The following sections provide an overview of SNMP, Net-SNMP, Secure Shell (SSH), and the Linux Base Pack PowerPack:
Use the following menu options to navigate the SL1 user interface:
- To view a pop-out list of menu options, click the menu icon (
 ).
). - To view a page containing all of the menu options, click the Advanced menu icon (
 ).
).
What is SNMP?
Simple Network Management Protocol (SNMP) is a set of standard protocols for managing diverse computer hardware and software within a TCP/IP network. SNMP is the most common protocol used by network monitoring and management applications to exchange information between devices. SL1 uses this protocol and other protocols to collect availability, performance, and configuration information.
SNMP uses a server-client structure.
- Clients are called agents. Devices and software that run SNMP are agents. For the purposes of this document, Net-SNMP is the agent.
- The server is called the management system. SL1 is the management system.
Typically, agents:
- Implement the SNMP protocol on the device.
- Store data points as defined by the Management Information Base (MIB) file.
- Can asynchronously signal an event to the manager.
Typically, a management system:
- Uses the SNMP Protocol.
- Queries agents.
- Receives responses (data points) from agents.
- Acknowledges asynchronous events from agents.
Most enterprise-level network hardware is configured for SNMP and can be SNMP-enabled. Many enterprise software applications are also SNMP-compliant. When SNMP is running on a device, it uses a standard format to collect and store data about the device and/or software. For example, SNMP might collect information on each network interface and the traffic on each interface. SL1 can then query the device to retrieve the stored data.
What is Net-SNMP?
Net-SNMP is a suite of applications used to implement SNMP. Net-SNMP is an agent. Standard Net-SNMP includes the SNMP daemon and a suite of client utilities. Net-SNMP can be run on any supported operating system, and SL1 will then be able communicate with and collect data from the device.
Why Should I Use Net-SNMP?
- Net-SNMP is an open-source application. It is free to use and distribute.
- Because Net-SNMP is widely used, there are many user groups and support forums for the product.
NOTE: Although ScienceLogic does not directly support the Net-SNMP agent, this document will get you started on the installation and configuration tasks for Net-SNMP. For detailed documentation on Net-SNMP, see the Net-SNMP website.
- Net-SNMP includes source and pre-compiled objects for all major flavors or UNIX and Linux as well as a number of other operating systems.
- Net-SNMP is an extensible agent. Generally, SNMP agents can retrieve only data that has been defined in a MIB file. In most cases, a hardware or software manufacturer creates the MIB file and then ships the MIB file with the product. Net-SNMP allows users to add values to the MIB file and retrieve values from scripts, programs, and files.
- Net-SNMP is a natural fit with SL1's Dynamic Applications. Using Net-SNMP and dynamic applications, users can create reports, coupled graphs, and events based on the data points that are most useful to them.
Basic SNMP Terminology
This section defines some basic SNMP terminology. You should be familiar with the following terminology before installing and configuring Net-SNMP:
- SNMP (Simple Network Management Protocol). A set of standard protocols for managing diverse computer hardware and software within a TCP/IP network. SNMP is the most common network protocol used by network monitoring and management applications to exchange management information between devices. SL1 uses this protocol and other protocols to collect availability, performance, and configuration information.
SNMP uses a server-client structure. Clients are called agents. Devices and software that run SNMP are agents. The server is called the management system. SL1 is the management system.
Most enterprise-level network hardware is configured for SNMP and can be SNMP-enabled. Many enterprise software applications are also SNMP-compliant. When SNMP is running on a device, it uses a standard format to collect and store data about the device and/or software. For example, SNMP might collect information on each network interface and the traffic on each interface. SL1 can then query the device to retrieve the stored data.
- SNMP Tree. SNMP uses a tree structure. The first few branches of the tree are organizational and do not apply to specific manufacturers and device. The starting point for all device or application info is:
- 1.3.6.1.4.1.vendor_number
- For details on SNMP tree structure, see the SMI Network Management Private Enterprise Codes.
- For an overview of the entire SNMP tree, see http://www3.rad.com/networks/applications/snmp/main.htm.
- MIB (Management Information Base). A collection of objects that can be monitored by a network management system (in this case, SL1). The objects are organized hierarchically and stored in a MIB file. SNMP requires a standardized format for each MIB file. This standardized format allows SL1 to gather data on any device where SNMP is enabled. A MIB file is usually associated with a manufacturer and a device. Some companies use a single MIB that contains information on all their products; some manufacturers create a separate MIB for each product.
- OID (Object ID). OIDs are the numeric IDs that are used in the SNMP tree. OIDs are used to define manufacturers, devices, and the characteristics of devices. OIDs are defined and organized in MIB files.
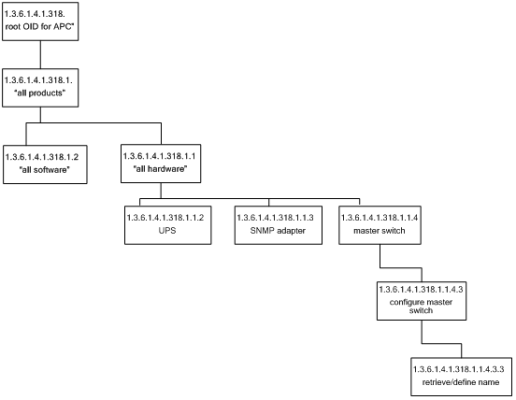
- In SL1, the root OID (sometimes called the vendor number) refers to the unique number assigned to each manufacturer. Each root OID is registered with IANA. For example, the root OID for American Power Conversion (APC) Corporation is 1.3.6.1.4.1.318. APC can then create and organize OIDs under this root OID. For example:
- 1.3.6.1.4.1.318 is the root OID for American Power Conversion Corporation.
- 1.3.6.1.4.1.318.1 could mean "all products". APC could then define unique IDs under “all products”.
- 1.3.6.1.4.1.318.1.1 could mean "hardware".
- 1.3.6.1.4.1.318.1.2 could mean "software".
All the OIDs that occur under 1.3.6.1.4.1.318.1.1 would be mapped to types of hardware, for example:
- 1.3.6.1.4.1.318.1.1.2 could mean "UPS".
- 1.3.6.1.4.1.318.1.1.3 could mean "SNMP adapter".
- 1.3.6.1.4.1.318.1.1.4 could mean "master switch".
All the OIDs that occur under each type of hardware (UPS, SNMP adapter, master switch) would be mapped to specific parameters that can be monitored and controlled through SNMP commands. For example:
- 1.3.6.1.4.1.318.1.1.4.3 could mean "configuration settings for master switch".
- 1.3.6.1.4.1.318.1.1.4.3.3 could mean "retrieve or define name for master switch".
The section of the SNMP tree for our example would look like this:
What is SSH?
Secure Shell (SSH) is a network protocol that enables users to securely access a command-line shell on a remote computer or server over an unsecured network. SSH provides strong encryption and authentication capabilities, making it an ideal method for securely administering commands or transferring data between a client and server.
To make SSH even more secure, you can use SSH keys instead of a simple password to log in to a server. SSH keys consist of two long strings of characters, called a public/private key pair, that are much less susceptible than passwords are to brute force attacks. The public key is placed on the server you want to access, while the private key resides on the client. When you use SSH to log in to the server from the client, the key pair is used to authenticate the session.
In SL1, some Dynamic Applications of type "Snippet" use SSH to communicate with a remote device. To use these Dynamic Applications, you must define an SSH credential. This credential specifies the hostname or IP address of the system you want to monitor, the port number used to access that system, and the private key used for authentication.
The default TCP port for SSH servers is 22.