This
Linux SSH Run Book Actions
The "Linux SSH Automations" PowerPack includes run book actions that use the "Execute Shell Commands" action type to retrieve diagnostic information or remediate an issue.
In the Input Parameters field for the "Execute Shell Commands" action type, you can specify the list of commands to run and their individual options. These can include the ID of an SSH/Key credential to use. The credential itself can have a specific host assigned to it, but a common configuration is for the action to run on the device or host where the triggering event occurred.
The following run book actions that use the "Execute Shell Commands" action type are included in the "Linux SSH Automations" PowerPack. For more information about the input parameter fields, see the table in Creating a Linux SSH Run Book Action.
| Action Name | Description | Commands Run |
|---|---|---|
|
Linux CPU Diagnostic Commands |
Runs diagnostic commands for CPU events. |
|
|
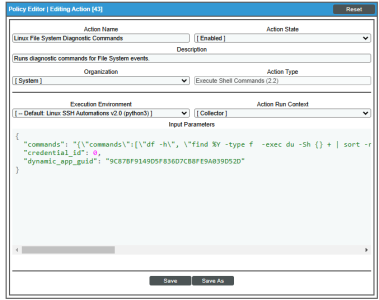
Linux File System Diagnostic Commands |
Runs diagnostic commands for File System events. |
|
|
Linux Illicit Process Remediation |
Collects a list of users logged in to the system and sends a term signal to a Linux process. |
|
|
Linux Interface Error/Discard Diagnostic Commands |
Runs diagnostic commands for Interface Error/Discard events. |
|
|
Linux Interface Utilization Diagnostic Commands |
Runs diagnostic commands for Interface Utilization events. |
|
|
Linux Memory Dmidecode Command |
Runs the dmidecode command with the memory option using sudo. |
|
|
Linux Memory/Swap Diagnostic Commands |
Runs diagnostic commands for Memory/Swap events. |
|
|
Linux Process Restart Remediation |
Restarts a Linux service and collects service status before and after the restart command. |
|
|
Linux System-Storage Diagnostic Commands |
Runs diagnostic commands for File System events. |
|
|
Linux Tcpdump Command |
Runs the tcpdump command using sudo. |
|
Creating a Custom Run Book Action Policy
You can use the "Execute Shell Commands" action type included with the "Linux SSH Automations" PowerPack to create custom run book actions that you can then use to build custom automation policies.
To create a custom action policy using the "Execute Shell Commands (2.2)" action type:
- Go to the Action Policy Manager page (Registry > Run Book > Actions).
- Click the button. The Action Editor page appears.
- In the Action Policy Editor page, supply a value in each field.
- Action Name. Specify the name for the action policy.
- Action State. Specifies whether the policy can be executed by an automation policy (Enabled) or cannot be executed (Disabled).
- Description. Allows you to enter a detailed description of the action.
- Organization. Organization to associate with the action policy.
- Action Type. Type of action that will be executed. Select the "Execute Shell Commands (2.2)" action type.
- Execution Environment. Select from the list of available Execution Environments. The default execution environment is System.
- Action Run Context. Select Database or Collector as the context in which the action policy will run.
- Input Parameters. A JSON structure that specifies each input parameter. Each parameter definition includes its name, data type, and whether the input is optional or required for this Custom Action Type. For more information about the input parameter fields, see the table in Creating a Linux SSH Run Book Action.
- Click [Save]. If you are modifying an existing action policy, click . Supply a new value in the Action Name field, and save the current action policy, including any edits, as a new policy.
Creating a Linux SSH Run Book Action
You can create a new run book action that runs SSH commands using the "Execute Shell Commands" custom action type. To do this, select "Execute Shell Commands (2.2)" in the Action Type drop-down list when you create a new run book action.
You can also use the existing run book actions in this PowerPack as a template by using the [Save As] option.
The Linux SSH run book actions accept the following parameters in JSON:
| Parameter | Input type | Description |
|---|---|---|
|
commands
|
string
|
Specifies a single command or a list of commands, in JSON format, to execute. You can use substitution variables in the commands. Example: "commands": "{\"commands\":[\"top -b -n 1\",\"ps -eo pid,ppid,%cpu,%mem,args --sort=-%cpu | head\",\"pidstat\",\"iostat -x 2 5\",\"dmesg | tail\"]}", ScienceLogic recommends that you make a copy of a run book action with the "Save As" button, and then rename the copy if you are modifying the list of commands in an existing run book action. |
|
credential_id
|
integer
|
Default value: 0 Specifies the credential_id to use for the connection.
|
|
dynamic_app_guid |
string |
Default value: The default value for this parameter corresponds to the globally unique ID number (GUID) value in the "Linux: Configuration Discovery" Dynamic Application. Specifies the GUID assigned to the Dynamic Application by Skylar One. You can specify multiple Dynamic Application IDs, separated by commas. If the credential_id parameter is not specified, Skylar One will use the dynamic_app_guid parameter to determine the credential. If this value is not specified, or if it is an empty string, Skylar One runs a query against the database to get the credential details. |
Using Substitution Values. The commands input can contain substitution values that match the keys in EM7_VALUES.
For more information about substitution variables, see Appendix A: Run Book Variables.
For a description of all options that are available in Automation Policies, see the
Configuring Linux Devices
If you have run book actions that use sudo in their commands, you will need to set up your user with passwordless sudo access on the Linux device being monitored.
For example, if your user is em7admin:
-
SSH to the Linux device.
-
Use the following format to create a new file for your user:
/etc/sudoers.d/<username>-user
For example:
sudo vi /etc/sudoers.d/em7admin-user
-
Add the following setting to the new file from step 2:
<username> ALL=(ALL) NOPASSWD:ALL
For example:
em7admin ALL=(ALL) NOPASSWD:ALL
-
Save the new file. New SSH logins will not ask for the sudo password, and the command and run books automations will run successfully.
Configuring Device Credentials
The "Execute Shell Commands" custom action type supports hard-coded credentials, where you specify the ID of a credential in the run book action. Alternately, the custom action type can dynamically determine the credential to use.
By default, the run book actions use the dynamic method by specifying credential ID 0 in the Input Parameters section. The dynamic method uses the first credential that matches the following rules:
- If the "Linux: Configuration Discovery" Dynamic Application from the "Linux Base Pack" PowerPack is aligned to the device associated with the triggering event, the credential aligned to that Dynamic Application is used.
- If none of the Dynamic Application GUIDs provided in the dynamic_app_guid list are aligned to the device associated with the triggering event, the first available SSH/Key credential aligned to the device as a secondary credential is used.
An SSH key is not required for an SSH/Key credential to work, and using a user/password pair in the credential is sufficient. You can set up the SSH key to suit your specific security requirements if needed.
Creating an SSH/Key Credential
If you already have the "Linux Base Pack" PowerPack installed and monitoring your Linux devices, you do not need to configure an additional credential.
If you do not have the "Linux Base Pack" PowerPack installed, you must create an SSH credential that includes the username and password, or username and private key, combination to communicate with your Linux devices.
To create a credential:
- Go to the Credentials page (Manage > Credentials).
- Click and select SSH/Key credential. The Create New SSH/Key Credential page appears.
- Supply values in the following fields:
- Name. Enter a name for the credential.
- All Organizations. Toggle on (blue) to align the credential to all organizations, or toggle off (gray) and then select one or more specific organizations from the Select the organizations drop-down field to align the credential with those specific organizations. This field is required.
- Timeout(ms). Enter a timeout, in milliseconds, for the connection.
- Hostname/IP. Hostname or IP address of the device from which you want to retrieve data.
- You can include the variable %D in this field. Skylar One will replace the variable with the IP address of the current device (device that is currently using the credential).
- You can include the variable %N in this field. Skylar One will replace the variable with hostname of the current device (device that is currently using the credential). If Skylar One cannot determine the hostname, Skylar One will replace the variable with the primary, management IP address for the current device.
- Port. To use SSH to connect to the device, enter "22" in this field.
- Username. Enter the username for an SSH user or user account on the device to be monitored.
- Password. Enter the password for the user you entered in the Username field.
- Private Key (PEM Format). Enter the SSH private key that you want Skylar One to use, in PEM format.
- Click .
For more information about configuring credentials in Skylar One, see Credentials.