You can use Skylar Compliance (formerly Restorepoint) to create policies to verify that your devices comply with corporate or regulatory guidelines.
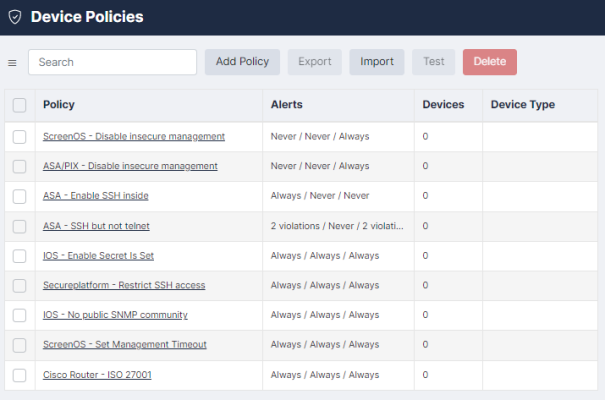
Device Policies
Use the Device Policies page (Compliance > Device Policies) to create configuration compliance policies and assign the policies to devices. Policies are groups of one or more rules. A rule is a pattern that is applied to configurations or device firmware version to test whether the configurations or firmware contain a certain phrase or Regular Expressions, or if they match an existing device template. If the tests fail, a compliance violation is triggered and an email alert is sent to the device owner.
Configuration Policies can be configured for devices that have a text configuration file or a TGZ archive of text configuration files.
Creating a Policy
To create a new policy:
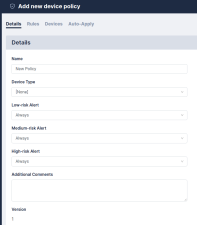
- Click to create a new policy or click to import a previously exported policy. The Add new device policy page appears.
- Enter the following details on the tab:
- Name. Type a name for the new device policy.
- Device Type. Select a device type from the drop-down field.
- Set the Alert. Choose which alert to set for your device policy.
Alert Criteria
Individual rules can be given a risk level, either Low , Medium or High. For each level, a trigger point can be set, to determine whether or not to generate an alert. This ranges from Never, through two, three, four, or five violations, to Always. For example, you may want an alert only if three or more low-risk rules are broken, but always if a single high-risk fails. You can also specify a Device Type that the policy will apply to, and add a Comment to explain the purpose of the policy.
If you want to copy an existing policy, open the existing policy and click Clone.
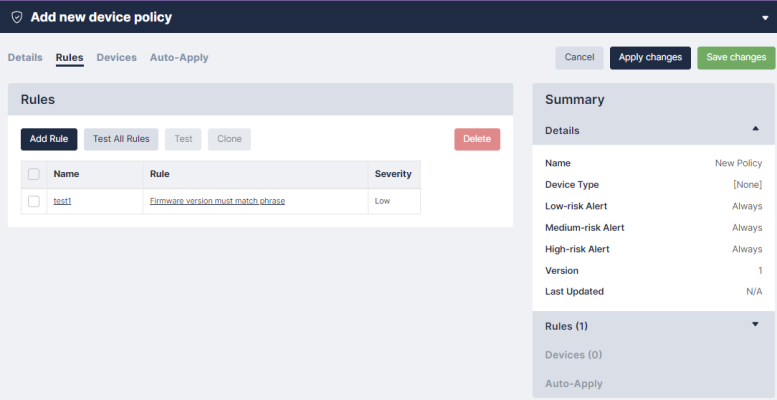
Rules Tab
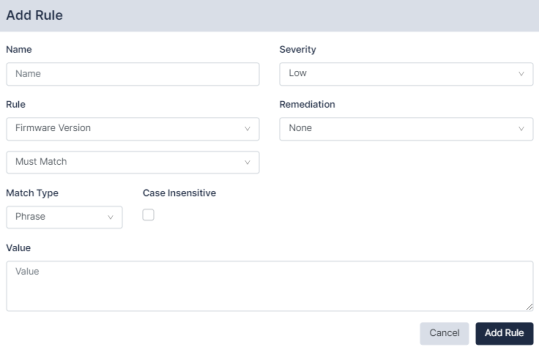
Click located in the Rules tab of the Add new device policy page to define and add a rule to a policy. Once a rule is defined, it can be edited, removed, cloned, or tested against an existing backup using the appropriate buttons. When finished, click .
Supply values in the following fields:
- Rule Name. A label that is used to identify a rule in a report or email.
- Rule Type. Whether the rule applies to a configuration, software version, runtime command, or the output of a scheduled action.
- Requirement. Select whether the rule Must Match or Must Not Match from the drop-down field.
- Match Type. Phrase, Regular Expressions, Lua function, device, or device templates. The Phrase match type matches any (case sensitive) number of characters, including multi-line. The Regex match type (see Regular Expressions) takes a Perl-flavoured regular expression, and applies it to the whole configuration, or firmware string.
- Severity. Select an alert level of None, Low, Medium, or High.
- Remediation Type. Select a remediation type of None, Manual, Automatic, or Command. For more information, see Remediation.
Remediation
You can use remediation when a compliance rule is not met, generally intended to rectify the violation. The following remediation types can be configured:
- Manual. The remediation text is appended to the notification email to signify that the recipient should take the appropriate action.
- Command. One of the stored Actions on the device is executed. For more information, see Device Control.
- Automatic. The text specified in the textbox is used as a command and executed on the device.
If the rule match type is Regex, the remediation can make use of the Capture feature, whereby parts of the pattern in brackets can be captured and then referred to in the remediation text (as $1, $2, etc.). For example, a rule may state that a configuration must not contain the regex:
set telnet (\d+\.\d+\.\d+\.\d+)
Where the command in brackets is a match for an IP address. If this rule is violated, the configuration can be remedied using the phrase:
unsettelnet$1
In this case, the brackets in the rule will capture the IP address, and apply it when the command is performed. The rule is then expanded:
unsettelnet1.2.3.4
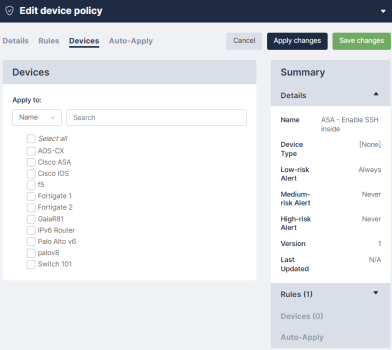
Devices Tab
Each policy can be assigned to, or removed from devices by selecting the relevant checkbox. Alternatively, this can be done from individual devices in the tab on the Edit Device policy page.
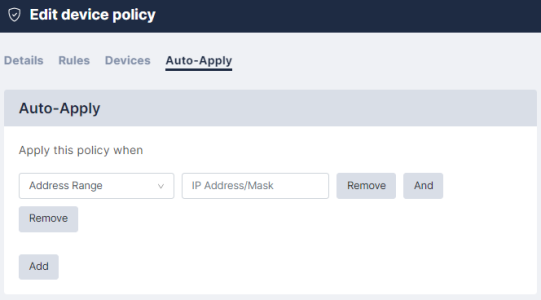
When your policy is assigned to, or removed from, its devices, you can choose when their policies should be applied. To apply the policies:
- Go to the tab (Compliance > Device Policies > your policy) . Choose an option from the Apply this policy when drop-down field to refine when a policy should be applied to a device that was created with Use Auto-Applied Rules
Regular Expressions
A regular expression specifies a set of strings as a pattern, rather than a list. For example, the pattern C(o|as?)t matches the strings Cot, Cat, and Cast, but not Coast. Skylar Compliance uses Perl-flavor Regular Expressions.
Most characters can be used in a regular expression. Some characters, called metacharacters, have special meanings:
- () denote grouping: (a|b)b matches ab and bb
- | denotes an alternative (see above)
- ^ matches the beginning of a line
- $matches the end of a line
- . matches any character
- + denotes one or more occurrences of the previous character: a+b matches ab, aab, abb, but not b
- * denotes zero or more occurrences of the previous character: a*b matches b, ab, aab, aaab
- ? denotes zero or one occurrences of the previous character: a?b matches b and ab, but not aab or aaab
Character classes are matches for sets of possible characters, rather than just a single character. For example:
- [bcr]at matches bat, cat and rat
- - can be used as a range operator in a character class. For example,[a-g] matches any character from a to g
There are some abbreviations for common character classes:
- \d matches a digit
- \s matches whitespace (a space or a tab)
- \w matches a word character (alphanumeric or a _)
For example, \d\d:\d\d:\d\d matches time in a hh:mm:ss format.
Lua Functions
You can use Skylar Compliance to define rules using Lua functions. For information on using Lua to run commands on your devices, see Lua Applets.
Available functions for compliance rules are:
- nextline() returns the next line of text
- getline(n) returns the given line of text
- numlines() returns the number of lines
- addmessage(m) allows you to replace a series of variables in the remediation text. For example, addmessage("Hello") with a remediation text of $1World! would output Hello World!. The next addmessage call would replace $2, and so on.
This function checks that the number of lines containing configure matches the lines containing port:
num1 = 0
num2 = 0
line, next = nextline()
while next do
if line:match("configure") then num1 = num1+1 end
if line:match("port") then num2 = num2+1 end
line, next = nextline()
end
if num1 > num2 then addmessage("more")
else if num2 < num1 then addmessage("less") end
return num1 == num2
Remediation Text: Config contains $1 configures than ports.
Variable Definitions
Items defined in this section can be used in compliance rules as variable replacements, referenced with the $replace$ format, where replace is the variable you have defined. This enables you to use a variable as shorthand for configuration elements, that are likely to be referenced multiple times.
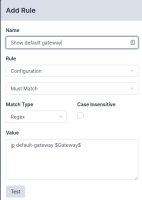
For example, if you create a definition for Gateway, and assign it a Value of 192.168.0.1, you can then use it in a compliance rule, as shown below:
This rule will be expanded to ip default-gateway 192.168.0.1. If the gateway address changes, update the Value in the Gateway variable definition and all rules that use the $Gateway$ variable will be automatically updated.
A variable name can only consist of letters, numbers, and the underscore character _. If the value contains escape sequences (such as \n), the sequence must be double-escaped (\\n).
Password Policies
You can use password policies to configure various rules to enforce password strength for devices and users. These settings are used in the strength meter that is displayed in all password fields : the background of the field will change color, from red for an unacceptable password, to yellow for a weak password, to green for a good password. Password Strength reports are available on the Reports page.
You can use the following rules for device passwords and user passwords:
- Minimum Length. Type a minimum number of characters for a password to be accepted.
- Good Length. Type a recommended number of characters to be considered good.
- Reject Common Passwords. Select this checkbox to reject easy-to-guess passwords, such as 1234 or password.
- Reject Dictionary Words. Select this checkbox to reject common words from the dictionary, such as backup or admin.
- Must Mix Case. Select this checkbox to require users to use mixed-case passwords.
- Must Include Numbers. Select this checkbox to require users to include numbers in their passwords.
- Must Include Symbols. Select this checkbox to require users to include symbols in their passwords.
- Expiration. User Passwords only. Type the number of days until the user passwords expires.
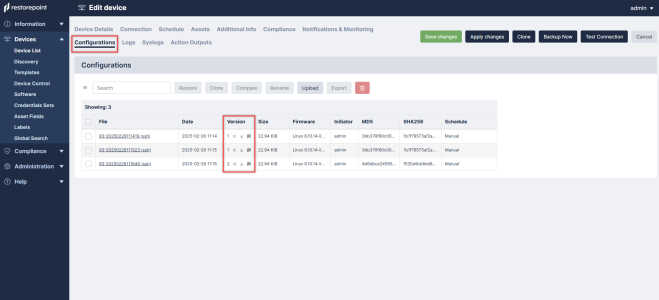
Configuration Baselines
Configuration versions can be marked as Baseline by the checkmark symbol in the Version column of the tab. When you perform subsequent backups, an email notification is sent if the configuration differs from a baseline version. This allows you to quickly check if the current configuration is an approved version.
- Go to the Devices page and select your device. The Edit Device page appears.
- Click the tab and set theBaseline toggle (
 ), Retention toggle (
), Retention toggle ( ), or Comment (
), or Comment ( ) for your device in the Version column.
) for your device in the Version column.- Baseline toggle on. If you use the (
 ), your configuration version will be marked as Baseline.
), your configuration version will be marked as Baseline. - Baseline toggle off. If you toggle to (
 ), your configuration is not Baseline.
), your configuration is not Baseline.
- Baseline toggle on. If you use the (