The following sections describe how to install Net-SNMP on a Linux device and how to configure Net-SNMP:
Use the following menu options to navigate the SL1 user interface:
- To view a pop-out list of menu options, click the menu icon (
 ).
). - To view a page containing all of the menu options, click the Advanced menu icon (
 ).
).
For detailed descriptions of Net-SNMP for each supported operating system, see http://www.net-snmp.org.
Installing Net-SNMP on Linux Devices
For each Linux device that you want to monitor with Net-SNMP, you must install and configure Net-SNMP. If you want to monitor multiple devices with Net-SNMP, you must install Net-SNMP and create the snmpd.conf file on each device to be monitored.
NOTE: Most Linux distributions will require the same installation and configuration as described in this
If Net-SNMP is correctly installed and configured on a Linux device, SL1 can automatically query the device and collect data. SL1 includes multiple default Dynamic Applications for the Net-SNMP agent. These Dynamic Applications allow SL1 to collect selected data-points from Net-SNMP devices. The data is then used to create reports and graphs, accessible via the graphical user-interface.
By querying Net-SNMP data-points, SL1 can collect and present at least the following about a device:
- System name, operating system, operating system version, and uptime
- File-system configuration and usage
- Memory size and usage
- CPU usage
- Installed software
- Running processes
- Network interface details, including name, speed, and MAC address
- Bandwidth usage
Installing and Configuring Net-SNMP on a Linux computer includes the following steps:
- Verifying and Installing Net-SNMP using free RPM Packages.
- Stopping snmpd.
- Creating the snmpd.conf file. This file defines how the Net-SNMP agent will behave and includes information on the physical location and the contact information for the server, access control for the Net-SNMP agent, and trap destinations for the agent.
- Starting snmpd and testing connectivity to Net-SNMP.
Step 1: Verifying and Installing Net-SNMP with RPM Packages
The operating system for SL1 ships with the following RPM packages for Net-SNMP:
- net-snmp-5.7.2-24.silo.el7.x86_64
- net-snmp-libs-5.7.2-24.silo.el7.x86_64
- net-snmp-utils--5.7.2-24.silo.el7.x86_64
To continue with the steps in this
- Open a shell session
- Enter one of the following at the prompt:
rpm -qa | grep net-snmp
or
yum list net-snmp
- Ensure that the output of this command includes each RPM listed above.
- If one or more of these packages are missing you can run the appropriate command from the following commands:
yum install net-snmp
yum install net-snmp-libs
yum install net-snmp-utils
- After you have verified and installed all the packages, you can create the net-snmp configuration file and start the snmp service (agent).
Step 2: Stopping snmpd
The Linux RPM for net-snmp includes the snmpd (Net-SNMP agent) binary as follows:
- The snmpd binary is installed in the directory /usr/sbin/snmpd.
- The configuration file for the snmpd agent is installed in /etc/snmp/snmpd.conf
NOTE: You should configure the snmpd.conf file before you start the snmpd daemon.
You must check if the snmpd agent is running. If it is, you must stop the snmpd agent so you can create the configuration file.
To check the snmpd agent and stop it (if necessary):
- Open a shell session.
- To see if the snmpd agent is running, enter the following at the prompt:
/etc/init.d/snmpd status
- If snmpd is running, you will see a message like "snmpd is running".
- If the snmpd agent is running, enter the following command to stop the agent:
/etc/init.d/snmpd stop
Step 3: Creating the snmpd.conf file
The snmpd.conf. file defines how the Net-SNMP daemon will behave and includes information about the physical location and contact information for the server, access control for the Net-SNMP agent, and trap destinations for the Net-SNMP agent.
In most cases, your computer(s) will already have an existing /etc/snmp/snmpd.conf file that includes the default settings. Because we want to create a new, clean snmpd.conf file, you must replace the existing file. You must move, not copy, the file, to ensure that you are creating a new file and not simply append new settings to the default settings in the snmpd.conf file. After stopping the snmpd agent, you must move the existing config file.
To move the existing configuration file, open a shell session and enter the following at the command line:
mv /etc/snmp/snmpd.conf /etc/snmp/snmpd.conf.orig
To create the/etc/snmp/snmpd.conf file:
- You can replace your snmpd.conf file with one of the examples in the following sections. There is an example configuration file for Net-SNMP for SNMPv2 and another for SNMPv3 on Linux.
- The example configuration files contain the basic settings that SL1 will need to communicate successfully with the Net-SNMP agent on the Linux server.
- For basic compatibility, you should edit your file to include only the entries from the selected example.
NOTE: Net-SNMP is highly customizable, and SL1 can fully take advantage of these customizations. If you are interested in extending your Net-SNMP agent, please contact ScienceLogic Professional Services.
Example snmpd.conf file for SNMPv2:
The following is a working example of a snmpd.conf file for SNMPv2. You should edit your snmpd.conf file to include only the entries from this example file.
NOTE: This snmpd.conf file does not include encrypting SNMP access to the Linux client.
The file should be located in /etc/snmp/snmpd.conf:
# snmpd.conf
#
# - created by the snmpconf configuration program
#
##############################################################
# SECTION: System Information Setup
#
# This section defines some of the information reported in
# the "system" mib group in the mibII tree.
# syslocation: The [typically physical] location of the system.
# Note that setting this value here means that when trying to
# perform an snmp SET operation to the sysLocation.0 variable will make
# the agent return the "notWritable" error code. IE, including
# this token in the snmpd.conf file will disable write access to
# the variable.
# arguments: location_string
syslocation "Reston, Virginia"
# syscontact: The contact information for the administrator
# Note that setting this value here means that when trying to
# perform an snmp SET operation to the sysContact.0 variable will make
# the agent return the "notWritable" error code. IE, including
# this token in the snmpd.conf file will disable write access to
# the variable.
# arguments: contact_string
syscontact "ScienceLogic Support 1-703-354-1010”
##############################################################
# SECTION: Access Control Setup
#
# This section defines who is allowed to talk to your running
# snmp agent
# rocommunity: a SNMPv1/SNMPv2c read-only access community name
# arguments: community [default|hostname|network/bits] [oid]
rocommunity public
# rwcommunity: a SNMPv1/SNMPv2c read-write access community name
# arguments: community [default|hostname|network/bits] [oid]
# rwcommunity private
##############################################################
# SECTION: Trap Destinations
#
# Here we define who the agent will send traps to.
# trap2sink: A SNMPv2c trap receiver
# arguments: host [community] [portnum]
#
trap2sink 192.168.10.71 public
# End of File
NOTE: The example snmpd.conf file for SNMPv2 uses the default community string ("public") and ScienceLogic-specific examples of Contact and Location information and Trap Destinations. You will need to change these settings to match your local environment.
Adding Read/Write Access to the snmpd.conf File for SNMPv2
The example snmpd.conf file provides only Read Only access to your Linux system from SL1 (using the default "SNMP public" credential that is included in SL1). If you require SL1 to have Read/Write access to your Linux system, you will need to perform the following steps.
- In the snmpd.conf file, uncomment the line for rwcommunity. To do this:
Change this line:
# rwcommunity private
To:
rwcommunity private
- Save your changes and exit the file.
Example snmpd.conf file for SNMPv3:
The following is a working example of a snmpd.conf file for SNMPv3. For operation with SL1, you should edit your snmpd.conf file to include only entries from this example file.
This example snmpd.conf file includes read and write community strings and encrypts all Net-SNMP access to your Linux system from SL1.
The file should reside in /etc/snmp/snmpd.conf:
# snmpd.conf
#
# - created by the snmpconf configuration program
#################################################################
# SECTION: System Information Setup
#
# This section defines some of the information reported in
# the "system" mib group in the mibII tree.
# syslocation: The [typically physical] location of the system.
# Note that setting this value here means that when trying to
# perform an snmp SET operation to the sysLocation.0 variable will make
# the agent return the "notWritable" error code. IE, including
# this token in the snmpd.conf file will disable write access to
# the variable.
# arguments: location_string
syslocation "Reston, Virginia”
# syscontact: The contact information for the administrator
# Note that setting this value here means that when trying to
# perform an snmp SET operation to the sysContact.0 variable will make
# the agent return the "notWritable" error code. IE, including
# this token in the snmpd.conf file will disable write access to
# the variable.
# arguments: contact_string
syscontact "ScienceLogic Support: 1-703-354-1010"
#################################################################
# SECTION: Access Control Setup
#
# This section defines who is allowed to talk to your running
# snmp agent.
# rwuser: a SNMPv3 read-write user
# arguments: user [noauth|auth|priv] [restriction_oid]
rouser linuser priv
createUser linuser SHA linuserpass DES linprivpass
rwuser linadmin priv
createUser linadmin SHA linauthpass DES linprivpass
#################################################################
# SECTION: Trap Destinations
#
# Here we define who the agent will send traps to.
# trap2sink: A SNMPv2c trap receiver
# arguments: host [community] [portnum]
#
trap2sink 192.168.10.71 public
# End of File
NOTE: The example snmpd.conf file for SNMPv3 uses ScienceLogic-specific examples of Contact and Location information and Trap Destinations. You will need to change these settings to match your local environment. In SL1, you must create a Read-Only credential for SNMPv3 and a Read/Write credential for SNMPv3 that match the credentials specified in the snmpd.conf file.
Step 4: Starting snmpd and Testing connectivity to Net-SNMP
These sections describe how to start the snmpd agent and how to test connectivity to Net-SNMP.
- If you use SNMPv2 and used the example snmpd.conf file for SNMPv2, follow the steps in the section on SNMPv2.
- If you use SNMPv3 and used the example snmpd.conf file for SNMPv3, follow the steps in the section on SNMPv3.
Testing the Example snmpd.conf file for SNMPv2
Now that you have created the new snmpd.conf file for SNMPv2 on your Linux system, you can start the snmpd service (agent) and test that the new file is working. To do this:
- You must first restart the snmpd agent. To do this, open a shell session and enter the following at the command prompt:
/etc/init.d/snmpd start
- The snmpd agent should now start running.
- To test the snmpd agent and the new configuration file, enter the following at the command prompt:
snmpwalk –v 2c –c public localhost system
- You should see output similar to:
SNMPv2-MIB::sysDescr.0 = STRING: Linux ps-centos-lnx 2.6.18-92.el5 #1 SMP Tue Jun 10 18:49:47 EDT 2008 i686
SNMPv2-MIB::sysObjectID.0 = OID: NET-SNMP-MIB::netSnmpAgentOIDs.10
DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (437) 0:00:04.37
SNMPv2-MIB::sysContact.0 = STRING: "ScienceLogic Support 1-703-354-1010"
SNMPv2-MIB::sysName.0 = STRING: ps.centos-lnx
SNMPv2-MIB::sysLocation.0 = STRING: "Reston, Virginia"
SNMPv2-MIB::sysORLastChange.0 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORID.1 = OID: SNMPv2-MIB::snmpMIB
SNMPv2-MIB::sysORID.2 = OID: TCP-MIB::tcpMIB
SNMPv2-MIB::sysORID.3 = OID: IP-MIB::ip
SNMPv2-MIB::sysORID.4 = OID: UDP-MIB::udpMIB
SNMPv2-MIB::sysORID.5 = OID: SNMP-VIEW-BASED-ACM-MIB::vacmBasicGroup
SNMPv2-MIB::sysORID.6 = OID: SNMP-FRAMEWORK-MIB::snmpFrameworkMIBCompliance
SNMPv2-MIB::sysORID.7 = OID: SNMP-MPD-MIB::snmpMPDCompliance
SNMPv2-MIB::sysORID.8 = OID: SNMP-USER-BASED-SM-MIB::usmMIBCompliance
SNMPv2-MIB::sysORDescr.1 = STRING: The MIB module for SNMPv2 entities
SNMPv2-MIB::sysORDescr.2 = STRING: The MIB module for managing TCP implementations
SNMPv2-MIB::sysORDescr.3 = STRING: The MIB module for managing IP and ICMP implementations
SNMPv2-MIB::sysORDescr.4 = STRING: The MIB module for managing UDP implementations
SNMPv2-MIB::sysORDescr.5 = STRING: View-based Access Control Model for SNMP.
SNMPv2-MIB::sysORDescr.6 = STRING: The SNMP Management Architecture MIB.
SNMPv2-MIB::sysORDescr.7 = STRING: The MIB for Message Processing and Dispatching.
SNMPv2-MIB::sysORDescr.8 = STRING: The management information definitions for the SNMP User-based Security Model.
SNMPv2-MIB::sysORUpTime.1 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.2 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.3 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.4 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.5 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.6 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.7 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.8 = Timeticks: (0) 0:00:00.00
Testing the Example snmpd.conf file for SNMPv3
Now that you have created the new snmpd.conf file for SNMPv3 on your Linux system, you can start the snmpd service (agent) and test that the new file is working. To do this:
- You must first restart the snmpd agent. To do this, open a shell session and enter the following at the command prompt:
/etc/init.d/snmpd start
- The snmpd agent should now start running.
- To test the snmpd agent and the new configuration file, enter the following at the command prompt. We are using the credentials from the example snmpd.conf file for SNMPv3 (linuser, linuserpass, and linprivpass); if you used different credentials, please substitute them in the command:
snmpwalk -v 3 -u linuser -l authPriv -a SHA -A linuserpass -x DES -X linprivpass localhost system
- You should see output similar to:
SNMPv2-MIB::sysDescr.0 = STRING: Linux ps-centos-lnx 2.6.18-92.el5 #1 SMP Tue Jun 10 18:49:47 EDT 2008 i686
SNMPv2-MIB::sysObjectID.0 = OID: NET-SNMP-MIB::netSnmpAgentOIDs.10
DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (327207) 0:54:32.07
SNMPv2-MIB::sysContact.0 = STRING: "ScienceLogic Support 1-703-354-1010"
SNMPv2-MIB::sysName.0 = STRING: ps-centos-lnx
SNMPv2-MIB::sysLocation.0 = STRING: "Reston, Virginia"
SNMPv2-MIB::sysORLastChange.0 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORID.1 = OID: SNMPv2-MIB::snmpMIB
SNMPv2-MIB::sysORID.2 = OID: TCP-MIB::tcpMIB
SNMPv2-MIB::sysORID.3 = OID: IP-MIB::ip
SNMPv2-MIB::sysORID.4 = OID: UDP-MIB::udpMIB
SNMPv2-MIB::sysORID.5 = OID: SNMP-VIEW-BASED-ACM-MIB::vacmBasicGroup
SNMPv2-MIB::sysORID.6 = OID: SNMP-FRAMEWORK-MIB::snmpFrameworkMIBCompliance
SNMPv2-MIB::sysORID.7 = OID: SNMP-MPD-MIB::snmpMPDCompliance
SNMPv2-MIB::sysORID.8 = OID: SNMP-USER-BASED-SM-MIB::usmMIBCompliance
SNMPv2-MIB::sysORDescr.1 = STRING: The MIB module for SNMPv2 entities
SNMPv2-MIB::sysORDescr.2 = STRING: The MIB module for managing TCP implementations
SNMPv2-MIB::sysORDescr.3 = STRING: The MIB module for managing IP and ICMP implementations
SNMPv2-MIB::sysORDescr.4 = STRING: The MIB module for managing UDP implementations
SNMPv2-MIB::sysORDescr.5 = STRING: View-based Access Control Model for SNMP.
SNMPv2-MIB::sysORDescr.6 = STRING: The SNMP Management Architecture MIB.
SNMPv2-MIB::sysORDescr.7 = STRING: The MIB for Message Processing and Dispatching.
SNMPv2-MIB::sysORDescr.8 = STRING: The management information definitions for the SNMP User-based Security Model.
SNMPv2-MIB::sysORUpTime.1 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.2 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.3 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.4 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.5 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.6 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.7 = Timeticks: (0) 0:00:00.00
SNMPv2-MIB::sysORUpTime.8 = Timeticks: (0) 0:00:00.00
Creating SNMP Credentials for Linux
The following sections describe how to create SNMP credentials in SL1 to monitor Linux devices.
- If you use SNMPv2 and used the example snmpd.conf file for SNMPv2, follow the steps in the section on SNMPv2.
- If you use SNMPv3 and used the example snmpd.conf file for SNMPv3, follow the steps in the section on SNMPv3.
Creating SNMPv2 Credentials
SNMP Credentials (called "community strings" in earlier versions of SNMP) allow SL1 to access SNMP data on a managed device. SL1 uses SNMP credentials to perform discovery, run auto-discovery, and gather information from SNMP Dynamic Applications.
To create an SNMPv2 credential:
- Go to the Credential Management page (System > Manage > Credentials).
- In the Credential Management page, click the menu. Select Create SNMP Credential.
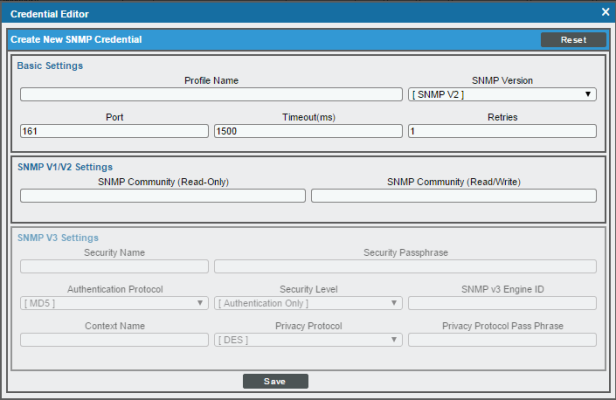
- The Credential Editor modal page appears. In this page, you can define the new SNMP credential. To define the new credential, supply values in the following fields:
- Profile Name. Name of the credential. Can be any combination of alphanumeric characters. This field is required.
- SNMP Version. SNMP version. Select SNMP V2. This field is required.
- Port. The port SL1 will use to communicate with the external device or application. The default value is 161. This field is required.
- Timeout (ms). Time, in milliseconds, after which SL1 will stop trying to communicate with the SNMP device. The default value is 1500. This field is required.
- Retries. Number of times SL1 will try to authenticate and communicate with the external device. The default value is 1. This field is required.
SNMP V1/V2 Settings
These fields appear if you selected SNMP V1 or SNMP V2 in the SNMP Version field. Otherwise, these fields are grayed out.
- SNMP Community (Read Only). The SNMP community string (password) required for read-only access of SNMP data on the remote device or application. For read-only SNMP V2 credentials, this field is required and you should leave the SNMP Community (Read/Write) field blank. Enter the same value as you entered for rocommunity in the snmpd.conf file.
- SNMP Community (Read/Write). The SNMP community string (password) required for read and write access of SNMP data on the remote device or application. For read/write SNMP V2 credentials, this field is required and you should leave the SNMP Community (Read Only) field blank. Enter the same value as you entered for rwcommunity in the snmpd.conf file.
- Click the button to save the new SNMP credential.
NOTE: When you define an SNMP Credential, the credential will automatically be aligned with the organization(s) you are a member of.
Creating SNMPv3 Credentials
The example snmpd.conf file for SNMPv3 provides both Read Only and Read/Write access to your Linux system from SL1. You must therefore define two new SNMPv3 credentials (one for read-only access and one for read/write access) in SL1, so SL1 can successfully communicate with your Linux system. To do this:
- Go to the Credential Management page (System > Manage > Credentials).
- In the Credential Management page, click the menu. Select Create SNMP Credential.
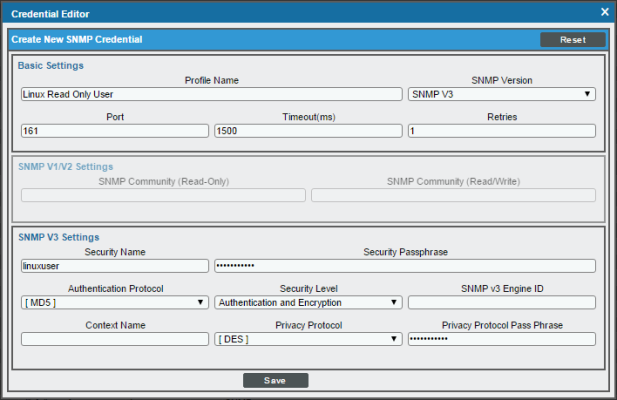
- The Credential Editor modal page appears. In this page, you can define the new SNMP credential. To define the new read-only credential, supply values in the following fields:
- Profile Name. Name of the read-only credential. Can be any combination of alphanumeric characters. This field is required.
- SNMP Version. SNMP version. Select SNMP V3. This field is required.
- Port. The port SL1 will use to communicate with the external device or application. The default value is 161. This field is required.
- Timeout (ms). Time, in milliseconds, after which SL1 will stop trying to communicate with the SNMP device. The default value is 1500. This field is required.
- Retries. Number of times SL1 will try to authenticate and communicate with the external device. The default value is 1. This field is required.
SNMP V3 Settings
These fields appear if you selected SNMP V3 in the SNMP Version field. Otherwise, these fields are grayed out.
- Security Name. Name used for read-only SNMP authentication. This field is required. Enter the same value as you entered for rouser in the snmpd.conf file.
- Security Passphrase. Password used to authenticate the credential. This value must contain at least 8 characters. This value is required if you want to use a Security Level that includes authentication. Enter the same value as you entered in the createuser line in the snmpd.conf file.
- Authentication Protocol. Select an authentication algorithm for the credential. Choices are MD5 or SHA. This field is required. Select SHA.
NOTE: If your SL1 system is FIPS-compliant, MD5 authentication for SNMP will fail.FIPS-compliant SL1 systems require SHA authentication for SNMP.
- Security Level. Specifies the combination of security features for the credentials. This field is required. Choices are:
- No Authentication / No Encryption.
- Authentication Only. This is the default value.
- Authentication and Encryption. This is the option specified in the example snmpd.conf file.
- SNMP v3 Engine ID. The unique engine ID for the SNMP agent you want to communicate with. (SNMPv3 authentication and encryption keys are generated based on the associated passwords and the engine ID.) This field is optional.
- Context Name. A context is a mechanism within SNMPv3 (and AgentX) that allows you to use parallel versions of the same MIB objects. For example, one version of a MIB might be associated with SNMP Version 2 and another version of the same MIB might be associated with SNMP Version 3. For SNMP Version 3, specify the context name in this field. This field is optional.
- Privacy Protocol. The privacy service encryption and decryption algorithm. Choices are DES or AES. The default value is DES. This field is required. The example snmpd.conf file specifies DES.
- Privacy Protocol Passphrase. Privacy password for the credential. This field is optional.
- Click the button to save the new read-only SNMPv3 credential.
- Repeat steps 1-4 to also create the new read/write SNMPv3 credential, updating the field values as needed.
NOTE: When you define an SNMP Credential, the credential will automatically be aligned with the organization(s) you are a member of.