAWS and HTML)
- Cisco Prime Collaboration Deployment (PCD) servers (SOAP and PAWS)
- Cisco SocialMiner (SOAP and PAWS)
As a result, several of the Dynamic Applications (including all performance Dynamic Applications) in the "Cisco: UC VOS Applications" PowerPack must be aligned with a SOAP/XML credential that includes the SOAP API and PAWS API login information.
If you are configuring a credential for a Cisco VOS application that does not use the PAWS API, see Creating a SOAP/XML Credential (non-PAWS API).
When possible, ScienceLogic recommends using the same login information with read access for all of the APIs required to monitor a particular application. Doing so enables you to create a single SOAP/XML credential for each application with only the "Basic Settings" configured.
The PowerPack includes an example SOAP/XML credential that you can edit for your own use.
To configure a SOAP/XML credential:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the Cisco VOS SOAP - Example credential, and then click its wrench icon (
 ). The Edit SOAP/XML Credential page appears.
). The Edit SOAP/XML Credential page appears.
- Add values to the following fields:
Basic Settings
- Profile Name. Type a unique name for your VOS credential.
Each application should have its own unique SOAP/XML credential. ScienceLogic recommends specifying the application type in the credential's Profile Name (e.g., "Cisco VOS SOAP - IM&P").
- Content Encoding. Select text/xml.
- Method. Select POST.
- HTTP Version. Select HTTP/1.1.
- URL. Type "http://%D" .
- HTTP Auth User. If the SOAP API and PAWS API login information is identical, then type the common login username. Otherwise, type the SOAP API login username.
- HTTP Auth Password. If the SOAP API and PAWS API login information is identical, then type the common login password. Otherwise, type the SOAP API login password.
- Timeout (seconds). Type "10".
Proxy Settings
- Hostname/IP. Leave this field blank.
- Port. Type "0".
- User. Leave this field blank.
CURL Options
- CURL Options. Do not make any selections in this field.
SOAP Options
- Embedded Password [%P]. If the SOAP API and PAWS API login information differ, then type the PAWS API login password. Otherwise, leave this field blank.
- Embed Value [%1]. If the SOAP API and PAWS API login information differ, then type the PAWS API login username in this field. Otherwise, leave this field blank.
- Embed Value [%2]. Leave this field blank.
- Embed Value [%3]. Leave this field blank.
- Embed Value [%4]. Leave this field blank.
HTTP Headers
- HTTP Headers. Do not make any selections in this field.
- Click the button.
Creating a SOAP/XML Credential (non-PAWS API)
If you do not have access to the Cisco Platform Administrative Web Service (PAWS) API, configure a SOAP/XML credential using the settings in this section.
Skylar One uses SOAP API queries and requests to an HTML-based user interface to monitor the following VOS applications:
- Cisco Contact Center Express (CCX) (SOAP)
- Cisco Unity Connection (CUC) servers (SOAP)
- Cisco IM & Presence (IM&P) servers (SOAP )
- Cisco Prime License Manager (PLM) (HTML)
- Cisco Prime Collaboration Deployment (PCD) servers (SOAP)
- Cisco SocialMiner (SOAP)
As a result, several of the Dynamic Applications (including all performance Dynamic Applications) in the "Cisco: UC VOS Applications" PowerPack must be aligned with a SOAP/XML credential that includes the SOAP API login information.
When possible, ScienceLogic recommends using the same login information with read access for all of the APIs required to monitor a particular application. Doing so enables you to create a single SOAP/XML credential for each application with only the "Basic Settings" configured.
The PowerPack includes an example SOAP/XML credential that you can edit for your own use.
NOTE: If you are using a Skylar One system prior to version 11.1.0, the new user interface does not include the Duplicate option for sample credential(s). ScienceLogic recommends that you use the classic user interface and the Save As button to create new credentials from sample credentials. This will prevent you from overwriting the sample credential(s).
To configure a SOAP/XML credential:
- Go to the Credentials page (Manage > Credentials).
- Locate the Cisco VOS SOAP - Example credential, click its icon (
) and select Duplicate. A copy of the credential, called Cisco VOS SOAP - Example copy appears.
- Click the icon (
) for the Cisco VOS SOAP - Example copy credential and select Edit. The Edit Credential page appears:
- Name. Type a unique name for your VOS credential.
Each application should have its own unique SOAP/XML credential. ScienceLogic recommends specifying the application type in the credential's Profile Name (e.g., "Cisco VOS SOAP - IM&P").
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Timeout (seconds). Type "10".
- Content Encoding. Select text/xml.
- Method. Select POST.
- HTTP Version. Select HTTP/1.1.
- URL. Type "http://%D".
- HTTP Auth User. Type the SOAP API login username.
- HTTP Auth Password. Type the SOAP API login password.
- Proxy Hostname/IP. Leave this field blank.
- Proxy Port. Type "0".
- Proxy User. Leave this field blank.
- Proxy Password. Leave this field blank.
- Embedded Password [%P]. Leave this field blank.
- Embed Value [%1]. Type "SOAP" or "SNMP" as applicable. "SOAP" indicates that the PAWS service will not be queried during discovery, but SOAP will still be used for monitoring. "SNMP" indicates that neither the PAWS service nor the SOAP service will be queried during discovery. Otherwise, leave this field blank.
- Embed Value [%2]. If you typed "SOAP" or "SNMP" in Embed Value [%1], then type the IP address or hostname list for the cluster nodes, with each address in the list separated by a comma. (The first address or hostname in the list is assumed to be primary.) Otherwise, leave this field blank.
If you enter hostnames in this field, you must first enable Network Address Translation (NAT) support for Cisco UC VOS devices.
If you enter hostnames in this field that cannot be resolved to IP addresses, then you must create a Host File entry for each hostname included in the list. In a NAT environment, the Host File entry should contain an entry for the external IP addresses. For more information about Host Files, see
- Embed Value [%3].If you typed "SOAP" or "SNMP" in Embed Value [%1], then type the appropriate VOS application cluster type abbreviation as follows:
- CUC
- IM&P
- CCX
- PLM
- HCS Intelligent Loader
- HCM-F
- PCD
- SocialMiner
- Embed Value [%4]. Leave this field blank.
- HTTP Headers. Do not make any selections in this field.
- CURL Options. Do not make any selections in this field.
- Click the button.
Creating a SOAP/XML Credential (non-PAWS API) in the Skylar One Classic User Interface
If you do not have access to the Cisco Platform Administrative Web Service (PAWS) API, configure a SOAP/XML credential using the settings in this section.
Skylar One uses SOAP API queries and requests to an HTML-based user interface to monitor the following VOS applications:
- Cisco Contact Center Express (CCX) (SOAP)
- Cisco Unity Connection (CUC) servers (SOAP)
- Cisco IM & Presence (IM&P) servers (SOAP )
- Cisco Prime License Manager (PLM) (HTML)
- Cisco Prime Collaboration Deployment (PCD) servers (SOAP)
- Cisco SocialMiner (SOAP)
As a result, several of the Dynamic Applications (including all performance Dynamic Applications) in the "Cisco: UC VOS Applications" PowerPack must be aligned with a SOAP/XML credential that includes the SOAP API login information.
When possible, ScienceLogic recommends using the same login information with read access for all of the APIs required to monitor a particular application. Doing so enables you to create a single SOAP/XML credential for each application with only the "Basic Settings" configured.
The PowerPack includes an example SOAP/XML credential that you can edit for your own use.
To configure a SOAP/XML credential for non-PAWS APIs:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the Cisco VOS SOAP - Example credential, and then click its wrench icon (
 ). The Edit SOAP/XML Credential page appears.
). The Edit SOAP/XML Credential page appears.
- Add values to the following fields:
Basic Settings
- Profile Name. Type a unique name for your VOS credential.
Each application should have its own unique SOAP/XML credential. ScienceLogic recommends specifying the application type in the credential's Profile Name (e.g., "Cisco VOS SOAP - IM&P").
- Content Encoding. Select text/xml.
- Method. Select POST.
- HTTP Version. Select HTTP/1.1.
- URL. Type "http://%D".
- HTTP Auth User. Type the SOAP API login username.
- HTTP Auth Password. Type the SOAP API login password.
- Timeout (seconds). Type "10".
Proxy Settings
- Hostname/IP. Leave this field blank.
- Port. Type "0".
- User. Leave this field blank.
CURL Options
- CURL Options. Do not make any selections in this field.
SOAP Options
- Embedded Password [%P]. Leave this field blank.
- Embed Value [%1]. Type "SOAP" or "SNMP" as applicable. "SOAP" indicates that the PAWS service will not be queried during discovery, but SOAP will still be used for monitoring. "SNMP" indicates that neither the PAWS service nor the SOAP service will be queried during discovery. Otherwise, leave this field blank.
- Embed Value [%2]. If you typed "SOAP" or "SNMP" in Embed Value [%1], then type the IP address or hostname list for the cluster nodes, with each address in the list separated by a comma. (The first address or hostname in the list is assumed to be primary.) Otherwise, leave this field blank.
If you enter hostnames in this field, you must first enable Network Address Translation (NAT) support for Cisco UC VOS devices.
If you enter hostnames in this field that cannot be resolved to IP addresses, then you must create a Host File entry for each hostname included in the list. In a NAT environment, the Host File entry should contain an entry for the external IP addresses. For more information about Host Files, see
- Embed Value [%3].If you typed "SOAP" or "SNMP" in Embed Value [%1], then type the appropriate VOS application cluster type abbreviation as follows:
- CUC
- IM&P
- CCX
- PLM
- HCS Intelligent Loader
- HCM-F
- PCD
- SocialMiner
Otherwise, leave this field blank.
- Embed Value [%4]. Leave this field blank.
HTTP Headers
- HTTP Headers. Do not make any selections in this field.
- Click the button.
Creating a Basic/Snippet Credential
Skylar One uses REST API queries to monitor the following VOS applications:
- Cisco Unity Connection (CUC) servers
- Cisco IM & Presence (IM&P) servers
To monitor these devices, you must create one or more Basic/Snippet credentials that enable Skylar One to log in to the REST API that reports the status of each VOS application's cluster. The "Cisco: UC VOS Applications" PowerPack includes two example Basic/Snippet credentials that you can edit for your own use.
The steps below describe how to edit both example credentials, which you should do if the REST API login information is different for CUC and IM&P. However, if the REST API login information is the same for both applications, then a second Basic/Snippet credential is unnecessary.
NOTE: If you are using a Skylar One system prior to version 11.1.0, the new user interface does not include the Duplicate option for sample credential(s). ScienceLogic recommends that you use the classic user interface and the Save As button to create new credentials from sample credentials. This will prevent you from overwriting the sample credential(s).
To edit the example Basic/Snippet credentials:
- Go to the Credentials page (Manage > Credentials).
- Locate the Cisco VOS CUC Cluster Status example credential, click its icon (
) and select Duplicate. A copy of the credential, called Cisco VOS CUC Cluster Status copy appears.
- Click the icon (
) for the Cisco VOS CUC Cluster Status copy credential and select Edit. The Edit Credential page appears. Update the following fields:
- Name. Type a new name for the CUC cluster status credential.
If you are monitoring multiple VOS applications that have the same REST API login information, then you can create one common Basic/Snippet credential for those applications. Otherwise, each VOS application should have its own unique Basic/Snippet credential. In that scenario, ScienceLogic recommends specifying the application type in the credential's Profile Name (e.g., "Cisco VOS Basic/Snippet - CUC").
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the What organization manages this service? drop-down field to align the credential with those specific organizations.
- Timeout. Type "10000".
- Hostname/IP. Type "%D".
- Port. Type "443".
- Username. Type the login username for the CUC cluster status REST API.
- Password. Type the password for the CUC cluster status REST API.
- Click the button.
- To create a Basic/Snippet credential to monitor VOS IM&P, repeat steps 1-4 to edit the Cisco VOS IM&P Cluster Status example credential.
Creating a Basic/Snippet Credential in the Skylar One Classic User Interface
Skylar One uses REST API queries to monitor the following VOS applications:
- Cisco Unity Connection (CUC) servers
- Cisco IM & Presence (IM&P) servers
To monitor these devices, you must create one or more Basic/Snippet credentials that enable Skylar One to log in to the REST API that reports the status of each VOS application's cluster. The "Cisco: UC VOS Applications" PowerPack includes two example Basic/Snippet credentials that you can edit for your own use.
The steps below describe how to edit both example credentials, which you should do if the REST API login information is different for CUC and IM&P. However, if the REST API login information is the same for both applications, then a second Basic/Snippet credential is unnecessary.
To edit the example Basic/Snippet credentials:
- Go to the Credential Management page (System > Manage > Credentials).
- Locate the Cisco VOS CUC Cluster Status example credential, then click its wrench icon (
 ). The Edit Basic/Snippet Credential page appears.
). The Edit Basic/Snippet Credential page appears.
- Update the following fields:
- Credential Name. Type a new name for the CUC cluster status credential.
If you are monitoring multiple VOS applications that have the same REST API login information, then you can create one common Basic/Snippet credential for those applications. Otherwise, each VOS application should have its own unique Basic/Snippet credential. In that scenario, ScienceLogic recommends specifying the application type in the credential's Profile Name (e.g., "Cisco VOS Basic/Snippet - CUC").
- Hostname/IP. Type "%D".
- Port. Type "443".
- Timeout. Type "10000".
- Username. Type the login username for the CUC cluster status REST API.
- Password. Type the password for the CUC cluster status REST API.
- Click the button.
- When the confirmation message appears, click .
- To create a Basic/Snippet credential to monitor VOS IM&P, repeat steps 1-5 to edit the Cisco VOS IM&P Cluster Status example credential.
Testing the Cisco UC VOS Credential
Skylar One includes a Credential Test for Cisco UC VOS. Credential Tests define a series of steps that Skylar One can execute on demand to validate whether a credential works as expected.
The Cisco UC VOS Credential Test can be used to test a SOAP/XML credential for monitoring Cisco UC VOS using the Dynamic Applications in the "Cisco: UC VOS Applications" PowerPack. The Cisco UC VOS Credential Test performs the following steps:
- Test Reachability. Performs an ICMP ping request to see if the device is reachable.
- Test Name Resolution. Checks to see if nslookup can resolve the IP address or hostname.
- Test Port Availability. Performs an NMAP request to see if the appropriate port is open.
- Test Credential Validity. Checks to see if the Cisco VOS credential is configured properly.
- Test PAWS and non-PAWS Monitoring Credential. Checks to see if a SOAP/XML credential can request a monitored resource.
To test the Cisco UC VOS credential:
- Go to the Credentials page (Manage > Credentials).
- Locate the Cisco UC VOS SOAP/XML credential you wish to test, select the Actions button (
) next to it and click Edit/Test. The Edit Credential modal page appears:
- In the Credential Tester pane, supply values in the following fields:
- Select Credential Test. Select "Cisco UC VOS Credential Test".
- Select Collector. Select the All-In-One Appliance or Data Collector that will run the test.
- Hostname/IP. Enter the IP address or hostname for the device.
NOTE: The credential being tested cannot include more than 32 characters in the Hostname/IP field.
- Click the button to run the credential test. The Test Credential window appears.
The Test Credential window displays a log entry for each step in the credential test. The steps performed are different for each credential test. The log entry for each step includes the following information:
- Step. The name of the step.
- Description. A description of the action performed during the step.
- Log Message. The result of the step for this credential test.
- Status. Whether the result of this step indicates the credential or the network environment is configured correctly (Passed) or incorrectly (Failed).
- Step Tip. Mouse over the question mark icon (
 ) to display the tip text. The tip text recommends what to do to change the credential or the network environment if the step has a status of "Failed".
) to display the tip text. The tip text recommends what to do to change the credential or the network environment if the step has a status of "Failed".
Testing the Cisco UC VOS Credential in the Skylar One Classic User Interface
Skylar One includes a Credential Test for Cisco UC VOS. Credential Tests define a series of steps that Skylar One can execute on demand to validate whether a credential works as expected.
The Cisco UC VOS Credential Test can be used to test a SOAP/XML credential for monitoring Cisco UC VOS using the Dynamic Applications in the "Cisco: UC VOS Applications" PowerPack. The Cisco UC VOS Credential Test performs the following steps:
- Test Reachability. Performs an ICMP ping request to see if the device is reachable.
- Test Name Resolution. Checks to see if nslookup can resolve the IP address or hostname.
- Test Port Availability. Performs an NMAP request to see if the appropriate port is open.
- Test Credential Validity. Checks to see if the Cisco VOS credential is configured properly.
- Test PAWS and non-PAWS Monitoring Credential. Checks to see if a SOAP/XML credential can request a monitored resource.
To test the Cisco UC VOS credential:
- Go to the Credential Test Management page (System > Customize > Credential Tests).
- Locate the Cisco UC VOS Credential Test and click its lightning bolt icon (
 ). The Credential Tester modal page appears.
). The Credential Tester modal page appears.
- Supply values in the following fields:
- Test Type. This field is pre-populated with the credential test you selected.
- Credential. Select the credential to test. This drop-down list includes only credentials that you have access to that can be tested using the selected credential test.
- Hostname/IP. Enter the IP address or hostname for the device.
NOTE: The credential being tested cannot include more than 32 characters in the Hostname/IP field.
- Collector. Select the All-In-One Appliance or Data Collector that will run the test.
- Click the button to run the credential test. The Test Credential window appears.
The Test Credential window displays a log entry for each step in the credential test. The steps performed are different for each credential test. The log entry for each step includes the following information:
- Step. The name of the step.
- Description. A description of the action performed during the step.
- Log Message. The result of the step for this credential test.
- Status. Whether the result of this step indicates the credential or the network environment is configured correctly (Passed) or incorrectly (Failed).
- Step Tip. Mouse over the question mark icon (
 ) to display the tip text. The tip text recommends what to do to change the credential or the network environment if the step has a status of "Failed".
) to display the tip text. The tip text recommends what to do to change the credential or the network environment if the step has a status of "Failed".